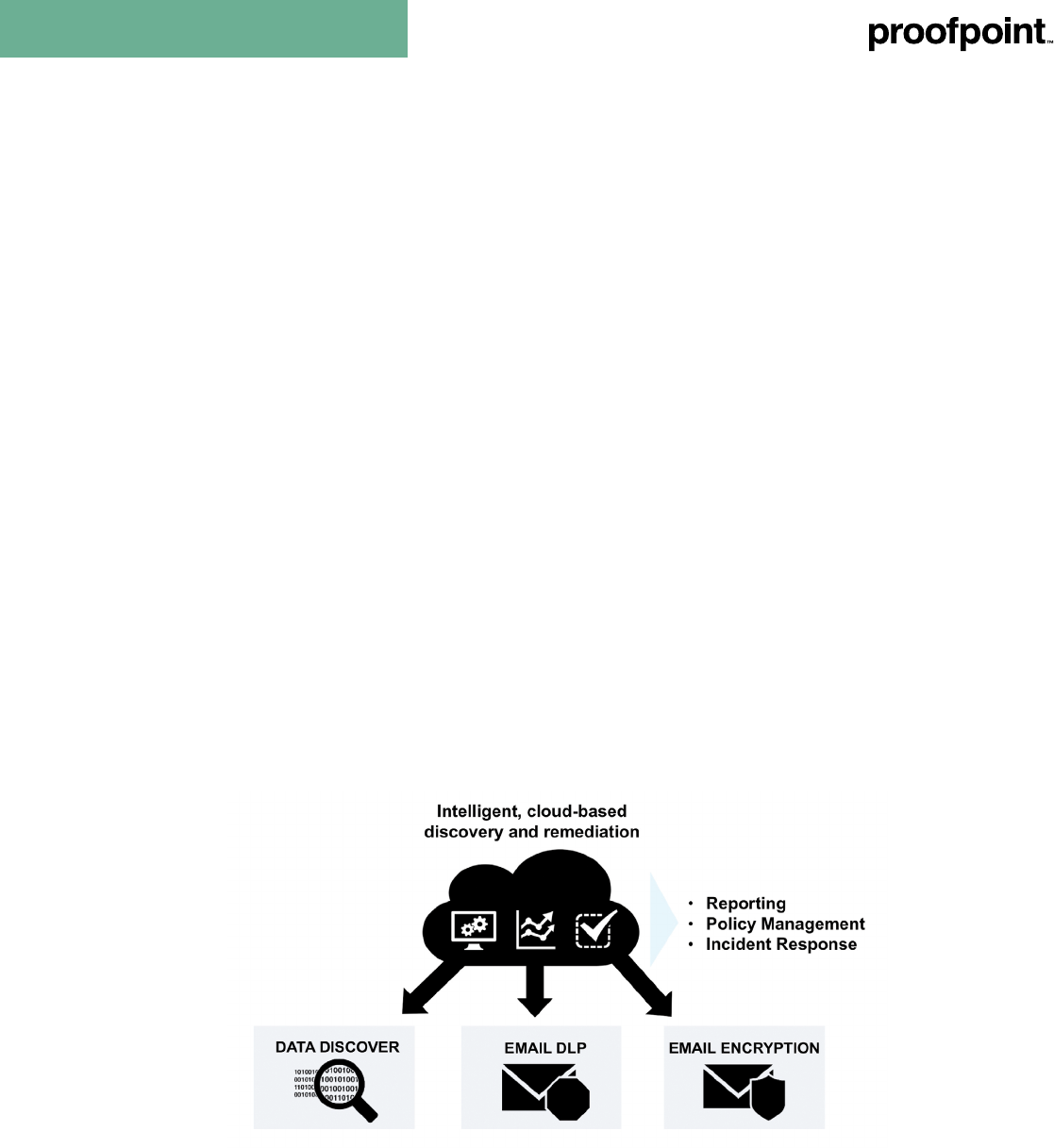
Proofpoint Information Protection
Find and protect your sensitive data, wherever it goes
Proofpoint Information Protection is the only cloud-based suite of solutions designed from the ground up to provide visibility
and control of sensitive data across cloud-based (i.e. Microsoft Ofce 365) or on-premises email, le shares, storage area
networks (SAN), network attached storage (NAS), and SharePoint — all with out-of-the-box policies that provide insight to
your attack surface in just 24 hours.
The suite includes:
• Proofpoint Data Discover: Quickly discover exposed sensitive and condential information in shared drives, NAS, SAN,
and SharePoint sites
• Proofpoint Email DLP: Prevent accidental negligence by employees with greater accuracy and control
• Proofpoint Email Encryption: Communicate securely with policy-based encryption of messages and attachments
Complete visibility and response for your unstructured enterprise data
Proofpoint provides dependable, automated content analysis to track information across your network, including:
• Email
• File shares
• Storage area networks
• Network attached storage
• SharePoint sites
No security posture is 100% effective against attackers. That is why IT teams must
proactively identify and protect sensitive and regulated data whether “at rest” in
le stores or “in motion” as it is sent or received. Proofpoint Information Protection
solutions reduce your attack surface and compliance risk by automatically classi-
fying sensitive data so that the people who need it—and only those people—have
access. Transparent policy enforcement and response protects your data without
interrupting your business processes.
Solution brief

ABOUT PROOFPOINT
Proofpoint, Inc. (NASDAQ:PFPT), a next-generation cybersecurity company, enables organizations to protect the way their people work today from advanced threats and compliance risks.
Proofpoint helps cybersecurity professionals protect their users from the advanced attacks that target them (via email, mobile apps, and social media), protect the critical information people
create, and equip their teams with the right intelligence and tools to respond quickly when things go wrong. Leading organizations of all sizes, including over 50 percent of the Fortune 100,
rely on Proofpoint solutions, which are built for today’s mobile and social-enabled IT environments and leverage both the power of the cloud and a big-data-driven analytics platform to
combat modern advanced threats.
proofpoint.com
© 2016 Proofpoint, Inc. Proofpoint is a trademark of Proofpoint, Inc. in the United States and other countries. All other trademarks contained herein are property of their respective owners.
Solution brief | Proofpoint information protection
You can automatically identify sensitive data—including PII, PHI, and PCI—at risk to exposure and enable real-time
remediation through quarantine, access revocation or deletion.
Automated regulatory compliance
Proofpoint provides dependable, automated content analysis to track information across your network, including:
• Electronic health records
• Condential design documents
• Cardholder information
• Other unstructured data
Policy-based encryption that end users love
Proofpoint Email Encryption makes secure communication simple, seamless, and automated. You can dynamically apply
policies based on message content, with encryption applied at the client or gateway levels. Proofpoint transparently
handles encryption key management and stores keys in secure, highly-available, and fully redundant facilities.
Cloud-based, rapid time-to-value
The time required to deploy traditional information protection solutions has been one of the biggest obstacles in
safeguarding business-critical data. Powered by a cloud-based platform, Proofpoint solutions deliver rapid deployment with
unprecedented time-to-value. You can deploy in just 90 minutes and realize benets in as fast as 24 hours.
One policy for multiple channels
Make the most of your investment in Proofpoint offerings. Our solutions share more than 80 policy templates—including
PCI, HIPAA, PII, and more. Custom policies can be created and extended to both data in motion and at rest.
Visualization for unstructured data at rest
Incident remediation queues are notorious for being more noise than insight. Data Discover solves this by providing tools,
including heat maps and exposure charts, to visualize where the organization is most vulnerable. For example, payment
credit industry (PCI) violations alone could overwhelm you with thousands of incidents. Data Discover can help by quickly
drilling into the specic PCI violations that affect your organization. These high value les are most likely to be exltrated by
threat actors in the event of a security compromise.
