
Junos® OS
CLI User Guide for Junos OS
Published
2024-07-12

Juniper Networks, Inc.
1133 Innovaon Way
Sunnyvale, California 94089
USA
408-745-2000
www.juniper.net
Juniper Networks, the Juniper Networks logo, Juniper, and Junos are registered trademarks of Juniper Networks, Inc.
in the United States and other countries. All other trademarks, service marks, registered marks, or registered service
marks are the property of their respecve owners.
Juniper Networks assumes no responsibility for any inaccuracies in this document. Juniper Networks reserves the right
to change, modify, transfer, or otherwise revise this publicaon without noce.
Junos® OS CLI User Guide for Junos OS
Copyright © 2024 Juniper Networks, Inc. All rights reserved.
The informaon in this document is current as of the date on the tle page.
YEAR 2000 NOTICE
Juniper Networks hardware and soware products are Year 2000 compliant. Junos OS has no known me-related
limitaons through the year 2038. However, the NTP applicaon is known to have some diculty in the year 2036.
END USER LICENSE AGREEMENT
The Juniper Networks product that is the subject of this technical documentaon consists of (or is intended for use
with) Juniper Networks soware. Use of such soware is subject to the terms and condions of the End User License
Agreement ("EULA") posted at hps://support.juniper.net/support/eula/. By downloading, installing or using such
soware, you agree to the terms and condions of that EULA.
ii

Table of Contents
About This Guide | xi
1
Overview
About the CLI Guide | 2
CLI Overview | 2
Introducing the Command-Line Interface | 3
CLI Modes, Commands, and Statement Hierarchies—An Overview | 5
Other Tools to Congure and Monitor Juniper Networks Devices | 7
Congure Junos OS in a FIPS Environment | 7
2
Geng Started
Geng Started: A Quick Tour of the CLI | 10
Get Started with the Command-Line Interface | 10
Switch Between Operaonal Mode and Conguraon Mode | 12
Use Keyboard Sequences to Navigate and Edit the CLI | 14
Congure a User Account on a Juniper Networks Device | 16
Use the CLI Editor in Conguraon Mode | 19
Check the Status of a Juniper Networks Device | 22
Roll Back Conguraon Changes | 25
Congure a Roung Protocol | 27
Shortcut | 28
Longer Conguraon | 28
Make Changes to a Roung Protocol Conguraon | 31
Online Help in the CLI | 35
Get Online Help from the Command-Line Interface | 35
CLI Online Help Features | 39
CLI Explorer Overview | 41
iii

CLI Environment Sengs | 42
Customize the CLI Environment | 42
Set the CLI Screen Length and Width | 46
Enable Conguraon Breadcrumbs | 47
3
Using Conguraon Statements to Congure a Device
CLI Conguraon Mode Overview | 51
Understanding CLI Conguraon Mode | 51
Enter and Exit CLI Conguraon Mode | 58
Relave Conguraon Mode Commands | 61
Command Compleon in Conguraon Mode | 61
Notaonal Convenons Used in Conguraon Hierarchies | 64
Overview of the Configure Command | 65
Forms of the configure Command | 65
How to Use the configure Command | 67
How to Use the configure exclusive Command | 68
How to Work with the Correct Conguraon | 71
Modify the Conguraon of a Device | 71
Display Users Currently Eding the Conguraon | 72
How to Modify the Juniper Networks Device Conguraon | 73
How to Add Conguraon Statements and Ideners | 75
How to Delete a Statement from a Device Conguraon | 76
Example: Delete a Statement from the Device Conguraon | 79
Copy a Statement in the Conguraon | 81
Example: Copy a Statement in the Conguraon | 81
Requirements | 81
Overview | 82
Conguraon | 82
iv

Example: Replace a Conguraon | 85
Requirements | 85
Overview | 85
Conguraon | 86
Insert a New Idener in a Device Conguraon | 92
Example: Insert a New Idener in a Device Conguraon | 92
Requirements | 93
Overview | 94
Conguraon | 94
Deacvate and Reacvate Statements and Ideners in a Device Conguraon | 97
Example: Deacvate and Reacvate Statements and Ideners in a Device Conguraon | 98
Requirements | 98
Overview | 98
Conguraon | 98
How to Make Global Changes in the Device Conguraon | 100
Common Regular Expressions to Use with the replace Command | 101
Example: How to Use Global Replace in a Device Conguraon—the \n Back Reference | 103
Requirements | 103
Overview | 104
Conguraon | 105
Example: Global Replace in a Device Conguraon—Replacing an Interface Name | 106
Requirements | 107
Overview | 107
Conguraon | 107
Example: Global Replace in a Device Conguraon—the upto Opon | 109
Add Comments in a Device Conguraon | 112
Add Comments in the CLI | 112
Add Comments in a File | 113
Example: Include Comments in a Device Conguraon by Using the CLI | 114
Requirements | 115
v

Overview | 115
Conguraon | 115
Example: Use the Wildcard Command with the Range Opon | 117
Requirements | 118
Overview | 118
Conguraon | 118
Use Conguraon Groups to Quickly Congure Devices | 127
Conguraon Groups Overview | 128
Congure Conguraon Groups | 129
Create a Conguraon Group | 129
How to Apply a Conguraon Group | 131
Example: Create and Apply Conguraon Groups | 132
Example: Disable Inheritance of a Conguraon Group | 134
Example: Use the junos-defaults Conguraon Group | 136
Example: Use Wildcards with Conguraon Groups | 139
How to Improve Commit Time When Using Conguraon Groups | 142
Example: Congure Sets of Statements with Conguraon Groups | 143
Example: Congure Interfaces Using Conguraon Groups | 144
Example: Use Conguraon Groups to Congure a Consistent IP Address for the Management
Interface | 147
Example: Use Conguraon Groups to Congure Peer Enes | 149
Example: Use Conguraon Groups to Establish Regional Conguraons | 151
Example: Congure Wildcard Conguraon Group Names | 152
Example: Reference the Preset Statement from the Defaults Group | 154
Example: View Default Statements That Have Been Applied to the Conguraon | 155
Set Up Roung Engine Conguraon Groups | 156
How to Use Condions to Apply Conguraon Groups | 158
vi

Example: Congure Condions for Applying Conguraon Groups | 159
Requirements | 159
Overview | 159
Conguraon | 160
View the Conguraon | 163
Display the Current Conguraon | 163
Example: Display the Current Conguraon | 164
Display Addional Informaon About the Conguraon | 166
Display set Commands from the Conguraon | 169
Verify the Device Conguraon | 173
Commit the Conguraon | 174
The Commit Model for Conguraons | 174
Commit a Device Conguraon | 176
Commit Operaon When Mulple Users Congure the Soware | 177
Commit Preparaon and Acvaon Overview | 178
Commit Device Conguraons in Two Steps: Preparaon and Acvaon | 180
Acvate a Device Conguraon with Conrmaon | 182
Schedule a Commit Operaon | 183
Monitor the Commit Process | 184
Add a Comment to Describe the Commied Conguraon | 186
Batch Commits Overview | 187
Example: Congure Batch Commit Server Properes | 188
Requirements | 188
Overview | 188
Conguraon | 189
Vericaon | 192
Back Up the Commied Conguraon on the Alternate Boot Drive | 199
4
Managing
Conguraons
vii

Conguraon Files Overview | 201
Conguraon Files Overview | 201
Device Conguraon Storage Overview | 203
Managing Conguraons | 203
The show | compare | display xml Command Output | 204
Returning to the Most Recently Commied Conguraon | 213
Returning to a Previously Commied Conguraon | 214
Example of Returning to a Previous Conguraon | 214
Example of Displaying Previous Conguraons | 214
About Comparing Conguraon Versions | 216
Using Conguraon Revision Ideners | 218
Saving a Conguraon to a File | 220
About Compressing the Current Conguraon File | 221
Free Up System Storage Space | 222
Clean Up Files with the CLI | 224
Autoinstallaon of Conguraon Files Overview | 226
Conguraon File Autoinstallaon—An Overview | 226
Conguring Autoinstallaon of Conguraon Files (CLI Procedure) | 229
Loading Conguraon Files | 231
Examples for Loading a Conguraon from a File or the Terminal | 232
How Character Encoding Works on Juniper Networks Devices | 235
About Specifying Statements and Ideners | 237
About Loading a Conguraon from a File | 241
Upload a Conguraon File | 245
Load JSON Conguraon Data With Unordered List Entries | 246
Back Up Conguraons to an Archive Site | 249
Congure the Transfer of the Acve Conguraon | 250
viii

Factory Default Conguraon Overview | 252
Restore the Default Factory Conguraon | 252
Rescue Conguraon | 253
Creang and Returning to a Rescue Conguraon | 253
Encrypt and Decrypt Conguraon Files | 255
Encrypt Conguraon Files | 255
Decrypt Conguraon Files | 257
Modify the Encrypon Key | 258
Example: Protecng the Junos OS Conguraon from Modicaon or Deleon | 259
Requirements | 259
Overview | 260
Protecng a Parent-Level Hierarchy | 260
Protecng a Child Hierarchy | 261
Protecng a Conguraon Statement Within a Hierarchy | 262
Protecng a List of Ideners for a Conguraon Statement | 263
Protecng an Individual Member from a Homogenous List | 264
Unprotecng a Conguraon | 265
Vericaon | 266
Synchronizing Conguraons Across Roung Engines | 270
Roung Engine Synchronizaon Overview | 270
Congure Mulple Roung Engines to Synchronize Commied Conguraons Automacally | 274
5
Using Operaonal Commands to Monitor Devices
CLI Operaonal Mode Overview | 278
CLI Operaonal Mode Command Overview | 278
Display Opons of the show Command—An Overview | 281
Interface Naming Convenons Used in Operaonal Commands | 282
About Group Interface Names Using Wildcard Characters | 284
ix

Using Operaonal Commands to Monitor a Device | 285
CLI Command Compleon Example | 286
Operaonal Mode Commands: Overview of Controlling the Scope | 287
Viewing Files and Directories on a Device | 289
Directories on the Device | 289
List Files and Directories | 290
Filenames and URLs | 293
Display Operang System Informaon | 295
Managing Programs and Processes Using Operaonal Mode Commands | 295
Show Soware Processes | 296
Restart the Soware Process | 297
Stop the Soware | 298
Reboot the Soware | 299
CLI Comment Character # for Operaonal Mode Commands | 300
Filtering Operaonal Command Output | 301
About Using the Pipe ( | ) Symbol to Filter Command Output | 301
Example: Use Regular Expressions with the Pipe ( | ) Symbol to Filter Command Output | 303
Example: Pipe ( | ) Filter Funcons in the Command-Line Interface | 304
Filter Operaonal Mode Command Output in a QFabric System | 318
Use Suppress-Zero Filter with the Pipe ( | ) Symbol to Filter Zero Values in Command Output | 319
6
Conguraon Statements and Operaonal Commands
Junos CLI Reference Overview | 324
x

About This Guide
The Junos OS command-line interface (CLI) is a command shell specic to Juniper Networks. This
command shell runs on top of the FreeBSD UNIX-based operang system kernel for Junos OS. Using
industry-standard tools and ulies, the CLI provides a powerful set of commands that you can use to
monitor and congure Juniper Networks devices running Junos OS. This guide contains informaon
about the CLI for Junos OS.
RELATED DOCUMENTATION
Day One: Exploring the Junos CLI
Day One: Junos for IOS Engineers
xi

About the CLI Guide
The Junos OS CLI Guide explains how to use the command-line interface (CLI). This guide also describes
advanced concepts and device conguraon when working with Juniper Networks devices running
Junos OS.
In this guide, you will learn about:
• Using conguraon statements to congure network devices
• Managing device conguraons
• Using operaonal commands to monitor devices
• Syntax for conguraon statements, operaonal commands, and environmental commands
For a basic introducon to Junos OS, see the Geng Started Guide for Junos OS. It provides a high-level
descripon of Junos OS, describes how to access devices, and provides simple step-by-step instrucons
for inial device conguraon.
For a technical and detailed exploraon of Junos OS, see the Overview for Junos OS. It further explains
how Junos OS works and describes the security, conguraon, monitoring, and management of network
devices.
Another useful learning resource is Day One: Exploring the Junos CLI.
CLI Overview
IN THIS SECTION
Introducing the Command-Line Interface | 3
CLI Modes, Commands, and Statement Hierarchies—An Overview | 5
Other Tools to Congure and Monitor Juniper Networks Devices | 7
Congure Junos OS in a FIPS Environment | 7
2

The CLI is the soware interface used to access your device. You use the CLI to congure the device,
monitor its operaons, and adjust the conguraon as needed. You access the CLI through a console
connecon interface or through a network connecon.
Introducing the Command-Line Interface
IN THIS SECTION
Key Features of the CLI | 3
The Junos OS CLI is a command shell
specic to Juniper Networks that runs on top of the operang
system kernel. Through industry-standard tools and ulies, the CLI provides a powerful set of
commands that you can use to monitor and to congure devices running Junos OS.
The CLI has two modes:
• Operaonal mode—Use this mode to display the current status of the device. In operaonal mode,
you enter commands to monitor and to troubleshoot the network operang system, devices, and
network connecvity.
• Conguraon mode—Use this mode to congure the device. In this mode, you enter statements to
congure all properes of the device, including interfaces, general roung informaon, roung
protocols, user access, and several system and hardware properes. Junos OS stores a conguraon
as a hierarchy of conguraon statements.
When you enter conguraon mode, you are viewing and changing a le called the
candidate
conguraon
. You use the candidate conguraon le, you make conguraon changes without
causing operaonal changes to the current operang conguraon, called the
acve conguraon
.
The device does not implement the changes you added to the candidate conguraon le unl you
commit the changes. Comming the conguraon changes acvates the revised conguraon on
the device. Candidate conguraons enable you to alter your conguraon without damaging your
current network operaons.
Key Features of the CLI
The CLI commands and statements follow a hierarchical organizaon and have a regular syntax. The CLI
provides the following features to simplify CLI use:
3
• Consistent command names—Commands that provide the same type of funcon have the same
name, regardless of the specic device type on which you are operang. For example, all show
commands display soware informaon and stascs, and all clear commands erase various types of
system informaon.
• Lists and short descripons of available commands—The CLI provides informaon about available
commands t each level of the command hierarchy. If you type a queson mark (?) at any level, you
see a list of the available commands along with a short descripon of each. This means that if you are
already familiar with Junos OS or with other roung soware, you can use many of the CLI
commands without referring to the documentaon.
• Command compleon—Command compleon for command names (keywords) and for command
opons is available at each level of the hierarchy. To complete a command or opon that you have
parally typed, press the Tab key or the Spacebar. If the parally typed leers begin a string that
uniquely idenes a command, the complete command name appears. Otherwise, a beep indicates
that you have entered an ambiguous command, and the CLI displays possible compleons.
Compleon also applies to other strings, such as lenames, interface names, usernames, and
conguraon statements.
If you have typed the mandatory arguments for execung a command in operaonal mode or
conguraon mode, the CLI displays <[Enter]> as one of the choices when you type a queson mark
(?). This output indicates that you have entered the mandatory arguments and can execute the
command at that level without specifying any further opons. Likewise, the CLI also displays <[Enter]>
when you reach a specic hierarchy level in the conguraon mode and do not need to enter any
more mandatory arguments or statements.
• Industry-standard technology—With FreeBSD UNIX as the kernel, a variety of UNIX ulies are
available on the CLI. For example, you can:
• Use regular expression matching to locate and to replace values and ideners in a conguraon,
to lter command output, and to examine log le entries.
• Use Emacs-based key sequences to move around on a command line and scroll through the
recently executed commands and command output.
• Store and archive Junos OS device les on a UNIX-based le system.
Use standard UNIX convenons to specify lenames and paths.
Exit the CLI environment and create a UNIX C shell or Bourne shell to navigate the le system,
manage router processes, and so on.
4

CLI Modes, Commands, and Statement Hierarchies—An Overview
IN THIS SECTION
CLI Command Hierarchy | 5
Conguraon Statement Hierarchy | 5
Move Among Hierarchy Levels | 6
The Junos OS CLI commands and statements are organized under two command modes and various
hierarchies. The following secons provide an overview of the CLI command modes and the command
and statement hierarchies.
CLI Command Hierarchy
CLI commands are organized in a hierarchy. Commands that perform a similar funcon are grouped
together under the same level of the hierarchy. For example, all commands that display informaon
about the system and the system soware are under the show system command. All commands that
display informaon about the roung table are under the show route command.
To execute a command, enter the full command name, starng at the top level of the hierarchy. For
example, to display a brief view of the routes in the roung table, use the command show route brief.
Conguraon Statement Hierarchy
The
conguraon statement
hierarchy has two types of statements:
Container statements
, which are
statements that contain other statements, and
leaf statements
, which do not contain other statements.
All the container statements and leaf statements together form the
conguraon hierarchy
.
The following illustraon shows a part of the hierarchy tree. The protocols statement is a top-level
statement at the trunk of the conguraon tree. The ospf, area, and interface statements are all
subordinate container statements of a higher statement; that is, they are branches of the hierarchy tree.
The hello-interval statement is a leaf on the tree.
Figure 1: Conguraon Statement Hierarchy Example
5

Move Among Hierarchy Levels
The following table shows the CLI commands you use to navigate the levels of the conguraon
statement hierarchy.
Table 1: CLI
Conguraon Mode Navigaon Commands
Command Descripon
edit
hierarchy-level
Moves to an exisng conguraon statement hierarchy or creates a hierarchy and moves
to that level.
exit
Moves up the hierarchy to the previous level where you were working. This command is,
in eect, the opposite of the edit command. Alternavely, you can use the quit command.
The exit command and the quit command are interchangeable.
up
Moves up the hierarchy one level at a me.
top
Moves directly to the top level of the hierarchy.
6

Other Tools to Congure and Monitor Juniper Networks Devices
Apart from the CLI, Junos OS also supports the following applicaons, scripts, and ulies that enable
you to congure and monitor Juniper Networks devices:
• J-Web GUI—Available on select Juniper Networks devices, the J-Web GUI enables you to monitor,
congure, troubleshoot, and manage the device by means of a browser with HTTP or HTTPS
enabled. For more informaon, see the
J-Web Interface User Guide
.
• Junos XML management protocol—The Junos XML management protocol enables you to monitor
and congure Juniper Networks devices. For more informaon, see the
Junos XML Management
Protocol Developer Guide
.
• NETCONF API—You can also use the NETCONF XML management protocol to monitor and
congure Juniper Networks devices. For more informaon, see the NETCONF XML Management
Protocol Developer Guide.
• Commit scripts and self-diagnosis features—You can dene scripts to enforce custom conguraon
rules, use commit script macros to provide simplied aliases for frequently used conguraon
statements, and congure diagnosc event policies and acons associated with each policy. For more
informaon, see the Junos OS Automaon Scripng User Guide.
• MIBs—You can use enterprise-specic and standard MIBS to retrieve informaon about the hardware
and soware components on a Juniper Networks device. For more informaon about MIBs, see the
Junos OS Network Management Administraon Guide for Roung Devices.
Congure Junos OS in a FIPS Environment
With Junos-FIPS you can congure a network of Juniper Networks devices in a FIPS 140-2
environment.
The Junos-FIPS soware environment requires the installaon of FIPS soware by a Crypto Ocer. In
Junos-FIPS, some Junos OS commands and statements have restricons and some addional
conguraon statements are available. For more informaon, see the following resources:
• Common Criteria and FIPS Cercaons—Provides links to guidelines for conguring Juniper
Networks devices so the secure environment complies with the requirements of public sector
cercaons such as Common Criteria and FIPS cercaon.
• Compliance Advisor—A Web applicaon that provides regulatory compliance informaon about
Common Criteria, FIPS, Homologaon, ROHS2, and USGv6 for Juniper Networks products.
7

Geng Started: A Quick Tour of the CLI
IN THIS SECTION
Get Started with the Command-Line Interface | 10
Switch Between Operaonal Mode and Conguraon Mode | 12
Use Keyboard Sequences to Navigate and Edit the CLI | 14
Congure a User Account on a Juniper Networks Device | 16
Use the CLI Editor in Conguraon Mode | 19
Check the Status of a Juniper Networks Device | 22
Roll Back Conguraon Changes | 25
Congure a Roung Protocol | 27
The following topics can help you (the network administrator) get started with the Junos OS CLI to
perform conguraon changes, switch between operaonal mode and conguraon mode, create a user
account, and execute some of the basic commands.
NOTE: If you need a basic introducon to Junos OS, see the Geng Started Guide for Junos OS.
For more in-depth informaon, as well as to learn how to use Junos OS with Juniper Networks
devices, see the Overview for Junos OS.
This Junos OS CLI Guide assumes that you are familiar with Junos OS concepts and operaon
principles.
Get Started with the Command-Line Interface
This topic shows you how to start the Junos OS CLI, view the command hierarchy, and make minor
conguraon changes.
10

NOTE: Before you begin, make sure that your device hardware is set up and Junos OS is
installed. You must have a direct console connecon to the device or network access using SSH
or Telnet. If your device is not set up, follow the installaon instrucons provided with the device
before proceeding.
To log in to a device and start the CLI:
1. Log in as root.
The root login account has superuser privileges, with access to all commands and statements.
2. Start the CLI:
root# cli
root@>
The > command prompt shows that you are in operaonal mode. Later, when you enter conguraon
mode, the prompt will change to #.
NOTE: If you are using the root account for the rst me on the device, remember that the
device ships with no password required for root. The rst me you commit a conguraon, you
must set a root password. Root access is not allowed over a telnet session. To enable root access
over an SSH connecon, you must congure the system services ssh root-login allow statement.
CLI commands can vary by plaorm and soware release. The CLI includes several ways to get help
about available commands. This secon demonstrates some examples showing how to get help:
1. Type ? to show the top-level commands available in operaonal mode.
root@> ?
Possible completions:
clear Clear information in the system
configure Manipulate software configuration information
diagnose Invoke diagnose script
file Perform file operations
help Provide help information
monitor Show real-time debugging information
mtrace Trace multicast path from source to receiver
ping Ping remote target
quit Exit the management session
11

request Make system-level requests
restart Restart software process
set Set CLI properties, date/time, craft interface message
show Show system information
ssh Start secure shell on another host
start Start shell
telnet Telnet to another host
test Perform diagnostic debugging
traceroute Trace route to remote host
2. Type file ? to show all possible compleons for the file command.
root@> file ?
Possible completions:
<[Enter]> Execute this command
archive Archives files from the system
checksum Calculate file checksum
compare Compare files
copy Copy files (local or remote)
delete Delete files from the system
list List file information
rename Rename files
show Show file contents
source-address Local address to use in originating the connection
| Pipe through a command
3. Type file archive ? to show all possible compleons for the file archive command.
root@> file archive ?
Possible completions:
compress Compresses the archived file using GNU gzip (.tgz)
destination Name of created archive (URL, local, remote, or floppy)
source Path of directory to archive
Switch Between Operaonal Mode and Conguraon Mode
When you monitor and congure a device running Junos OS, you may need to switch between modes .
When you switch between operaonal mode and conguraon mode, the command prompt also
12

changes. The operaonal mode prompt is a right-angle bracket (>). The conguraon mode prompt is a
pound or hash sign (#).
To switch between operaonal mode and conguraon mode:
1. When you log in to the device and type the cli command and press Enter, you are automacally in
operaonal mode:
---JUNOS 17.2B1.8 built 2018-05-09 23:41:29 UTC
% cli
user@host>
2. To enter conguraon mode, type the configure command or the edit command in CLI operaonal
mode. The prompt in brackets ([edit]), also known as a
banner
, shows that you are in conguraon
mode at the top of the hierarchy. For example:
user@host> configure
Entering configuration mode
[edit]
user@host#
The CLI prompt changes from user@host> to user@host#, showing that you are in conguraon mode,
and a banner appears to indicate the hierarchy level.
3. You can exit conguraon mode and return to operaonal mode in one of the following ways:
• To commit the conguraon and exit:
[edit]
user@host# commit and-quit
commit complete
Exiting configuration mode
user@host>
• To exit without comming:
[edit]
user@host# exit
13

Exiting configuration mode
user@host>
When you exit conguraon mode, the CLI prompt changes from user@host# to user@host>, and the
banner no longer appears. You can enter or exit conguraon mode as many mes as you wish
without comming your changes.
4. To display the output of an
operaonal mode command
such as show while in conguraon mode,
issue the run conguraon mode command. Then, specify the operaonal mode command:
[edit]
user@host# run
operational-mode-command
For example, to display the currently set priority value of the Virtual Router Redundancy Protocol
(VRRP) primary device while you are modifying the VRRP conguraon for a backup device:
[edit interfaces xe-4/2/0 unit 0 family inet vrrp-group 27]
user@host# show
virtual-address [ 192.168.1.15 ];
[edit interfaces xe-4/2/0 unit 0 family inet vrrp-group 27]
user@host# run show vrrp detail
Physical interface: xe-5/2/0, Unit: 0, Address: 192.168.29.10/24
Interface state: up, Group: 10, State: backup
Priority: 190, Advertisement interval: 3, Authentication type: simple
Preempt: yes, VIP count: 1, VIP: 192.168.29.55
Dead timer: 8.326, Master priority: 201, Master router: 192.168.29.254
[edit interfaces xe-4/2/0 unit 0 family inet vrrp-group 27]
user@host# set priority ...
Use Keyboard Sequences to Navigate and Edit the CLI
You can use keyboard sequences in the Junos OS CLI to navigate and edit the command line. You can
also use keyboard sequences to scroll through a list of recently executed commands. The following table
lists some of the CLI keyboard sequences. They are the same as those used in Emacs.
14

Table 2: CLI Keyboard Shortcuts
Keyboard sequence Acon
Ctrl+b Move the cursor back one character.
Esc+b or Alt+b Move the cursor back one word.
Ctrl+f Move the cursor forward one character.
Esc+f or Alt+f Move the cursor forward one word.
Ctrl+a Move the cursor to the beginning of the command line.
Ctrl+e Move the cursor to the end of the command line.
Ctrl+h, Delete,
or Backspace
Delete the character before the cursor.
Ctrl+d Delete the character at the cursor.
Ctrl+k Delete the all characters from the cursor to the end of the command line.
Ctrl+u or Ctrl+x Delete the all characters from the command line.
Ctrl+w, Esc+Backspace,
or Alt+Backspace
Delete the word before the cursor.
Esc+d or Alt+d Delete the word aer the cursor.
Ctrl+y Insert the most recently deleted text at the cursor.
Ctrl+l Redraw the current line.
Ctrl+p Scroll backward through the list of recently executed commands.
15

Table 2: CLI Keyboard Shortcuts
(Connued)
Keyboard sequence Acon
Ctrl+n Scroll forward through the list of recently executed commands.
Ctrl+r Search the CLI history incrementally in reverse order for lines matching the search
string.
Esc+/ or Alt+/ Search the CLI history for words for which the current word is a prex.
Esc+. or Alt+. Scroll backward through the list of recently entered words in a command line.
Esc+
number
sequence
or Alt+
number
sequence
Specify the number of mes to execute a keyboard sequence.
Congure a User Account on a Juniper Networks Device
This topic describes how to use a root account to log in to a Juniper Networks device and congure a
new user account. You can congure an account for your own use or create a test account.
To congure a new user account on the device:
1. Log in as root and enter conguraon mode:
root@host> configure
[edit]
root@host#
The ([edit]) prompt banner shows that you are in conguraon edit mode at the top of the
hierarchy.
2.
Change to the [edit system login] secon of the conguraon:
[edit]
root@host# edit system login
16

[edit system login]
root@host#
The prompt in brackets changes to [edit system login] to show that you are at a new level in the
hierarchy.
3. Now add a new user account. In the example, user1 represents a username:
[edit system login]
root@host# edit user user1
This example adds an account user1.
NOTE: User account names can contain a period (.). For example, you can have a user
account user.1. However, the username cannot begin or end with a period.
4. Congure a full name for the account. If the name includes spaces, enclose the enre name in
quotaon marks (" "):
[edit system login user user1]
root@host# set full-name "User One"
5. Congure an account class. The account class sets the user access privileges for the account:
[edit system login user user1]
root@host# set class super-user
6. Congure an authencaon method and password for the account:
[edit system login user user1]
root@host# set authentication plain-text-password
New password:
Retype new password:
When the new password prompt appears, enter a clear-text password that the system can encrypt,
and then conrm the new password.
17

7. Commit the conguraon:
[edit system login user user1]
root@host# commit
commit complete
Conguraon changes are not acve unl you commit the conguraon. If the commit is
successful, a commit complete message appears.
8. Return to the top level of the conguraon, and then exit:
[edit system login user user1]
root@host# top
[edit]
root@host# exit
Exiting configuration mode
9. Log out of the device:
root@host> exit
% logout Connection closed.
10. To test your changes, log back in with the user account and password you just congured:
login: user1
Password:
password
---JUNOS 17.2B1.8 built 2018-05-09 23:41:29 UTC
user1@host>
When you log in, you should see the new username at the command prompt.
You have successfully used the CLI to view the device status and perform a simple conguraon change.
NOTE: For complete informaon about the commands to issue to congure your device,
including examples, see the Junos OS conguraon guides.
18

Use the CLI Editor in Conguraon Mode
This topic describes basic commands that you can use to enter conguraon mode in the CLI editor. The
topic also describes commands that you use to navigate the conguraon hierarchy, get help, and
commit or revert the changes that you make during the conguraon session.
Task Command/
Statement
Example
Edit Your Conguraon
Enter conguraon mode.
When you start the CLI, the device is
in operaonal mode. You must
explicitly enter conguraon mode.
When you do, the CLI prompt changes
from user@host> to user@host#, and the
hierarchy level appears in square
brackets.
configure
user@host> configure
[edit]
user@host#
Create a statement hierarchy.
You can use the edit command to
simultaneously create a hierarchy and
move to that new level in the
hierarchy. You cannot use the edit
command to change the value of
ideners.
edit
hierarchy-
level value
[edit]
user@host# edit security zones security-zone myzone
[edit security zones security-zone myzone]
user@host#
Create a statement hierarchy, and set
idener values.
The set command is like edit, except
that your current level in the hierarchy
does not change.
set
hierarchy-
level value
[edit]
user@host# set security zones security-zone myzone
[edit]
user@host#
Navigate the Hierarchy
19

(Connued)
Task Command/
Statement
Example
Navigate down to an exisng
hierarchy level.
edit
hierarchy-
level
[edit]
user@host# edit security zones
[edit security zones]
user@host#
Navigate up one level in the hierarchy.
up [edit security zones]
user@host# up
[edit security]
user@host#
Navigate to the top of the hierarchy.
top [edit security zones]
user@host# top
[edit]
user@host#
Commit or Revert Changes
Commit your conguraon.
commit [edit]
user@host# commit
commit complete
20

(Connued)
Task Command/
Statement
Example
Roll changes back from the current
session.
Use the rollback command to revert all
changes from the current
conguraon session. When you run
the rollback command before you exit
your session or commit changes, the
soware loads the most recently
commied conguraon onto the
device. You must enter the rollback
statement at the edit level in the
hierarchy.
rollback [edit]
user@host# rollback
load complete
Exit Conguraon Mode
Commit the conguraon, and exit
conguraon mode.
commit and-quit [edit]
user@host# commit and-quit
user@host>
Exit conguraon mode without
comming your conguraon.
You must navigate to the top of the
hierarchy using the up or top
commands before you can exit
conguraon mode.
exit [edit]
user@host# exit
The configuration has been changed but not
committed
Exit with uncommitted changes? [yes,no] (yes)
Get Help
21

(Connued)
Task Command/
Statement
Example
Display a list of valid opons for the
current hierarchy level.
? [edit ]
user@host# edit security zones ?
Possible completions:
<[Enter]> Execute this command
> functional-zone Functional zone
> security-zone Security zones
| Pipe through a
command
[edit]
SEE ALSO
Understanding CLI Conguraon Mode | 51
Check the Status of a Juniper Networks Device
In operaonal mode, you can use show commands to check the status of the device and monitor the
acvies on the device.
To help you become familiar with show commands:
• Type show ? to display the list of show commands you can use to monitor the router:
root@> show ?
Possible completions:
accounting Show accounting profiles and records
aps Show Automatic Protection Switching information
arp Show system Address Resolution Protocol table entries
as-path Show table of known autonomous system paths
bfd Show Bidirectional Forwarding Detection information
22

bgp Show Border Gateway Protocol information
chassis Show chassis information
class-of-service Show class-of-service (CoS) information
cli Show command-line interface settings
configuration Show current configuration
connections Show circuit cross-connect connections
dvmrp Show Distance Vector Multicast Routing Protocol info
dynamic-tunnels Show dynamic tunnel information information
esis Show end system-to-intermediate system information
firewall Show firewall information
helper Show port-forwarding helper information
host Show hostname information from domain name server
igmp Show Internet Group Management Protocol information
ike Show Internet Key Exchange information
ilmi Show interim local management interface information
interfaces Show interface information
ipsec Show IP Security information
ipv6 Show IP version 6 information
isis Show Intermediate System-to-Intermediate System info
l2circuit Show Layer 2 circuit information
l2vpn Show Layer 2 VPN information
lacp Show Link Aggregation Control Protocol information
ldp Show Label Distribution Protocol information
link-management Show link management information
llc2 Show LLC2 protocol related information
log Show contents of log file
mld Show multicast listener discovery information
mpls Show Multiprotocol Label Switching information
msdp Show Multicast Source Discovery Protocol information
multicast Show multicast information
ntp Show Network Time Protocol information
ospf Show Open Shortest Path First information
ospf3 Show Open Shortest Path First version 3 information
passive-monitoring Show information about passive monitoring
pfe Show Packet Forwarding Engine information
pgm Show Pragmatic Generalized Multicast information
pim Show Protocol Independent Multicast information
policer Show interface policer counters and information
policy Show policy information
ppp Show PPP process information
rip Show Routing Information Protocol information
ripng Show Routing Information Protocol for IPv6 info
route Show routing table information
23

rsvp Show Resource Reservation Protocol information
sap Show Session Announcement Protocol information
security Show security information
services Show services information
snmp Show Simple Network Management Protocol information
system Show system information
task Show routing protocol per-task information
ted Show Traffic Engineering Database information
version Show software process revision levels
vpls Show VPLS information
vrrp Show Virtual Router Redundancy Protocol information
• Use the show chassis routing-engine command to view the Roung Engine status:
root@> show chassis routing-engine
Routing Engine status:
Slot 0:
Current state Master
Election priority Master (default)
Temperature 31 degrees C / 87 degrees F
CPU temperature 32 degrees C / 89 degrees F
DRAM 768 MB
Memory utilization 84 percent
CPU utilization:
User 0 percent
Background 0 percent
Kernel 1 percent
Interrupt 0 percent
Idle 99 percent
Model RE-2.0
Serial ID b10000078c10d701
Start time 2005-12-28 13:52:00 PST
Uptime 12 days, 3 hours, 44 minutes, 19 seconds
Load averages: 1 minute 5 minute 15 minute
0.02 0.01 0.00
•
Use the show system storage command to view available storage on the device:
root@> show system storage
Filesystem Size Used Avail Capacity Mounted on
24

/dev/ad0s1a 865M 127M 669M 16% /
devfs 1.0K 1.0K 0B 100% /dev
devfs 1.0K 1.0K 0B 100% /dev/
/dev/md0 30M 30M 0B 100% /packages/mnt/jbase
/dev/md1 158M 158M 0B 100% /packages/mnt/jkernel-9.3B1.5
/dev/md2 16M 16M 0B 100% /packages/mnt/jpfe-M7i-9.3B1.5
/dev/md3 3.8M 3.8M 0B 100% /packages/mnt/jdocs-9.3B1.5
/dev/md4 44M 44M 0B 100% /packages/mnt/jroute-9.3B1.5
/dev/md5 12M 12M 0B 100% /packages/mnt/jcrypto-9.3B1.5
/dev/md6 25M 25M 0B 100% /packages/mnt/jpfe-common-9.3B1.5
/dev/md7 1.5G 196K 1.4G 0% /tmp
/dev/md8 1.5G 910K 1.4G 0% /mfs
/dev/ad0s1e 96M 38K 88M 0% /config
procfs 4.0K 4.0K 0B 100% /proc
/dev/ad1s1f 17G 2.6G 13G 17% /var
SEE ALSO
Managing Programs and Processes Using Operaonal Mode Commands | 295
Viewing Files and Directories on a Device | 289
Roll Back Conguraon Changes
This topic shows how to use the rollback command to return your uncommied but revised
conguraon to the state of the most recently commied Junos OS conguraon. The rollback
command is useful if you make conguraon changes and then decide not to keep them.
The following procedure shows how to congure an SNMP health monitor on a Juniper Networks
device and then return to the most recently commied conguraon that does not include the health
monitor. When congured, the SNMP health monitor provides the network management system (NMS)
with predened monitoring for le system usage, CPU usage, and memory usage on the device.
1. Enter conguraon mode:
user@host> configure
entering configuration mode
[edit]
user@host#
25

2. Show the current conguraon (if any) for SNMP:
[edit]
user@host# show snmp
No snmp statements appear because SNMP has not been congured on the device.
3. Congure the health monitor:
[edit]
user@host# set snmp health-monitor
4. Show the new conguraon:
[edit]
user@host# show snmp
health-monitor;
The health-monitor statement indicates that SNMP health monitoring is congured on the device.
5. Enter the rollback conguraon mode command to return to the most recently commied
conguraon:
[edit]
user@host# rollback
load complete
6. Show the conguraon again to make sure your change is no longer present:
[edit]
user@host# show snmp
No snmp conguraon statements appear. The health monitor is no longer congured.
7.
Enter the commit command to acvate the conguraon to which you rolled back:
[edit]
user@host# commit
26

8. Exit conguraon mode:
[edit]
user@host# exit
Exiting configuration mode
You can also use the rollback command to return to earlier conguraons.
SEE ALSO
Returning to the Most Recently Commied Conguraon | 213
Congure a Roung Protocol
IN THIS SECTION
Shortcut | 28
Longer Conguraon | 28
Make Changes to a Roung Protocol Conguraon | 31
This topic provides a sample conguraon that describes how to congure an OSPF backbone area that
has two SONET interfaces.
The nal conguraon looks like this:
[edit]
protocols {
ospf {
area 0.0.0.0 {
interface so-0/0/0 {
hello-interval 5;
dead-interval 20;
}
interface so-0/0/1 {
27

hello-interval 5;
dead-interval 20;
}
}
}
}
Shortcut
You can create a shortcut for this enre conguraon with the following two commands:
[edit]
user@host# set protocols ospf area 0.0.0.0 interface so-0/0/0 hello-interval 5 dead-interval 20
[edit]
user@host# set protocols ospf area 0.0.0.0 interface so-0/0/1 hello-interval 5 dead-interval 20
Longer Conguraon
This secon provides a longer example of creang the previous OSPF conguraon. In the process, it
illustrates how to use the dierent features of the CLI.
1. Enter conguraon mode by issuing the configure command:
user@host> configure
entering configuration mode
[edit]
user@host#
Noce that the prompt has changed to a pound or hash sign (#) to indicate conguraon mode.
2. To create the above conguraon, you start by eding the protocols ospf statements:
[edit]
user@host# edit protocols ospf
[edit protocols ospf]
user@host#
3. Now add the OSPF area:
[edit protocols ospf]
user@host# edit area 0.0.0.0
28

[edit protocols ospf area 0.0.0.0]
user@host#
4. Add the rst interface:
[edit protocols ospf area 0.0.0.0]
user@host# edit interface so-0/0/0
[edit protocols ospf area 0.0.0.0 interface so-0/0/0]
user@host#
You now have four nested statements.
5. Set the hello and dead intervals.
[edit protocols ospf area 0.0.0.0 interface so-0/0/0]
user@host# set hello-interval 5
user@host# set dead-interval 20
user@host#
6. You can see what is congured at the current level with the show command:
[edit protocols ospf area 0.0.0.0 interface so-0/0/0]
user@host# show
hello-interval 5;
dead-interval 20;
[edit protocols ospf area 0.0.0.0 interface so-0/0/0]
user@host#
7. You are nished at this level, so go up a level and view what you have done so far:
[edit protocols ospf area 0.0.0.0 interface so-0/0/0]
user@host# up
[edit protocols ospf area 0.0.0.0]
user@host# show
interface so-0/0/0 {
hello-interval 5;
dead-interval 20;
}
[edit protocols ospf area 0.0.0.0]
user@host#
29

The interface statement appears because you have moved to the area statement.
8. Add the second interface:
[edit protocols ospf area 0.0.0.0]
user@host# edit interface so-0/0/1
[edit protocols ospf area 0.0.0.0 interface so-0/0/1]
user@host# set hello-interval 5
[edit protocols ospf area 0.0.0.0 interface so-0/0/1]
user@host# set dead-interval 20
[edit protocols ospf area 0.0.0.0 interface so-0/0/1]
user@host# up
[edit protocols ospf area 0.0.0.0]
user@host# show
interface so-0/0/0 {
hello-interval 5;
dead-interval 20;
}
interface so-0/0/1 {
hello-interval 5;
dead-interval 20;
}
[edit protocols ospf area 0.0.0.0]
user@host#
9. Move up to the top level and review what you have:
[edit protocols ospf area 0.0.0.0]
user@host# top
[edit]
user@host# show
protocols {
ospf {
area 0.0.0.0 {
interface so-0/0/0 {
hello-interval 5;
dead-interval 20;
}
interface so-0/0/1 {
hello-interval 5;
dead-interval 20;
}
30

}
}
}
[edit]
user@host#
This conguraon now contains the statements that you want.
10. Before comming the conguraon (and thereby acvang it), verify that the conguraon is
correct:
[edit]
user@host# commit check
configuration check succeeds
[edit]
user@host#
11. Commit the conguraon to acvate it on the device:
[edit]
user@host# commit
commit complete
[edit]
user@host#
Make Changes to a Roung Protocol Conguraon
Suppose you decide to use dierent dead intervals and hello intervals on interface so-0/0/1. You can
make changes to the conguraon.
1. Go directly to the appropriate hierarchy level by typing the full hierarchy path to the statement that
you want to edit:
[edit]
user@host# edit protocols ospf area 0.0.0.0 interface so-0/0/1
[edit protocols ospf area 0.0.0.0 interface so-0/0/1]
user@host# show
hello-interval 5;
dead-interval 20;
[edit protocols ospf area 0.0.0.0 interface so-0/0/1]
user@host# set hello-interval 7
[edit protocols ospf area 0.0.0.0 interface so-0/0/1]
31

user@host# set dead-interval 28
[edit protocols ospf area 0.0.0.0 interface so-0/0/1]
user@host# top
[edit]
user@host# show
protocols {
ospf {
area 0.0.0.0 {
interface so-0/0/0 {
hello-interval 5;
dead-interval 20;
}
interface so-0/0/1 {
hello-interval 7;
dead-interval 28;
}
}
}
}
[edit]
user@host#
2. If you decide not to run OSPF on the rst interface, delete the statement:
[edit]
user@host# edit protocols ospf area 0.0.0.0
[edit protocols ospf area 0.0.0.0]
user@host# delete interface so-0/0/0
[edit protocols ospf area 0.0.0.0]
user@host# top
[edit]
user@host# show
protocols {
ospf {
area 0.0.0.0 {
interface so-0/0/1 {
hello-interval 7;
dead-interval 28;
}
}
}
}
32

[edit]
user@host#
Everything inside the statement you deleted was deleted with it. You can also eliminate the enre
OSPF conguraon by simply entering delete protocols ospf while at the top level.
3. Maybe you decide to use the default values for the hello intervals and dead intervals on your
remaining interface but want OSPF to run on that interface. In that case, delete the hello interval
mer and dead interval mer:
[edit]
user@host# edit protocols ospf area 0.0.0.0 interface so-0/0/1
[edit protocols ospf area 0.0.0.0 interface so-0/0/1]
user@host# delete hello-interval
[edit protocols ospf area 0.0.0.0 interface so-0/0/1]
user@host# delete dead-interval
[edit protocols ospf area 0.0.0.0 interface so-0/0/1]
user@host# top
[edit]
user@host# show
protocols {
ospf {
area 0.0.0.0 {
interface so-0/0/1;
}
}
}
[edit]
user@host#
You can set mulple statements at the same me as long as they are all part of the same hierarchy.
The hierarchy consists of the path of statements from the top inward, as well as one or more
statements at the boom of the hierarchy. Seng mulple statements at the same me can reduce
considerably the number of commands you must enter.
4.
To go back to the original hello interval mer and dead interval mer on interface so-0/0/1, enter:
[edit]
user@host# edit protocols ospf area 0.0.0.0 interface so-0/0/1
[edit protocols ospf area 0.0.0.0 interface so-0/0/1]
user@host# set hello-interval 5 dead-interval 20
[edit protocols ospf area 0.0.0.0 interface so-0/0/1]
user@host# exit
33

[edit]
user@host# show
protocols {
ospf {
area 0.0.0.0 {
interface so-0/0/1 {
hello-interval 5;
dead-interval 20;
}
}
}
}
[edit]
user@host#
5. You also can re-create the other interface, as you had it before, with only a single entry:
[edit]
user@host# set protocols ospf area 0.0.0.0 interface so-0/0/0 hello-interval 5 dead-interval 20
[edit]
user@host# show
protocols {
ospf {
area 0.0.0.0 {
interface so-0/0/0 {
hello-interval 5;
dead-interval 20;
}
interface so-0/0/1 {
hello-interval 5;
dead-interval 20;
}
}
}
}
[edit]
user@host#
34

Online Help in the CLI
IN THIS SECTION
Get Online Help from the Command-Line Interface | 35
CLI Online Help Features | 39
CLI Explorer Overview | 41
Get Online Help from the Command-Line Interface
IN THIS SECTION
Geng Help About Commands | 35
Geng Help About a String in a Statement or Command | 37
Geng Help About Conguraon Statements | 38
Geng Help About System Log Messages | 38
The CLI has a context-sensive online help feature that enables you to access informaon about
commands and statements.
Geng Help About Commands
CLI commands and opons can vary by plaorm and soware release. Each level of the CLI command
hierarchy provides informaon about available commands. You can type a queson mark (?) to get
context-relevant help about commands.
• If you type the queson mark at the command-line prompt, the CLI lists the available commands and
opons. For example, to view a list of top-level operaonal mode commands, this is the result:
user@host> ?
Possible completions:
35

clear Clear information in the system
configure Manipulate software configuration information
file Perform file operations
help Provide help information
mtrace Trace mtrace packets from source to receiver.
monitor Real-time debugging
ping Ping a remote target
quit Exit the management session
request Make system-level requests
restart Restart a software process
set Set CLI properties, date, time, craft display text
show Show information about the system
ssh Open a secure shell to another host
start Start a software process
telnet Telnet to another host
test Diagnostic debugging commands
traceroute Trace the route to a remote host
user@host>
• If you type the queson mark aer entering the complete name of a command or command opon,
the CLI lists the available commands and opons and then re-displays the command names and
opons you typed.
user@host> clear ?
Possible completions:
arp Clear address-resolution information
bgp Clear BGP information
chassis Clear chassis information
firewall Clear firewall counters
igmp Clear IGMP information
interfaces Clear interface information
ilmi Clear ILMI statistics information
isis Clear IS-IS information
ldp Clear LDP information
log Clear contents of a log file
mpls Clear MPLS information
msdp Clear MSDP information
multicast Clear Multicast information
ospf Clear OSPF information
pim Clear PIM information
rip Clear RIP information
route Clear routing table information
36

rsvp Clear RSVP information
snmp Clear SNMP information
system Clear system status
vrrp Clear VRRP statistics information
user@host> clear
• If you type the queson mark in the middle of a command name, the CLI lists possible command
compleons that match the leers you have entered so far. It then re-displays the leers that you
typed. For example, to list all operaonal mode commands that start with the leer
c
, type the
following:
user@host> c?
Possible completions:
clear Clear information in the system
configure Manipulate software configuration information
user@host> c
• For introductory informaon on using the queson mark or the help command, you can also type help
and press Enter:
user@host> help
Geng Help About a String in a Statement or Command
You can use the help command to display help about a text string contained in a statement or command
name:
help apropos
string
string
is a text string about which you want to get help. Use the string to match statement or command
names as well as to match the help strings that are displayed for the statements or commands.
If the string contains spaces, enclose it in quotaon marks (" "). You can also specify a regular expression
for the string, using standard UNIX-style regular expression syntax.
For statements or commands that need input data type as STRING, the supported characters set is as
follows:
• Any printable ASCII characters
• For characters with space, enclose it in double-quotes.
37

• To have double-quote as the input, it should be escaped with ‘\’.
NOTE: No escape characters are supported in a string other than to escape from double
quotes.
• The range of supported characters for aributes is 0 through 65499 characters.
• The range of supported characters for string type ideners is 1 through 255 characters.
In conguraon mode, this command displays statement names and help text that match the string
specied. In operaonal mode, this command displays command names and help text that match the
string specied.
Geng Help About Conguraon Statements
You can display help based on text contained in a statement name using the help topic and help reference
commands:
help topic
word
help reference
statement-name
The help topic command displays usage guidelines for the statement based on informaon that appears
in the Junos OS conguraon guides. The help reference command displays summary informaon about
the statement based on the summary descripons that appear in the Junos OS conguraon guides.
Geng Help About System Log Messages
You can display help based on a system log tag using the help syslog command:
help syslog
syslog-tag
The help syslog command displays the contents of a system log message.
38

CLI Online Help Features
IN THIS SECTION
Help for Omied Statements | 39
Using CLI Command Compleon | 39
Using Command Compleon in Conguraon Mode | 40
Displaying Tips About CLI Commands | 40
Help for Omied Statements
If you have omied a required statement at a specic hierarchy level, when you aempt to move from
that hierarchy level or when you issue the show command in conguraon mode, a message indicates
which statement is missing. For example:
[edit protocols pim interface so-0/0/0]
user@host# top
Warning: missing mandatory statement: 'mode'
[edit]
user@host# show
protocols {
pim {
interface so-0/0/0 {
priority 4;
version 2;
# Warning: missing mandatory statement(s): 'mode'
}
}
}
Using CLI Command Compleon
The Junos OS CLI provides you a command compleon opon that enables the operang system to
recognize commands and opons based on the inial few leers you typed. That is, you do not always
have to remember or type the full command or opon name for the CLI to recognize it.
39

• To display all possible command or opon compleons, type the paral command followed
immediately by a queson mark.
• To complete a command or opon that you have parally typed, press Tab or Space. If the parally
typed leers begin a string that uniquely idenes a command, the complete command name
appears. Otherwise, a prompt indicates that you have entered an ambiguous command, and the
possible compleons display.
Command compleon also applies to other strings, such as lenames, interface names, and usernames.
To display all possible values, type a paral string followed immediately by a queson mark. To complete
a string, press Tab.
Using Command Compleon in Conguraon Mode
The CLI command compleon funcons also apply to the commands in conguraon mode and to
conguraon statements. Specically, to display all possible commands or statements, type the paral
string followed immediately by a queson mark. To complete a command or statement that you have
parally typed, press Tab or Space.
Displaying Tips About CLI Commands
To get ps about CLI commands, issue the help tip cli command. Each me you enter the command, a
new p appears. For example:
user@host> help tip cli
Junos tip:
Use 'request system software validate' to validate the incoming software
against the current configuration without impacting the running system.
user@host> help tip cli
Junos tip:
Use 'commit and-quit' to exit configuration mode after the commit has
succeeded. If the commit fails, you are left in configuration mode.
You can also enter help tip cli
number
to associate a p with a number. This enables you to recall the p
later. For example:
user@host> help tip cli 10
JUNOS tip:
Use '#' in the beginning of a line in command scripts to cause the
rest of the line to be ignored.
40

user@host> help tip cli
JUNOS tip:
Use the 'apply-groups' statement at any level of the configuration
hierarchy to inherit configuration statements from a configuration group.
user@host>
SEE ALSO
CLI Command Compleon Example | 286
CLI Explorer Overview
CLI Explorer is a Web applicaon that helps you to explore Junos OS conguraon statements and
commands. CLI Explorer lists all the conguraon statements and commands the Junos OS supports
across dierent plaorms and soware releases.
To view the available conguraon statements and commands, you can use any of the following ltering
opons:
• Filter by product family—To nd the CLI reference informaon by product family, you can either
select “All products” or select any specic product.
For example: ACX Series, EX Series.
• Filter by number or leer—To nd the CLI reference informaon by number or leer, you can either
select “All” or lter by numbers “3” or “8” or any of the leers (“A”, “B”, “C”...).
For example, if you select the leer “A”, commands such as aaa, aaa clients (TDF), aaa-access-profile
(L2TP LNS) appear.
• Filter by the normal search opon—To use this opon to lter the commands and statements, you
enter your search criteria.
For example, if you enter the number “3”, all the commands and statements containing the number
“3” appear in the search results.
When you click on the link in the search results, you are directed to a page describing the command or
statement that is referenced in a user guide.
To explore the Junos OS conguraon statements and commands, see the CLI Explorer.
41

CLI Environment Sengs
IN THIS SECTION
Customize the CLI Environment | 42
Set the CLI Screen Length and Width | 46
Enable Conguraon Breadcrumbs | 47
In operaonal mode, you (the network administrator) can customize the Junos OS CLI environment to
suit your specic preferences and requirements.
Customize the CLI Environment
IN THIS SECTION
Display the Current CLI Sengs | 43
Set the Terminal Type | 43
Set the CLI Prompt | 44
Set the CLI Directory | 44
Set the CLI Timestamp | 44
Set the Idle Timeout | 45
Set the CLI to Prompt for Restart Aer a Soware Upgrade | 45
Set CLI Command Compleon | 45
42

In operaonal mode, you can customize the CLI environment by using the set cli command. For
example, you can specify the number of lines that are displayed on the screen or your terminal type. The
following output lists the available opons:
user@host>set cli ?
Possible completions:
complete-on-space Set whether typing space completes current word
directory Set working directory
idle-timeout Set maximum idle time before login session ends
logical-system Set default logical system
prompt Set CLI command prompt string
restart-on-upgrade Set whether CLI prompts to restart after software upgrade
screen-length Set number of lines on screen
screen-width Set number of characters on a line
tenant Set default tenant
terminal Set terminal type
timestamp Timestamp CLI output
NOTE: Some values are already set when you use SSH to log in to the device or log in from the
console when its terminal type is already congured: your terminal type, screen length, and
screen width.
Display the Current CLI Sengs
To display the current CLI sengs, use the show cli command:
user@host> show cli
CLI screen length set to 24
CLI screen width set to 80
CLI complete-on-space set to on
Set the Terminal Type
To set the terminal type, use the set cli terminal command:
user@host> set cli terminal
terminal-type
43

The
terminal type
can be one of the following: ansi, vt100, small-xterm, or xterm.
Set the CLI Prompt
The default CLI prompt is user@host>. To change this prompt, use the set cli prompt command. If the
prompt string contains spaces, enclose the string in quotaon marks (" " ).
user@host> set cli prompt
string
NOTE: Changing the CLI prompt is not persistent across CLI sessions. When you exit the CLI and
restart it, the prompt defaults to user@host.
Set the CLI Directory
To set the current working directory, use the set cli directory command:
user@host> set cli directory
directory
The
directory
must be the full pathname of the desired working directory. Aer entering this command,
the CLI switches to the specied directory.
Set the CLI Timestamp
By default, CLI output does not include a mestamp. To include a mestamp in CLI output, use the set
cli timestamp command:
user@host> set cli timestamp [format
time-date-format
| disable]
Enclose the format in single quotaon marks ( ‘ ). If you do not specify a mestamp format, the default
format is
'Mmm dd hh:mm:ss’
(for example, Feb 08 17:20:49).
44

Set the Idle Timeout
By default, a CLI session never mes out aer extended idle me unless you have included the idle-
timeout statement in the user’s login class conguraon. To set the maximum me an individual session
can be idle before the user is logged o the device, use the set cli idle-timeout command:
user@host> set cli idle-timeout
timeout
The
meout
can be 0 through 100,000 minutes. Seng the
meout
to 0 disables the idle meout.
Set the CLI to Prompt for Restart Aer a Soware Upgrade
By default, the CLI prompts users to restart aer a soware upgrade. To disable the prompt, use the set
cli restart-on-upgrade off command:
user@host>set cli restart-on-upgrade off
To reenable the prompt, use the set cli restart-on-upgrade on command:
user@host> set cli restart-on-upgrade on
Set CLI Command Compleon
By default, you can press Tab or the spacebar to have the CLI complete a command.
To have the CLI allow only Tab to complete a command, use the set cli complete-on-space off command:
user@host> set cli complete-on-space off
Disabling complete-on-space
user@host>
To enable the use of the spacebar (as well as Tab) for command compleon, use the set cli complete-on-
space on command:
user@host> set cli complete-on-space on
Enabling complete-on-space
user@host>
45

Set the CLI Screen Length and Width
IN THIS SECTION
Set the Screen Length | 46
Set the Screen Width | 46
You can set the Junos OS CLI screen length and width according to your specic preferences and
requirements.
Set the Screen Length
The default CLI screen length is 24 lines. If output is longer than this, the display scrolls to the
congured screen length and then displays a more prompt. You can press Enter to display the next line, or
press the Spacebar to show the next full screen. Alternavely, you can press h to view all the available
opons, which include navigaon, searching, and saving.
To change the screen length, use the set cli screen-length command:
user@host> set cli screen-length
length
Seng the screen length to 0 lines disables the use of “one screen at a me” output. This seng causes
the screen to scroll all the way through to compleon without displaying the more prompt. Disabling this
UNIX more-type interface can be useful when you are issuing CLI commands from scripts.
Set the Screen Width
The value of CLI screen width can be 0 or in the range of 40 through 1024. The default CLI screen width
is 80 characters. Using a CLI screen width value of 0 disables the display of the output screen, which
may be desirable when using scripts. To change the width, use the set cli screen-width command:
user@host> set cli screen-width
width
46

Enable Conguraon Breadcrumbs
You can congure the output of show configuration operaonal mode commands and show conguraon
mode commands to display conguraon breadcrumbs. These breadcrumbs help you idenfy the exact
locaon in the conguraon hierarchy for the output you are viewing.
Before you enable the conguraon breadcrumbs feature, check the output of the show configuration
command.
user@host> show configuration
...
}
}
}
}
}
fe-4/1/2 {
description "FA4/1/2: mxxj1-mr6 (64.12.137.160/27) (T=bblan, bbmail, bbowmtc)";
unit 0 {
family inet {
filter {
output 151mj;
}
address 64.12.137.187/27 {
vrrp-group 1 {
virtual-address 64.12.137.189;
---(more 18%)-----------------------------------------------------
The output does not clearly indicate the secon of the conguraon being viewed.
To enable the conguraon breadcrumbs feature:
1. Launch conguraon mode in the CLI.
2. Dene a class at the [edit system login] hierarchy level, and set an idle meout value of 10 minutes.
[edit system login]
user@host# set class breadclass idle-timeout 10
47

3. Include the configuration-breadcrumbs statement at the [edit system login class
<class name>
] hierarchy
level.
[edit system login class breadclass]
user@host# set configuration-breadcrumbs
4. Add a user to the dened login class to enable the breadcrumb output view when this user runs the
show configuration operaonal mode command.
[edit system login user user1]
user@host# set class breadclass
5. Commit the conguraon.
[edit]
user@host# commit
Upon enabling conguraon breadcrumbs in the CLI, user1 (the user added to the login class) can
verify the feature in the output by entering the show configuration command.
user1@host> show configuration
...
}
}
}
}
}
fe-4/1/2 {
description "FA4/1/2: mxxj1-mr6 (64.12.137.160/27) (T=bblan, bbmail, bbowmtc)";
unit 0 {
family inet {
filter {
output 151mj;
}
address 64.12.137.187/27 {
vrrp-group 1 {
virtual-address 64.12.137.189;
48

---(more 18%)---[groups main interfaces fe-4/1/2 unit 0 family inet address 64.12.137.187/27
vrrp-group 1]---
The new output indicates the exact locaon of the conguraon hierarchy the user is viewing. In this
case, user1 is currently viewing the interface conguraon of a group.
NOTE: If you enable conguraon breadcrumbs for your own user account, log out and then
log in again to see the changes.
49

3
CHAPTER
Using Conguraon Statements to
Congure a Device
CLI Conguraon Mode Overview | 51
Overview of the Configure Command | 65
Modify the Conguraon of a Device | 71
Use Conguraon Groups to Quickly Congure Devices | 127
View the Conguraon | 163
Verify the Device Conguraon | 173
Commit the Conguraon | 174

CLI Conguraon Mode Overview
IN THIS SECTION
Understanding CLI Conguraon Mode | 51
Enter and Exit CLI Conguraon Mode | 58
Relave Conguraon Mode Commands | 61
Command Compleon in Conguraon Mode | 61
Notaonal Convenons Used in Conguraon Hierarchies | 64
The conguraon mode of the Junos OS CLI enables you to congure a device, using conguraon
statements to set, manage, and monitor device properes.
Understanding CLI Conguraon Mode
IN THIS SECTION
Conguraon Mode Commands | 52
Conguraon Statements and Ideners | 54
Conguraon Statement Hierarchy | 55
You can congure all Junos OS properes, including interfaces, general roung informaon, roung
protocols, and user access, as well as several system hardware properes.
As "Understanding the Junos OS CLI Modes, Commands, and Statement Hierarchies" on page 5
describes, a device conguraon is stored as a hierarchy of statements. In conguraon mode, you
create a set of conguraon statements to use. When you nish entering the conguraon statements
and are certain they are complete and correct, you commit them, which acvates the conguraon on
the device.
51
You can create the conguraon interacvely, or you can create an ASCII text le containing the
conguraon, load it on the device, and commit it.
Conguraon Mode Commands
The following table summarizes each CLI conguraon mode command. The commands are organized
alphabecally.
Table 3: Summary of Conguraon Mode Commands
Command Descripon
activate Remove the inactive: tag from a statement. Statements or ideners that have been acvated
take eect when you next issue the commit command.
annotate
Add comments to a conguraon. You can add comments only at the current hierarchy level.
commit
Commit the set of changes to the database and cause the changes to take operaonal eect.
copy
Make a copy of an exisng statement in the conguraon.
deactivate Add the inactive: tag to a statement, eecvely commenng out the statement or idener
from the conguraon. Statements or ideners marked as inacve are ignored when you issue
the commit command.
delete
Delete a statement or idener. All subordinate statements and ideners contained within the
specied statement path are deleted with it.
edit
Move inside the specied statement hierarchy. If the statement does not exist, it is created.
exit
Exit the current level of the statement hierarchy, returning to the level before the last edit
command, or exit from conguraon mode. The quit and exit commands are equivalent.
extension
Manage conguraons that SDK applicaon packages contribute. Manage them by either
displaying or deleng user-dened conguraons that the named SDK applicaon package
contributed. A conguraon dened in any nave Junos OS package is never deleted by the
extension command.
52

Table 3: Summary of Conguraon Mode Commands
(Connued)
Command Descripon
help
Display help about available conguraon statements.
insert
Insert an idener into an exisng hierarchy.
load
Load a conguraon from an ASCII conguraon le or from terminal input. Your current
locaon in the conguraon hierarchy is ignored when the load operaon occurs.
quit
Exit the current level of the statement hierarchy, returning to the level before the last edit
command, or exit from conguraon mode. The quit and exit commands are equivalent.
rename
Rename an exisng
conguraon statement
or idener.
replace
Replace ideners or values in a conguraon.
rollback
Return to a previously commied conguraon. The soware saves the last 10 commied
conguraons, including the rollback number, date, me, and name of the user who issued the
commit configuration command.
run
Run a CLI command without exing from conguraon mode.
save
Save the conguraon to an ASCII le. The conguraon statements up to and including the
current level of the statement hierarchy are saved, along with the statement hierarchy
containing it. This acon allows a secon of the conguraon to be saved, while fully
specifying the statement hierarchy.
set Create a statement hierarchy and set idener values. This command is similar to edit, except
that your current level in the hierarchy does not change.
show
Display the current conguraon.
status
Display the users currently eding the conguraon.
53

Table 3: Summary of Conguraon Mode Commands
(Connued)
Command Descripon
top Return to the top level of conguraon command mode, which is indicated by the [edit]
banner.
up
Move up one level in the statement hierarchy.
update
Update a private database.
wildcard delete
Delete a statement or idener. All subordinate statements and ideners contained within the
specied statement path are deleted with it. You can use regular expressions to specify a
paern. Based on this paern, the operang system searches for items that contain these
paerns and deletes them.
Conguraon Statements and Ideners
You can congure device properes by including the corresponding statements in the conguraon.
Typically, a statement consists of a system-dened keyword, which is xed text, and an oponal
idener. An idener is an idenfying name that you can dene, such as the name of an interface or a
username, which enables you and the CLI to dierenate among a collecon of statements.
Table 4 on page 54 lists top-level conguraon statements. See CLI Explorer for informaon about
each conguraon statement.
Table 4:
Conguraon Mode Top-Level Statements
Statement Descripon
access
Congure the Challenge Handshake Authencaon Protocol (CHAP).
accounting-options
Congure accounng stascs data collecon for interfaces and rewall lters.
chassis
Congure properes of the router chassis, including condions that acvate alarms and
SONET/SDH framing and concatenaon properes.
54

Table 4: Conguraon Mode Top-Level Statements
(Connued)
Statement Descripon
class-of-service
Congure class-of-service parameters.
firewall
Congure lters that select packets based on their contents.
forwarding-options
Congure forwarding opons, including trac sampling opons.
groups
Congure conguraon groups.
interfaces
Congure interface informaon, such as encapsulaon, interfaces, virtual channel ideners
(VCIs), and data-link connecon ideners (DLCIs).
policy-options
Congure roung policies, which enable you to lter and set properes in incoming and
outgoing routes.
protocols
Congure roung protocols, including BGP, IS-IS, LDP, MPLS, OSPF, RIP, and RSVP.
routing-instances
Congure one or more roung instances.
routing-options
Congure protocol-independent roung opons, such as stac routes, autonomous system
numbers, confederaon members, and global tracing (debugging) operaons to log.
security
Congure IP Security (IPsec) services.
snmp
Congure SNMP community strings, interfaces, traps, and nocaons.
system
Congure systemwide properes, including the hostname, domain name, Domain Name
System (DNS) server, user logins and permissions, mappings between hostnames and
addresses, and soware processes.
Conguraon Statement Hierarchy
The Junos OS conguraon consists of a hierarchy of statements. There are two types of statements:
55

• Container statements, which are branches that can contain other statements (including addional
container statements or leaf statements). Container statements at the top of the hierarchy are
considered to be the trunk of the hierarchy tree.
• Leaf statements (contained by container statements), which do not contain other statements.
The container and leaf statements form the conguraon hierarchy. Each statement at the top level of
the conguraon hierarchy resides at the trunk of a hierarchy tree. These top-level statements are
container statements, containing other statements that form the tree branches. The leaf statements are
the leaves of the hierarchy tree. An individual hierarchy of statements, which starts at the trunk of the
hierarchy tree, is called a statement path.
The following illustraon shows the hierarchy tree, illustrang a statement path for the part of the
protocol conguraon hierarchy responsible for conguring the hello-interval statement on an interface
in an OSPF area.
Figure 2: Conguraon Mode Hierarchy of Statements
The protocols statement is a top-level statement at the trunk of the conguraon tree. The ospf, area, and
interface statements are all subordinate container statements of a higher statement (they are branches of
the hierarchy tree). The hello-interval statement is a leaf on the tree, which in this case contains a data
value, namely the length of the hello-interval, in seconds.
The following conguraon example illustrates the statement hierarchy as shown in Figure 2 on page
56:
56

[edit protocols ospf area
area-number
interface
interface-name
]
The command displays the conguraon as follows:
protocols {
ospf {
area 0.0.0.0 {
interface so-0/0/0 {
hello-interval 5;
}
interface so-0/0/1 {
hello-interval 5;
}
}
}
}
The CLI indents each level in the hierarchy to indicate each statement’s relave posion in the hierarchy.
Addionally, in general, it sets o each level with braces, using an open brace at the beginning of each
hierarchy level and a closing brace at the end. If the statement at a hierarchy level is empty, the braces
are not printed.
Each leaf statement ends with a semicolon. If the hierarchy does not extend as far as a leaf statement,
the last statement in the hierarchy ends with a semicolon.
The conguraon hierarchy can also contain “oneliners” at the lowest level in the hierarchy. Oneliners
remove one level of braces in the syntax and display the container statement, its ideners, the child or
leaf statement, and its aributes all on one line.
For example, dynamic-profile
dynamic-profile-name
aggregate-clients; is a oneliner because the dynamic-profile
statement, its idener
dynamic-profile-name
, and leaf statement aggregate-clients all appear on one line
when you run the show command in conguraon mode:
[edit forwarding-options]
user@host# show
dhcp-relay {
dynamic-profile
dynamic-profile-name
aggregate-clients;
}
57

Enter and Exit CLI Conguraon Mode
You congure Junos OS by entering conguraon mode and creang a hierarchy of conguraon mode
statements.
• To enter conguraon mode, use the configure command.
When you enter conguraon mode, the following conguraon mode commands are available:
user@host>configure
entering configuration mode
[edit]
user@host#?
possible completions:
<[Enter]> Execute this command
activate Remove the inactive tag from a statement
annotate Annotate the statement with a comment
commit Commit current set of changes
copy Copy a statement
deactivate Add the inactive tag to a statement
delete Delete a data element
edit Edit a sub-element
exit Exit from this level
help Provide help information
insert Insert a new ordered data element
load Load configuration from ASCII file
quit Quit from this level
rename Rename a statement
replace Replace character string in configuration
rollback Roll back to previous committed configuration
run Run an operational-mode command
save Save configuration to ASCII file
set Set a parameter
show Show a parameter
status Show users currently editing configuration
top Exit to top level of configuration
up Exit one level of configuration
wildcard Wildcard operations
[edit]
user@host>
58

NOTE: When making conguraon changes, commit them before you exit. If you exit
conguraon mode without comming conguraon changes, you lose the intended
changes.
You must have congure permission to view and use the configure command. When in conguraon
mode, you can view and modify only those statements for which you have access privileges.
• If you enter conguraon mode and another user is also in conguraon mode, a message shows the
user’s name and the part of the conguraon the other user is viewing or eding:
user@host> configure
Entering configuration mode
Users currently editing the configuration:
root terminal d0 (pid 4137) on since 2008-04-09 23:03:07 PDT, idle 7w6d 08:22
[edit]
The configuration has been changed but not committed
[edit]
user@host#
Up to 32 users can be in conguraon mode simultaneously, and they all can make changes to the
conguraon at the same me.
• To exit conguraon mode, use the exit configuration-mode conguraon mode command from any
level, or use the exit command from the top level. For example:
[edit protocols ospf area 0.0.0.0 interface so-0/0/0]
user@host# exit configuration-mode
exiting configuration mode
user@host>
[edit]
user@host# exit
exiting configuration mode
user@host>
59

If you try to exit fconguraon mode using the exit command and the conguraon contains changes
that you have not commied, you see the following message and prompt:
[edit]
user@host# exit
The configuration has been changed but not committed
Exit with uncommitted changes? [yes,no] yes
Exiting configuration mode
user@host>
• To exit with uncommied changes without having to respond to a prompt, use the exit configuration-
mode command. This command is useful when you are using scripts to perform remote conguraon.
[edit]
user@host# exit configuration-mode
The configuration has been changed but not committed
Exiting configuration mode
user@host>
SEE ALSO
Switch Between Operaonal Mode and Conguraon Mode | 12
How to Use the congure exclusive Command Do you want to make this (and the other command
topics) user focused by referring to the main acon users want to do? Example: "How to Prevent
Conicts Using the congure exclusive Command" or "How to Prevent Conguraon Conicts." |
68
How to Work with the Correct ConguraonIf you want to make the tle user focused, this is one
opon (but prey long). You may have a beer idea. What is the main reason a user would use this
command? That goal can become the tle. | 71
How to Modify the Juniper Networks Device Conguraon | 73
Display set Commands from the Conguraon | 169
Commit Operaon When Mulple Users Congure the Soware | 177
Managing Programs and Processes Using Operaonal Mode Commands | 295
60

Relave Conguraon Mode Commands
The top or up command followed by another conguraon command—such as edit, insert, delete,
deactivate, annotate, or show—enables you to quickly move to the top of the hierarchy or to a level above
the area you are conguring.
To issue conguraon mode commands from the top of the hierarchy, use the top command and specify
a conguraon command. For example:
[edit interfaces fxp0 unit 0 family inet]
user@host# top edit system login
[edit system login]
user@host#
To issue conguraon mode commands from a locaon higher up in the hierarchy, use the up
conguraon mode command. Specify the number of levels you want to move up in the hierarchy, and
then specify a conguraon command. For example:
[edit protocols bgp]
user@host# up 2 activate system
SEE ALSO
Display the Current Conguraon | 163
Command Compleon in Conguraon Mode
This topic shows you how to access command help and to use basic command compleon in CLI
conguraon mode. In each case, you access help by using the queson mark (?) character, either alone
or with a paral command or conguraon statement.
To list the conguraon mode commands, use the ? command alone:
[edit]
user@host# ?
<[Enter]> Execute this command
activate Remove the inactive tag from a statement
61

annotate Annotate the statement with a comment
commit Commit current set of changes
copy Copy a statement
deactivate Add the inactive tag to a statement
delete Delete a data element
edit Edit a sub-element
exit Exit from this level
extension Extension operations
help Provide help information
insert Insert a new ordered data element
load Load configuration from ASCII file
quit Quit from this level
rename Rename a statement
replace Replace character string in configuration
rollback Roll back to previous committed configuration
run Run an operational-mode command
save Save configuration to ASCII file
set Set a parameter
show Show a parameter
status Show users currently editing configuration
top Exit to top level of configuration
up Exit one level of configuration
wildcard Wildcard operations
[edit]user@host#
To list all the statements available at a parcular hierarchy level, use ? aer the name of the hierarchy
level you wish to view. In this example, see the edit and edit protocols hierarchies:
[edit]
user@host# edit ?
Possible completions:
> accounting-options Accounting data configuration
> chassis Chassis configuration
> class-of-service Class-of-service configuration
> firewall Define a firewall configuration
> forwarding-options Configure options to control packet sampling
> groups Configuration groups
> interfaces Interface configuration
> policy-options Routing policy option configuration
> protocols Routing protocol configuration
> routing-instances Routing instance configuration
> routing-options Protocol-independent routing option configuration
62

> snmp Simple Network Management Protocol
> system System parameters
user@host# edit protocols ?
Possible completions:
<[Enter]> Execute this command
> bgp BGP options
> connections Circuit cross-connect configuration
> dvmrp DVMRP options
> igmp IGMP options
> isis IS-IS options
> ldp LDP options
> mpls Multiprotocol Label Switching options
> msdp MSDP options
> ospf OSPF configuration
> pim PIM options
> rip RIP options
> router-discovery ICMP router discovery options
> rsvp RSVP options
> sapSession Advertisement Protocol options
> vrrp VRRP options
| Pipe through a command
To list all commands that start with a parcular string or leer, enter the string, leer, or both, and then
enter the ? character. This example shows all the routing-options commands starng with the leer “a”:
user@host# edit routing-options a?
Possible completions:
> aggregate Coalesced routes
> autonomous-system Autonomous system number
This example shows all congured xe- interfaces. You can display these interfaces by using the rst two
leers of the abbreviaon (ex) and the ? character:
user@host# edit interfaces ex?
<interface_name> Interface name
ex-0/2/0 Interface name
ex-0/2/1 Interface name
[edit]
63

You can also show a list of all congured policy statements:
user@host# show policy-options policy-statement ?
user@host# show policy-options policy-statement
<policy_name> Name to identify a policy filter
lo0only-v4 Name to identify a policy filter
lo0only-v6 Name to identify a policy filter
lo2bgp Name to identify a policy filter
SEE ALSO
How to Add Conguraon Statements and Ideners | 75
Notaonal Convenons Used in Conguraon Hierarchies
When you are working in CLI conguraon mode, the banner on the line preceding the prompt indicates
the current hierarchy level. In the following example, the level is [edit protocols ospf]:
[edit protocols ospf]
user@host#
NOTE: Junos OS documentaon uses user@host# as the standard conguraon mode prompt. In a
CLI session, the prompt shows your user ID and the congured name of the Juniper Networks
device you are working on.
Use the set ? command to display the statements that you can include in the conguraon at the current
level. The help apropos command is also context-sensive, displaying matching statements only at the
current command hierarchy level and below.
Statements are listed alphabecally within each hierarchy and subhierarchy. An excepon occurs if a
subhierarchy is so long that it might be dicult to determine where it ends and its next peer statement
begins. In case of a very long subhierarchy, the subhierarchy appears at the end of its parent hierarchy
instead of in alphabecal order. In this excepon scenario, a placeholder appears in the alphabecal
posion where the subhierarchy would have been listed.
64

For example, at the [edit interfaces
interface-name
unit
logical-unit-number
] hierarchy level, the
family
family-name
subhierarchy has more than 20 child statements, including several subhierarchies with
child statements of their own. The full family
family-name
hierarchy appears at the end of its parent
hierarchy ([edit interfaces
interface-name
unit
logical-unit-number
]), and the following placeholder appears
at its alphabecal posion:
family
family-name
{
...
the
family
subhierarchy appears after the main
[edit interfaces
interface-name
unit
logical-unit-number
]
hierarchy
...
}
Another excepon to alphabecal order is that the disable statement always appears rst in any
hierarchy that includes it.
Overview of the Configure Command
IN THIS SECTION
Forms of the configure Command | 65
How to Use the configure Command | 67
How to Use the configure exclusive Command | 68
How to Work with the Correct Conguraon | 71
You (the network administrator) use the
configure command to enter CLI conguraon mode. You can
also use it to gather other informaon, such as which other users are currently in conguraon mode.
Forms of the configure Command
Junos OS supports three forms of the configure command: configure, configure private, and configure
exclusive. These forms control how users edit and commit conguraons. You can use this command to
coordinate the work of mulple users who manage the network and device conguraon.
65

Table 5: Forms of the configure Command
Command Edit Access Commit Access
configure
• No one can lock the conguraon. All users can
make conguraon changes.
• When you enter conguraon mode, the CLI
displays the following informaon:
• A list of other users eding the
conguraon
• Hierarchy levels the users are viewing or
eding
•
Whether the conguraon has been
changed, but not commied
•
When more than one user makes changes to a
conguraon, the most recent changes take
precedence when the conguraon is
commied.
• All users can commit any changes
to the conguraon.
• If you and another user make
changes and the other user
commits changes, your changes
are commied as well.
configure
exclusive
• One user locks the conguraon and makes
changes without interference from other users.
• If you enter conguraon mode while another
user has locked the conguraon (with the
configure exclusive command), the CLI displays
the user’s PID and the hierarchy level the user is
viewing or eding.
• If you enter conguraon mode when another
user has locked the conguraon, you can
aempt to forcibly log out that user using the
request system logout operaonal mode
command. For details, see the CLI Explorer.
• Only the user who has locked the
conguraon can commit it.
• Other users can enter and exit
conguraon mode, but they
cannot commit any changes they
aempt to make to the
conguraon unl it is unlocked.
66

Table 5: Forms of the configure Command
(Connued)
Command Edit Access Commit Access
configure private
• Mulple users can edit the conguraon at the
same me.
• Each user has a private candidate conguraon
to edit independently of other users.
• When mulple users enter conicng
conguraons, the rst commit operaon takes
precedence over subsequent commit
operaons.
• When you commit the
conguraon, the device does not
immediately accept your private
candidate conguraon as the
new operaonal conguraon.
Before the device accepts your
conguraon, it veries that no
other user has modied the
operaonal (running)
conguraon .
•
If another user has modied the
conguraon, you can merge the
modicaons into your private
candidate conguraon and
aempt to commit again.
SEE ALSO
Commit a Device Conguraon | 176
Display set Commands from the Conguraon | 169
Display Users Currently Eding the Conguraon | 72
How to Use the configure Command
Up to 32 users can work in conguraon mode simultaneously; all can make changes to the
conguraon at the same me. When you commit changes to the conguraon, you may be comming
a combinaon of changes that you and other users have made. For this reason, you must keep track of
who is in conguraon mode with you.
To see other users currently logged in to the same device in conguraon mode:
•
Use the configure command to enter CLI conguraon mode.
67

If other users are in conguraon mode, the message displayed indicates who the users are and what
poron of the conguraon each person is viewing or eding.
user@host> configure
Entering configuration mode
Current configuration users:
root terminal p3 (pid 1088) on since 2018-05-13 01:03:27 EDT
[edit interfaces so-3/0/0 unit 0 family inet]
The configuration has been changed but not committed
[edit]
user@host#
How to Use the configure exclusive Command
If you enter conguraon mode using the configure exclusive command, you lock the candidate global
conguraon for as long as you remain in conguraon mode. (The candidate global conguraon is also
known as the shared conguraon or shared conguraon database.) Using the configure exclusive
command, you can make changes without interference from other users. Other users can enter and exit
conguraon mode, but they cannot make any permanent changes to the conguraon. Also, any
aempted changes by other users while the conguraon is in the locked state are discarded as soon as
the other users exit conguraon mode.
If another user has locked the conguraon, and you need to forcibly log them out, use the operaonal
mode command request system logout pid
pid_number
. You can locate the
pid_number
in the nocaon you
receive upon entering conguraon mode when someone else has locked it for exclusive access.
If you enter conguraon mode while another user is also in conguraon mode and has locked the
conguraon, a message idenes the user. The message also idenes the poron of the conguraon
that the user is viewing or eding. For example, in the following example, the
pid_number
of the user
who has locked the conguraon for exclusive access is 1088:
user@host> configure
Entering configuration mode
Users currently editing the configuration:
root terminal p3 (pid 1088) on since 2018-10-30 19:47:58 EDT, idle 00:00:44
exclusive [edit interfaces so-3/0/0 unit 0 family inet]
68

In configure exclusive mode, any uncommied changes are discarded when you exit:
user@host> configure exclusive
warning: uncommitted changes will be discarded on exit
Entering configuration mode
[edit]
user@host# set system host-name cool
[edit]
user@host# quit
The configuration has been changed but not committed
warning: Auto rollback on exiting 'configure exclusive'
Discard uncommitted changes? [yes,no]yes
warning: discarding uncommitted changes
load complete
Exiting configuration mode
When you use the yes opon to exit configure exclusive mode, Junos OS discards any uncommied
changes and rolls backs the conguraon to its previously commied state. The no opon enables you to
connue eding or to commit your changes in configure exclusive mode.
When one user exits configure exclusive mode while another user is in configure private mode, Junos OS
rolls back any uncommied changes in the private mode session.
Another rollback can happen if you enter conguraon mode with the configure exclusive command and
issue the commit confirmed command, but without conrming the commit within the specied interval. By
not conrming the commit within the specied interval, you trigger an automac rollback. Aer an
automac rollback occurs, the operang system removes the exclusive lock from your session. As a
result, the error message “access has been revoked” appears. This error message appears because the
session is no longer an exclusive session. This means that the conguraon is back to the default state:
anyone with access can edit the conguraon, commit it, or both. To re-lock the conguraon, you must
use the configure exclusive command again.
user@host>configure exclusive
warning: uncommitted changes will be discarded on exit
Entering configuration mode
[edit]
user@host# commit confirmed 1
commit confirmed will be automatically rolled back in 1 minutes unless confirmed
69

commit
# commit confirmed will be rolled back in 1 minute
Commit was not confirmed; automatic rollback complete.
[edit]
user@host# commit
error: access has been revoked.
user@host# commit check
error: access has been revoked.
user@host>configure exclusive
warning: uncommitted changes will be discarded on exit
Entering configuration mode
If you iniate a configure exclusive session, issue the commit confirmed command, and conrm the commit,
your session retains the exclusive lock. You can connue to make changes to the conguraon while sll
in a locked exclusive session.
user@host> configure exclusive
warning: uncommitted changes will be discarded on exit
Entering configuration mode
[edit]
user@host# commit confirmed 1
commit confirmed will be automatically rolled back in 1 minutes unless confirmed
commit complete
# commit confirmed will be rolled back in 1 minute
[edit]
user@host# commit
commit complete
SEE ALSO
How to Add Conguraon Statements and Ideners | 75
70

How to Work with the Correct Conguraon
When you are in configure private mode, you must work with a copy of the most recently commied
shared conguraon. If the global conguraon changes, you can issue the update command to update
your private candidate conguraon. When you update your private candidate conguraon, that
conguraon contains a copy of the most recently commied conguraon with your private changes
merged in.
NOTE: Merge conicts can occur when you issue the update command.
You can also issue the rollback command to discard your private candidate conguraon changes and
obtain the most recently commied conguraon.
NOTE: Junos OS does not support using the configure private command to congure statements
corresponding to third-party YANG data models such as OpenCong data models or custom
YANG data models.
Modify the Conguraon of a Device
IN THIS SECTION
Display Users Currently Eding the Conguraon | 72
How to Modify the Juniper Networks Device Conguraon | 73
How to Add Conguraon Statements and Ideners | 75
How to Delete a Statement from a Device Conguraon | 76
Example: Delete a Statement from the Device Conguraon | 79
Copy a Statement in the Conguraon | 81
Example: Copy a Statement in the Conguraon | 81
Example: Replace a Conguraon | 85
Insert a New Idener in a Device Conguraon | 92
Example: Insert a New Idener in a Device Conguraon | 92
71

Deacvate and Reacvate Statements and Ideners in a Device Conguraon | 97
Example: Deacvate and Reacvate Statements and Ideners in a Device Conguraon | 98
How to Make Global Changes in the Device Conguraon | 100
Common Regular Expressions to Use with the replace Command | 101
Example: How to Use Global Replace in a Device Conguraon—the \n Back Reference | 103
Example: Global Replace in a Device Conguraon—Replacing an Interface Name | 106
Example: Global Replace in a Device Conguraon—the upto Opon | 109
Add Comments in a Device Conguraon | 112
Example: Include Comments in a Device Conguraon by Using the CLI | 114
Example: Use the Wildcard Command with the Range Opon | 117
The CLI enables you to modify an exisng Junos OS conguraon. This secon explains the specics of
adding a statement, deleng a statement, copying a statement, and inserng a new idener, including
examples.
Display Users Currently Eding the Conguraon
To display the users currently eding the conguraon, use the status conguraon mode command:
user@host# status
Users currently editing the configuration:
rchen terminal p0 (pid 55691) on since 2018-03-01 13:17:25 PST
[edit interfaces]
The system displays who is eding the conguraon (rchen), where the user is logged in (terminal p0), the
date and me the user logged in (2018-03-01 13:17:25 PST), and what level of the hierarchy the user is
eding ([edit interfaces]).
If you issue the status conguraon mode command and a user has scheduled a candidate conguraon
to become acve for a future me, the system displays who scheduled the commit (
root
), where the user
72

is logged in (terminal d0), the date and me the user logged in (2018-10-31 14:55:15 PST), and that a commit
is pending (commit at).
[edit]
user@host# status
Users currently editing the configuration:
root terminal d0 (pid 767) on since 2018-10-31 14:55:15 PST, idle 00:03:09
commit at
If you issue the status conguraon mode command and a user is eding the conguraon in congure
exclusive mode, the system displays who is eding the conguraon (root), where the user is logged in
(terminal d0), the date and me the user logged in (2018-11-01 13:05:11 PST), and that a user is eding the
conguraon in congure exclusive mode (exclusive [edit]).
[edit]
user@host# status
Users currently editing the configuration:
root terminal d0 (pid 2088) on since 2018-11-01 13:05:11 PST
exclusive [edit]
SEE ALSO
Forms of the congure Command | 65
Schedule a Commit Operaon | 183
How to Use the congure Command | 67
How to Modify the Juniper Networks Device Conguraon
To congure a Juniper Networks device or to modify an exisng conguraon, you add statements to
the conguraon using the edit and set commands. For each statement hierarchy, you create the
hierarchy starng with a statement at the top level. You then connue creang the hierarchy with
statements that move progressively lower in the hierarchy.
To modify the hierarchy, you use two conguraon mode commands. Select the relevant command
based on what you want to accomplish:
73

• edit—Moves to a specied hierarchy level. If that hierarchy level does not exist, the edit command
creates it. The edit command has the following syntax:
edit <
statement-path
>
• set—Creates a conguraon statement and sets idener values. Aer you issue a set command, you
remain at the same level in the hierarchy. The set command has the following syntax:
set <
statement-path
>
statement
<
identifier
>
The hierarchy to the conguraon statement and the statement itself is
statement-path
. If you have
already moved to the statement’s hierarchy level, you can omit the statement path. The conguraon
statement itself is
statement
. The
identifier
string idenes an instance of a statement.
Statements can be either container statements or leaf statements. A container statement can include
addional container statements within it, as well as leaf statements. A leaf statement, however, stands
alone. The command edit? displays the container statements, while set? displays both the container and
leaf statements, using > to dierenate between them.
NOTE: You cannot use the edit command to change the value of ideners. You must use the set
command.
SEE ALSO
Relave Conguraon Mode Commands | 61
How to Use the congure exclusive Command Do you want to make this (and the other command
topics) user focused by referring to the main acon users want to do? Example: "How to Prevent
Conicts Using the congure exclusive Command" or "How to Prevent Conguraon Conicts." | 68
How to Work with the Correct ConguraonIf you want to make the tle user focused, this is one
opon (but prey long). You may have a beer idea. What is the main reason a user would use this
command? That goal can become the tle. | 71
Display the Current Conguraon | 163
74

How to Add Conguraon Statements and Ideners
You congure all properes of a Juniper Networks device by including statements in the conguraon. A
statement consists of a keyword, which is xed text. You can also include an idener in a statement. An
idener is an idenfying name that you dene, such as the name of an interface or a username, and
that enables you and the CLI to discriminate among a collecon of statements.
For example, the following list shows the statements available at the top level in conguraon mode:
user@host# set ?
Possible completions:
> accounting-options Accounting data configuration
+ apply-groups Groups from which to inherit configuration data
> chassis Chassis configuration
> class-of-service Class-of-service configuration
> firewall Define a firewall configuration
> forwarding-options Configure options to control packet sampling
> groups Configuration groups
> interfaces Interface configuration
> policy-options Routing policy option configuration
> protocols Routing protocol configuration
> routing-instances Routing instance configuration
> routing-options Protocol-independent routing option configuration
> snmp Simple Network Management Protocol
> system System parameters
An angle bracket ( > ) before the statement name indicates that it is a container statement and that you
can dene other statements at levels below it. If there is no angle bracket ( > ) before the statement
name, the statement is a leaf statement; you cannot dene other statements at hierarchy levels below it.
A plus sign (+) before the statement name indicates that it can contain a set of values. To specify a set,
include the values in brackets. For example:
[edit]
user@host# set policy-options community my-as1-transit members [65535:10 65535:11]
In some statements, you can include an idener. For some ideners, such as interface names, you
must specify the idener in a precise format. For example, the interface name so-0/0/0 refers to a
SONET/SDH interface that is on the Flexible PIC Concentrator (FPC) in slot 0, in the rst PIC locaon,
and in the rst port on the Physical Interface Card (PIC).
75

For other ideners, such as interface descripve text and policy and rewall term names, you can
specify any name, including special characters, spaces, and tabs.
You must enclose ideners in quotaon marks (double quotes). You must also use quotaon marks to
enclose ideners and any strings that include a space, a tab character, or any of the following
characters:
( ) [ ] { } ! @ # $ % ^ & | ' = ?
If you do not type an opon for a statement that requires one, a message indicates the type of
informaon required. In this example, you must type an area number to complete the command:
[edit]
user@host# set protocols ospf area
^
syntax error, expecting <identifier>
SEE ALSO
Display the Current Conguraon | 163
About Specifying Statements and Ideners | 237
How to Delete a Statement from a Device Conguraon
You delete a statement or idener from a device conguraon using the delete conguraon mode
command. Deleng a statement or an idener eecvely "uncongures" the funconality associated
with that statement or idener, returning that funconality to its default condion.
user@host# delete <
statement-path
> <
identifier
>
When you delete a statement, the statement and all its subordinate statements and ideners are
removed from the conguraon.
For statements that can have more than one idener, when you delete one idener, only that
idener is deleted. The other ideners in the statement remain.
76

To delete the enre hierarchy starng at the current hierarchy level, use the delete command without
specifying a statement or an idener. When you omit the statement or idener, you are prompted to
conrm the deleon:
[edit]
user@host# delete
Delete everything under this level? [yes, no] (no)
Possible completions:
no Don't delete everything under this level
yes Delete everything under this level
Delete everything under this level? [yes, no] (no)
NOTE: You cannot delete mulple statements or ideners within a hierarchy using a single
delete command. You must delete each statement or idener individually, using mulple delete
commands. For example, consider the following conguraon at the [edit system] hierarchy level:
system {
host-name
host-211
;
domain-name
domain-122
;
backup-router
192.168.71.254
;
arp;
authentication-order [ radius password tacplus ];
}
To delete the domain-name, host-name, and backup-router from the conguraon, you must delete each
statement individually.
user@host delete system host-name
host-211
user@host delete system domain-name
domain-122
user@host delete system backup-router
192.168.71.254
You cannot issue a single delete command. For example, the following command would not work:
user@host> delete system hostname
host-211
domain-name
domain-122
backup-router
192.168.71.254
You can delete related conguraon items simultaneously, such as channelized interfaces or stac
routes, by using a single command and regular expressions. Deleng a statement or an idener
eecvely “uncongures” the funconality associated with that statement or idener, returning that
funconality to its default condion.
77

You can delete only certain parts of the conguraon where you normally put mulple items, such as
interfaces. However, you cannot delete "groups" of dierent items, as shown in this example:
user@host# show system services
ftp;
rlogin;
rsh;
ssh {
root-login allow;
}
telnet;
[edit]
user@host# wildcard delete system services *
syntax error.
When you delete a statement, the statement and all its subordinate statements and ideners are
removed from the conguraon.
To delete related conguraon items, issue the wildcard conguraon mode command with the delete
opon and specify the statement path, the items to be summarized with a regular expression, and the
regular expression, as follow:
user@host# wildcard delete <
statement-path
> <
identifier
>
<regular-expression>
NOTE: When you use the wildcard command to delete related conguraon items, the regular
expression must be the nal statement.
If the Junos OS matches more than eight related items, the CLI displays only the rst eight items.
How to Delete Interfaces from the Conguraon
You can delete mulple T1 interfaces in the range from t1-0/0/0:0 through t1-0/0/0:23 by using this
syntax:
user@host# wildcard delete interfaces t1-0/0/0:.*
matched: t1-0/0/0:0
matched: t1-0/0/0:1
matched: t1-0/0/0:2
Delete 3 objects? [yes,no] (no) no
78

How to Delete Routes from the Conguraon
You can delete stac routes in the range from 172.0.0.0 to 172.255.0.0 by using this syntax:
user@host# wildcard delete routing-options static route 172.*
matched: 172.16.0.0/12
matched: 172.16.14.0/24
matched: 172.16.100.0/24
matched: 172.16.128.0/19
matched: 172.16.160.0/24
matched: 172.17.12.0/23
matched: 172.17.24.0/23
matched: 172.17.28.0/23
...
Delete 13 objects? [yes,no] (no)
Example: Delete a Statement from the Device Conguraon
The following example shows how to delete the ospf statement, eecvely unconguring OSPF on the
router:
[edit]
user@host# set protocols ospf area 0.0.0.0 interface so-0/0/0 hello-interval 5
[edit]
user@host# show
protocols {
ospf {
area 0.0.0.0 {
interface so-0/0/0 {
hello-interval 5;
}
}
}
}
[edit]
user@host# delete protocols ospf
[edit]
user@host# show
79

[edit]
user@host#
Delete all statements from the current level down:
[edit]
user@host# edit protocols ospf area 0.0.0.0
[edit protocols ospf area 0.0.0.0]
user@host# set interface so-0/0/0 hello-interval 5
[edit protocols ospf area 0.0.0.0]
user@host# delete
Delete everything under this level? [yes, no] yes
[edit protocols ospf area 0.0.0.0]
user@host# show
[edit]
user@host#
Uncongure a specic property. In this example, remove the interface speed seng:
[edit]
user@host# set interfaces so-3/0/0 speed 100mb
[edit]
user@host# show
interfaces {
so-3/0/0 {
speed 100mb;
}
}
[edit]
user@host# delete interfaces so-3/0/0 speed
[edit]
user@host# show
interfaces {
so-3/0/0;
}
80

Copy a Statement in the Conguraon
When you have many similar statements in a device conguraon, you can add one statement and then
make copies of that statement. Copying a statement duplicates that statement and the enre hierarchy
of statements congured under that statement. Copying statements is useful when you are conguring
many physical or logical interfaces of the same type.
To make a copy of an exisng statement in the conguraon:
1. Use the conguraon mode copy command:
user@host# copy
existing-statement
to
new-statement
2. Immediately aer you have copied a poron of the conguraon, check the validity of the new
conguraon.
3. If the conguraon is invalid, modify either the copied poron or the original poron to produce a
valid conguraon.
Example: Copy a Statement in the Conguraon
IN THIS SECTION
Requirements | 81
Overview | 82
Conguraon | 82
This example shows how you can create one virtual connecon (VC) on an interface by copying an
exisng VC.
Requirements
No special conguraon beyond device inializaon is required before conguring this example.
81

Before you begin this example, congure the following inial conguraon:
[edit interfaces]
user@host# show
at-1/0/0 {
description "PAIX to MAE West"
encapsulation atm-pvc;
unit 61 {
point-to-point;
vci 0.61;
family inet {
address 10.0.1.1/24;
}
}
}
To quickly congure the inial conguraon for this example, copy the following commands, paste them
into a text le, remove any line breaks and change any details necessary to match your network
conguraon, copy and paste this command into the CLI at the [edit] hierarchy level, and then enter
commit in conguraon mode.
set interfaces at-1/0/0 description "PAIX to MAE West"
set interfaces at-1/0/0 encapsulation atm-pvc
set interfaces at-1/0/0 unit 61 point-to-point
set interfaces at-1/0/0 unit 61 vci 0.61
set interfaces at-1/0/0 unit 61 family inet address 10.0.1.1/24
Overview
In this example illustrang how to copy statements, you add a virtual connecon that is very similar to a
virtual connecon already congured.
Conguraon
IN THIS SECTION
CLI Quick Conguraon | 83
Congure by Copying | 83
Results | 84
82

CLI Quick Conguraon
Start at the [edit interfaces at-1/0/0] hierarchy level.
copy unit 61 to unit 62
set unit 62 vci 0.62
edit unit 62
replace pattern 10.0.1.1 with 10.0.2.1
Congure by Copying
Step-by-Step Procedure
To congure by copying a conguraon:
1. Go to the [edit interfaces at-1/0/0] hierarchy level and copy unit 61.
[edit interfaces at-1/0/0]
user@host# copy unit 61 to unit 62
2. Take a look at the new conguraon and see what you need to change to make the conguraon
valid.
user@host# show interfaces at-1/0/0
description "PAIX to MAE West"
encapsulation atm-pvc;
unit 61 {
point-to-point;
vci 0.61;
family inet {
address 10.0.1.1/24;
}
}
unit 62 {
point-to-point;
vci 0.61;
family inet {
address 10.0.1.1/24;
83

}
}
3. Change the conguraon to make it valid.
In this example you want to recongure the virtual circuit idener (VCI) and virtual path idener
(VPI).
[edit interfaces at-1/0/0]
user@host# set unit 62 vci 0.62
You also want to replace the IP address of the new interface with its own IP address.
[edit interfaces at-1/0/0]
user@host# edit unit 62
user@host# replace pattern 10.0.1.1 with 10.0.2.1
Results
[edit]
show interfaces
at-1/0/0 {
description "PAIX to MAE West"
encapsulation atm-pvc;
unit 61 {
point-to-point;
vci 0.61;
family inet {
address 10.0.1.1/24;
}
}
unit 62 {
point-to-point;
vci 0.62;
family inet {
address 10.0.2.1/24;
}
84

}
}
Example: Replace a Conguraon
IN THIS SECTION
Requirements | 85
Overview | 85
Conguraon | 86
If you need to make changes to the conguraon of a device, you can always remove the original
conguraon sengs using the delete command and add your new conguraon sengs using the set
command. However, there are other ways of modifying a conguraon that are more ecient and easier
to use.
This example shows how to use the following conguraon mode commands to update an exisng
conguraon:
• rename—Rename an exisng conguraon seng, such as an interface name. This command can be
useful when you are adding new interfaces to a device.
• copy—Copy a conguraon seng and the enre hierarchy of statements congured under that
seng. Copying conguraon statements is useful when you are conguring many physical or logical
interfaces of the same type.
• replace—Make global changes to text paerns in the conguraon. For example, if you consistently
misspell a word common to the descripon statement for all of the interfaces on your device, you
can x this mistake with a single command.
Requirements
No special conguraon beyond device inializaon is required before conguring this example.
Overview
During the rst example in this topic, you make the following conguraon changes:
• Create a new interface with a descripon that contains a typing error.
85

• Copy the conguraon from the interface that you created to create a new interface.
• Rename one of the interfaces that you created.
• Fix the typing error in the descripon for the interfaces that you created.
In the second, shorter example, you try some of the same commands under slightly dierent
circumstances.
Conguraon
IN THIS SECTION
Use the Copy, Rename, and Replace Commands to Modify a Loopback Interface Conguraon | 86
Compare the Copy Command at the Top-Level Conguraon Hierarchy Level | 89
Use the Copy, Rename, and Replace Commands to Modify a Loopback Interface Conguraon
Step-by-Step Procedure
CAUTION: If your exisng conguraon uses any of the loopback interface unit
numbers used in this example, you must substute dierent unused loopback interface
unit numbers. Otherwise, following these steps could damage the exisng operaonal
status of your device.
To create and modify a conguraon of a loopback interface using the copy, rename, and replace
commands:
1. Create a new loopback interface unit number and include a descripon.
The mistakes in the spelling of loopback in the descripon are intenonal.
[edit]
user@host# set interfaces lo0 unit 100 description "this is a lopbck interface"
86

2. Display the conguraon for the loopback interface you have just added.
[edit]
user@host# show interfaces lo0 unit 100
description "this is a lopbck interface";
3. Duplicate the loopback interface you have just created, errors included, from unit 100 to unit 101.
[edit]
user@host# copy interfaces lo0 unit 100 to unit 101
4. Display the conguraons for loopback interfaces lo0 unit 100 and lo0 unit 101.
[edit]
user@host# show interfaces lo0 unit 100
description "this is a lopbck interface";
[edit]
user@host# show interfaces lo0 unit 101
description "this is a lopbck interface";
The copy command duplicates an interface including any child statements, such as description.
5. Rename the loopback interface lo0 unit 100 to loopback interface lo0 unit 102.
[edit]
user@host# rename interfaces lo0 unit 100 to unit 102
6. Display the conguraon for loopback interface lo0 unit 100.
[edit]
user@host# show interfaces lo0 unit 100
[edit]
user@host#
You should not see any results from this command. The loopback interface lo0 unit 100 is now gone.
The rename command replaces the conguraon statement indicated with the new conguraon.
87

7. Fix the misspelling of the word
loopback
in the descripons for loopback interfaces lo0 unit 101 and
lo0 unit 102.
[edit]
user@host# replace pattern lopbck with loopback
8. Display the conguraon for loopback interfaces lo0 unit 101 and lo0 102 to verify that the word
loopback
is now spelled correctly.
[edit]
user@host# show interfaces lo0 unit 101
description "this is a loopback interface";
[edit]
user@host# show interfaces lo0 unit 102
description "this is a loopback interface";
The replace command replaces all instances of the paern specied in the command, unless limited in
some way. The next example in this topic shows one way to limit the eect of the replace command.
9. In conguraon mode, use the rollback command to returnthe device conguraon to the state it was
in before you executed the previous steps.
[edit]
user@host# rollback
Results
In conguraon mode, use the show interfaces lo0 unit 101 and show interfaces lo0 unit 102 commands to
ensure that the device conguraon is in the state it was in before you executed the steps in this
example.
[edit]
user@host: show interfaces lo0 unit 101
[edit]
user@host#
88

You should not see any results from this command.
[edit]
user@host# show interfaces lo0 unit 102
[edit]
user@host#
You should not see any results from this command.
Compare the Copy Command at the Top-Level Conguraon Hierarchy Level
Step-by-Step Procedure
The previous example shows the copy, rename, and replace commands at the [edit interfaces
interface-name
unit
logical-interface-number
] hierarchy level. This example shows how some of these commands work at
the top level of the CLI conguraon mode hierarchy.
The following example requires you to navigate to various levels in the conguraon hierarchy. For
informaon about navigang the CLI, see "Using the CLI Editor in Conguraon Mode" on page 19 .
1. Create an Ethernet interface.
[edit]
user@host# set interfaces et-2/0/0 unit 0 family inet address 192.0.2.2
2. Copy the interface you just created to another interface.
[edit]
user@host# copy interfaces et-2/0/0 to et-2/1/0
Compare this copy command to the one in the previous example, where the copy command takes the
keyword unit before the value to be copied:
[edit]
user@host# copy interfaces lo0 unit 100 to unit 101
Noce that the keyword interfaces is not repeated aer the preposion to and before the value to be
copied. This happens in some top-level statements with the copy command.
89

TIP: Similarly, in the rename command, you do not repeat the keyword part of the statement
before the new idener in some top-level statements.
3. Show your conguraon so far.
[edit]
user@host# show interfaces
et-2/0/0 {
unit 0 {
family inet {
address 192.0.2.2/32;
}
}
}
et-2/1/0 {
unit 0 {
family inet {
address 192.0.2.2/32;
}
}
}
4. Replace the address for et-2/1/0 with another IP address.
[edit interfaces et-2/1/0 unit 0 family inet]
user@host# replace pattern 192.0.2.2 with 192.0.2.40
Noce that if you want to change only a specic occurrence of a paern instead of all occurrences,
youmust navigate to that specic hierarchy level before using the replace command.
5. Show the interfaces again.
[edit]
user@host# show interfaces
et-2/0/0 {
unit 0 {
family inet {
address 192.0.2.2/32;
}
90

}
}
et-2/1/0 {
unit 0 {
family inet {
address 192.0.2.40/32;
}
}
}
6. In conguraon mode, use the rollback command to return the device conguraon to the state it
was in before you executed the previous steps.
[edit]
user@host# rollback
Results
In conguraon mode, use the show interfaces et-2/0/0 and show interfaces et-2/1/0 commands to ensure
that the device conguraon is in the state it was in before you executed the steps in this example.
[edit]
user@hostshow interfaces et-2/0/0
[edit]
user@host#
You should not see any results from this command.
[edit]
user@R1# show interfaces et-2/1/0
[edit]
user@host#
You should not see any results from this command.
91

Insert a New Idener in a Device Conguraon
When conguring a Juniper Networks device, you can enter most statements and ideners in any
order. Regardless of the order in which you enter the conguraon statements, the CLI always displays
the conguraon in a strict order. However, in a few cases the order of the statements maers because
the conguraon statements create a sequence that is analyzed in order.
For example, in a roung policy or rewall lter, you dene terms that are analyzed sequenally. Also,
when you create a named path in dynamic MPLS, you dene an ordered list of the transit routers in the
path, starng with the rst transit router and ending with the last one.
To modify a poron of the conguraon in which the statement order maers, use the insert
conguraon mode command:
user@host#insert <
statement-path
>
identifier1
(before | after)
identifier2
If you do not use the insert command but instead congure the idener, the idener is placed at the
end of the list of similar ideners.
Example: Insert a New Idener in a Device Conguraon
IN THIS SECTION
Requirements | 93
Overview | 94
Conguraon | 94
This example shows the use of the insert command.
Whereas a term added using the set command is placed at the end of the exisng list of terms, you use
the insert command to add a term in the order you specify. Specifying the order of statements is
important in the cases in which the order maers because the conguraon statements create a
sequence that is analyzed in order.
As this example shows, you must create the term (or it must already exist) before you can use it with the
insert command. The reference point for placing the term must also exist; for example, to place the term
92

T1 before the term T2, both T1 and T2 must already exist and be populated. Junos OS removes empty
terms automacally.
Requirements
Before you can insert a term, you must congure an inial policy. To quickly congure the inial policy
for this example, copy the following commands, paste them into a text le, remove any line breaks and
change any details necessary to match your network conguraon, copy and paste the commands into
the CLI at the [edit policy-options] hierarchy level, and then enter commit from conguraon mode.
set policy-statement statics term term1 from route-filter 192.168.0.0/16 orlonger
set policy-statement statics term term1 from route-filter 224.0.0.0/3 orlonger
set policy-statement statics term term1 then reject
set policy-statement statics term term2 from protocol direct
set policy-statement statics term term2 then reject
set policy-statement statics term term3 from protocol static
set policy-statement statics term term3 then reject
set policy-statement statics term term4 then accept
Now check to verify that you have the hierarchy congured correctly:
[edit policy-options]
user@host# show
policy-statement statics {
term term1 {
from {
route-filter 192.168.0.0/16 orlonger;
route-filter 224.0.0.0/3 orlonger;
}
then reject;
}
term term2 {
from protocol direct;
then reject;
}
term term3 {
from protocol static;
then reject;
}
term term4 {
then accept;
93

}
}
Overview
To modify a poron of the conguraon in which the statement order maers, you must use the insert
conguraon mode command. If you use the set command instead, the added statement or idener
will be in the wrong place sequenally. The only other way to get the terms of the command in the
correct order is to dismantle the conguraon and start over.
Conguraon
IN THIS SECTION
CLI Quick Conguraon | 94
Congure to Insert Terms | 95
Results | 96
CLI Quick Conguraon
To quickly congure this example, copy the following commands, paste them into a text le, remove any
line breaks and change any details necessary to match your network conguraon, copy and paste the
commands into the CLI at the [edit policy-opons] hierarchy level, and then enter commitin conguraon
mode.
[edit]
user@host# rename policy-options policy-statement statics term term4 to term term6
[edit]
user@host# set policy-options policy-statement statics term term4 from protocol local
[edit]
user@host# set policy-options policy-statement statics term term4 then reject
[edit]
user@host# set policy-options policy-statement statics term term5 from protocol aggregate
[edit]
user@host# set policy-options policy-statement statics term term5 then reject
[edit]
user@host# insert policy-options policy-statement statics term term4 after term term3
94

[edit]
user@host# insert policy-options policy-statement statics term term5 after term term4
Congure to Insert Terms
Step-by-Step Procedure
1. Determine the order in which your conguraon terms need to go. Consider both the original terms
and the new terms you plan to add.
In the original conguraon, the policy is named statics, and there are four terms. Each of the rst
three terms matches on a dierent match criteria, and the resulng matches are rejected. The last
term accepts all the rest of the trac.
In this example, you need to add two terms that eliminate addional types of trac. Both these
terms need to go before the last term in the original conguraon.
2. Rename original term4 to term6.
[edit]
user@host# rename policy-options policy-statement statics term term4 to term term6
This step preserves the original last term, now renamed term6, as the last term.
3. Create a new term4.
[edit]
user@host# set policy-options policy-statement statics term term4 from protocol local
user@host# set policy-options policy-statement statics term term4 then reject
A new term is added that matches trac from local system addresses and rejects it.
4. Create new term5.
[edit]
user@host# set policy-options policy-statement statics term term5 from protocol aggregate
user@host# set policy-options policy-statement statics term term5 then reject
A new term is added that matches trac from aggregate routes and rejects it.
95

5. Insert term4 aer term3.
[edit]
user@host# insert policy-options policy-statement statics term term4 after term term3
6. Insert term5 aer term4.
[edit]
user@host# insert policy-options policy-statement statics term term5 after term term4
Results
[edit]
user@host# show policy-options policy-statement statics
term term1 {
from {
route-filter 192.168.0.0/16 orlonger;
route-filter 224.0.0.0/3 orlonger;
}
then reject;
}
term term2 {
from protocol direct;
then reject;
}
term term3 {
from protocol static;
then accept;
}
term term4 {
from protocol local;
then reject;
}
term term5 {
from protocol aggregate;
then reject;
}
term term6 {
96

then accept;
}
Deacvate and Reacvate Statements and Ideners in a Device
Conguraon
In a Junos OS conguraon, you can deacvate statements and ideners so they do not take eect
when you issue the commit command. Any deacvated statements and ideners are marked with the
inactive tag. They remain in the conguraon but are not acvated when you issue a commit command.
To deacvate a statement or idener, use the deactivate conguraon mode command:
user@host# deactivate( statement | identifier )
To reacvate a statement or idener, use the activate conguraon mode command:
user@host# activate ( statement | identifier )
In both commands, the
statement
and the
identifier
you specify must be at the current hierarchy level.
When you deacvate a statement, that specic statement is ignored and is not applied at all when you
issue a commit command.
To disable a statement, use the disable conguraon mode command.
In some porons of the conguraon hierarchy, you can include a disable statement to disable
funconality. One example is disabling an interface by including the disable statement at the [edit
interface
interface-name
] hierarchy level. When you disable a funcon, it is reacvated when you issue a
commit command but is treated as though it is down or administravely disabled.
97

Example: Deacvate and Reacvate Statements and Ideners in a
Device Conguraon
IN THIS SECTION
Requirements | 98
Overview | 98
Conguraon | 98
This example shows a common use case in which you use the deactivate and activate conguraon mode
commands. It involves dual Roung Engines, primary and backup, that have graceful Roung Engine
switchover (GRES) congured. The soware on both Roung Engines needs to be upgraded. This can
easily be accomplished by deacvang GRES, updang the Roung Engines, and then reacvang
GRES.
NOTE: You can also perform a similar upgrade using the same setup, except that nonstop acve
roung (NSR) is congured instead of GRES. You would need to deacvate NSR and then
upgrade the Roung Engines before reacvang NSR.
Requirements
This example requires the use of a device with dual Roung Engines that can be upgraded.
Before you begin this example, make sure that you have GRES congured.
Overview
In this example, there are two Roung Engines. GRES is congured, and the Roung Engines need to be
upgraded. To accomplish the upgrade, you need to deacvate the GRES feature, upgrade each of the
Roung Engines, and then acvate GRES again.
Conguraon
IN THIS SECTION
Congure the Deacvaon and Reacvaon of GRES | 99
98

Congure the Deacvaon and Reacvaon of GRES
Step-by-Step Procedure
To deacvate and reacvate GRES for Roung Engine upgrade:
1. Show that GRES is enabled for the router.
[edit]
user@host# show chassis
redundancy {
graceful-switchover;
}
fpc 2 {
pic 0 {
tunnel-services {
bandwidth 1g;
}
}
}
2. Deacvate GRES.
[edit]
user@host# deactivate chassis redundancy graceful-switchover
user@host# commit
3. Show that GRES is deacvated.
[edit]
user@host# show chassis
redundancy {
inactive: graceful-switchover;
}
fpc 2 {
pic 0 {
tunnel-services {
bandwidth 1g;
}
99

}
}
4. Upgrade the Roung Engines one by one.
For instrucons on upgrading Junos OS on dual Roung Engines, see Installing the Soware Package
on a Device with Redundant Roung Engines.
5. Reacvate GRES.
[edit]
user@host# activate chassis redundancy graceful-switchover
user@host# commit
Results
Verify that GRES feature is acvated again.
[edit]
user@host# show chassis
redundancy {
graceful-switchover;
}
fpc 2 {
pic 0 {
tunnel-services {
bandwidth 1g;
}
}
}
How to Make Global Changes in the Device Conguraon
You can make global changes to variables and ideners in the device conguraon by using the replace
conguraon mode command. This command replaces a paern in a conguraon with another paern.
100

For example, you can use this command to nd and replace all occurrences of an interface name when a
PIC is moved to another slot in the router.
user@host# replace pattern
pattern1
with
pattern2 <
upto
n>
The pattern
pattern1
opon is a text string or regular expression that denes the ideners and values you
want to replace in the conguraon.
The
pattern2
opon is a text string or regular expression that replaces the ideners and values located
within
pattern1
.
The CLI uses standard UNIX-style regular expression syntax (as dened in POSIX 1003.2). If the regular
expression contains spaces, operators, or wildcard characters, enclose the expression in quotaon
marks. Greedy qualiers (match as much as possible) are supported. Lazy qualiers (match as lile as
possible) are not supported.
The upto
n
opon species the number of objects replaced. The value of
n
controls the total number of
objects that are replaced in the conguraon (not the total number of mes the paern occurs). Objects
at the same hierarchy level (siblings) are replaced rst. Mulple occurrences of a paern within a given
object are considered a single replacement. For example, if a conguraon contains a 010101 text string,
the command replace pattern 01 with pattern 02 upto 2 replaces 010101 with 020202 (instead of 020201).
Replacement of 010101 with 020202 is considered a single replacement (
n
= 1), not three separate
replacements (
n
=3).
If you do not specify an upto opon, all ideners and values in the conguraon that match
pattern1
are
replaced.
The replace command is available in conguraon mode at any hierarchy level. All matches are case-
sensive.
Common Regular Expressions to Use with the replace Command
Table 6: Common Regular Expressions to Use with the replace Command
Operator Funcon
|
Indicates that a match can be one of the two terms on either side of the pipe.
^
Used at the beginning of an expression, denotes where a match should begin.
101

Table 6: Common Regular Expressions to Use with the replace Command
(Connued)
Operator Funcon
$
Used at the end of an expression, denotes that a term must be matched exactly up to the point of the
$ character.
[ ]
Species a range of leers or digits to match. To separate the start and end of a range, use a hyphen
( - ).
( ) Species a group of terms to match. Stored as numbered variables. Use for back references as \1
\2 .... \9.
*
Denotes 0 or more terms.
+
Denotes one or more terms.
.
Denotes any character except for a space (" ").
\ A backslash escapes special characters to suppress their special meaning. For example, \. matches .
(period symbol).
\
n
Back reference that matches the
n
th group.
&
Back reference that matches the enre match.
The following table lists some replacement examples.
Table 7: Replacement Examples
Command Result
replace pattern myrouter with router1 Match: myrouter
Result: router1
102

Table 7: Replacement Examples
(Connued)
Command Result
replace pattern "192\.168\.(.*)/24" with "10.2.\1/28" Match: 192.168.3.4/24
Result: 10.2.3.4/28
replace pattern "1.\1" with "abc&def" Match: 1.1
Result: abc1.1def
replace pattern 1.1 with " abc\&def" Match: 1#1
Result: abc&def
Example: How to Use Global Replace in a Device Conguraon—the \n
Back Reference
IN THIS SECTION
Requirements | 103
Overview | 104
Conguraon | 105
This example shows how you can use a back reference to replace a paern.
Requirements
No special conguraon beyond device iniaon is required before conguring this example.
Before you begin, congure the following:
[edit]
user@host# show interfaces
103

xe-0/0/0 {
unit 0;
}
fe-3/0/1 {
vlan-tagging;
unit 0 {
description "inet6 configuration. IP: 2000::c0a8::1bf5";
vlan-id 100;
family inet {
address 17.10.1.1/24;
}
family inet6 {
address 2000::c0a8:1bf5/3;
}
}
}
To quickly congure this inial conguraon, copy the following commands and paste them in a text le,
remove any line breaks, change any details necessary to match your network conguraon, and then
copy and paste the commands into the CLI at the [edit] hierarchy level:
set interfaces xe-0/0/0 unit 0
set interfaces fe-3/0/1 vlan-tagging
set interfaces fe-3/0/1 unit 0 description "inet6 configuration IP: 2000::c0a8::1bf5"
set interfaces fe-3/0/1 unit 0 vlan-id 100
set interfaces fe-3/0/1 unit 0 family inet address 17.10.1.1/24
set interfaces fe-3/0/1 unit 0 family inet6 address 2000::c0a8:1bf5/3
Overview
One of the most useful features of regular expressions is the back reference. Backreferences provide a
convenient way to idenfy a repeated character or substring within a string. Once you nd the paern,
you can repeat it without wring it again. You refer to the previously captured paern with just \#
(where # is a numeral that indicates the number of mes you want the paern matched).
You can use backreferences to recall, or nd, data and replace it with something else. In this way you can
reformat large sets of data with a single replace command, thus saving you the me it would take to look
for and replace the paern manually.
104

Conguraon
IN THIS SECTION
Conguring a Replacement Using a Back Reference in the Command | 105
Results | 105
Conguring a Replacement Using a Back Reference in the Command
Step-by-Step Procedure
To replace a paern in a Junos OS conguraon using a back reference:
• Use the replace command.
[edit]
user@host# replace pattern
pattern1
with
pattern2
In this case, we want to replace :1bf5with 1bf5.
[edit]
user@host# replace pattern "(.*):1bf5" with "\11bf5"
Noce the back reference (\1), which indicates the paern should be searched for and replaced only
once.
Results
Here is the resulng conguraon:
[edit]
user@host# show interfaces
xe-0/0/0 {
unit 0;
}
fe-3/0/1 {
vlan-tagging;
105

unit 0 {
description "inet6 configuration. IP: 2000::c0a8:1bf5";
vlan-id 100;
family inet {
address 17.10.1.1/24;
}
family inet6 {
address 2000::c0a8:1bf5/3;
}
}
}
In this example, the paern 2000::c0a8::1bf5 is replaced with 2000::c0a8:1bf5 once.
Example: Global Replace in a Device Conguraon—Replacing an
Interface Name
IN THIS SECTION
Requirements | 107
Overview | 107
Conguraon | 107
This example shows how to replace an interface name globally in a conguraon by using the replace
command.
Using the replace command can be a faster and beer way to change a conguraon. For example, a PIC
might be moved to another slot in a router, which changes the interface name. With one command you
can update the whole conguraon. Or you might want to quickly extend the conguraon with other
similar conguraons, for example, similar interfaces.
By using a combinaon of the copy and replace commands, you can add to a conguraon and then
replace certain aspects of the newly copied conguraons. The replace command works with regular
expressions. Regular expressions are quick, exible, and ubiquitous. You can fashion just about any
paern you might need to search for, and most programming languages support regular expressions.
106

Requirements
No special conguraon beyond device inializaon is required before conguring this example.
Before you begin, congure the following hierarchy on the router. To quickly congure this hierarchy,
see "CLI Quick Conguraon" on page 108 .
user@host# show interfaces
so-0/0/0 {
dce;
}
user@host# show protocols
ospf {
area 0.0.0.0 {
interface so-0/0/0.0 {
hello-interval 5;
}
}
}
Overview
This example shows how to replace an interface name globally in a conguraon by using the replace
command. It is a simple example.
The previous conguraon is the starng point for this conguraon update. In the course of this
example, you change the name of the inial interface throughout the conguraon with one command.
Conguraon
IN THIS SECTION
CLI Quick Conguraon | 108
Conguring an Interface Name Change | 108
Results | 108
107

CLI Quick Conguraon
To quickly congure the inial conguraon for this example, copy the following commands, paste them
into a text le, remove any line breaks and change any details necessary to match your network
conguraon, copy and paste these commands into the CLI at the [edit] hierarchy level, and then enter
commit from conguraon mode.:
set interfaces so-0/0/0 dce
set protocols ospf area 0.0.0.0 interface so-0/0/0.0 hello-interval 5
Conguring an Interface Name Change
Step-by-Step Procedure
To change an interface name:
1. Make sure that you are at the top of the conguraon mode hierarchy.
user@host# top
2. Replace so-0/0/0 with so-1/1/0 using the replace command, which uses the pattern keyword.
user@host# replace pattern so-0/0/0 with so-1/1/0
Results
Aer making the required changes, verify the conguraon by using the show interfaces and show protocols
conguraon mode commands.
[edit]
user@host# show interfaces
so-1/1/0 {
dce;
}
user@host# show protocols
ospf {
area 0.0.0.0 {
108

interface so-1/1/0.0 {
hello-interval 5;
}
}
}
Aer you have conrmed that the conguraon is correct, enter the commit command.
Example: Global Replace in a Device Conguraon—the upto Opon
Consider the hierarchy shown in Figure 3 on page 110. The text string 010101 appears in three places: the
descripon secons of ge-0/0/0, ge-0/0/0.0, and fe-0/0/1. These three instances are three objects. The
following example shows how you can use the upto opon to perform replacements in a device
conguraon:
109

Figure 3: Replacement by Object
An upto 2 opon in the replace command converts 01 to 02 for two object instances. The objects under the
main interfaces ge-0/0/0 and fe-0/0/1 will be replaced rst (since these are siblings in the hierarchy level).
Because of the upto 2 restricon, the replace command replaces paerns in the rst and second instance
in the hierarchy (siblings), but not the third instance (child of the rst instance).
user@host# show interfaces
ge-0/0/0 {
description "mkt 010101"; #First instance in the hierarchy
unit 0 {
110

description "mkt 010101"; #Third instance in the hierarchy (child of the first
instance)
}
}
fe-0/0/1 {
description "mkt 010101"; #second instance in the hierarchy (sibling of the first
instance)
unit 0 {
family inet {
address 200.200.20.2/24;
}
}
}
[edit]
user@host# replace pattern 01 with 02 upto 2
[edit]
user@host# commit
commit complete
[edit]
user@host# show interfaces
ge-0/0/0 {
description "mkt 020202"; #First instance in the hierarchy
unit 0 {
description "mkt 010101"; #Third instance in the hierarchy (child of the first
instance)
}
}
fe-0/0/1 {
description "mkt 020202"; #second instance in the hierarchy (sibling of the first
instance)
unit 0 {
family inet {
address 200.200.20.2/24;
}
}
}
111

Add Comments in a Device Conguraon
IN THIS SECTION
Add Comments in the CLI | 112
Add Comments in a File | 113
You can include comments in a device conguraon to describe any statement in the conguraon. You
can add comments interacvely in the CLI and by eding the ASCII conguraon le.
When conguring interfaces, you can add comments about the interface by including the description
statement at the [edit interfaces
interface-name
] hierarchy level. Any comments you include appear in the
output of the show interfaces commands..
Add Comments in the CLI
When you add comments in conguraon mode, they are associated with a statement at the current
level. Each statement can have one single-line comment associated with it. Before you can associate a
comment with a statement, the statement must exist. The comment is placed on the line preceding the
statement.
To add comments to a conguraon, use the annotate conguraon mode command:
user@host# annotate
statement
"
comment-string
"
statement
is the conguraon statement to which you are aaching the comment; it must be at the
current hierarchy level. If a comment for the specied
statement
already exists, it is deleted and replaced
with the new comment.
comment-string
is the text of the comment. The comment text can be any length, and you must type it on a
single line. If the comment contains spaces, you must enclose it in quotaon marks. In the comment
string, you can include the comment delimiters /* */ or #. If you do not specify any, the comment string
is enclosed with the /* */ comment delimiters.
To delete an exisng comment, specify an empty comment string:
user@host# annotate
statement
""
112

If you add comments with the annotate command, you can view the comments within the conguraon
by entering the show conguraon mode command or the show configuration operaonal mode
command.
NOTE: Junos OS supports annotaon up to the last level in the conguraon hierarchy, including
oneliners. However, annotaon of parts (the child statements or ideners within the oneliner)
of the oneliner is not supported. For example, in the following sample conguraon hierarchy,
annotaon is supported up to the level 1 parent hierarchy, but not supported for the metric child
statement:
[edit protocols]
isis {
interface ge-0/0/0.0 {
level 1 metric
10
;
}
}
}
Add Comments in a File
When you edit the ASCII conguraon le and add comments, they can be one or more lines and must
precede the statement they are associated with. If you place the comments in other places in the le,
such as on the same line following a statement or on a separate line following a statement, they are
removed when you use the load command to open the conguraon into the CLI.
The following excerpt from a conguraon example illustrates how to place and how not to place
comments in a conguraon le:
/* This comment goes with routing-options */
routing-options {
/* This comment goes with routing-options traceoptions */
traceoptions {
/* This comment goes with routing-options traceoptions tracefile */
tracefile rpd size 1m files 10;
/* This comment goes with routing-options traceoptions traceflag task */
traceflag task;
/* This comment goes with routing-options traceoptions traceflag general */
traceflag general;
}
autonomous-system 10458; /* This comment is dropped */
}
113

routing-options {
rib-groups {
ifrg {
import-rib [ inet.0 inet.2 ];
/* A comment here is dropped */
}
dvmrp-rib {
import-rib inet.2;
export-rib inet.2;
/* A comment here is dropped */
}
/* A comment here is dropped */
}
/* A comment here is dropped */
}
When you include comments in the conguraon le directly, you can format comments in the following
ways:
• Start the comment with a /* and end it with a */. The comment text can be on a single line or can
span mulple lines.
• Start the comment with a # and end it with a new line (carriage return).
Example: Include Comments in a Device Conguraon by Using the CLI
IN THIS SECTION
Requirements | 115
Overview | 115
Conguraon | 115
Adding comments to a device conguraon makes the conguraon le readable and more readily
understood by users. You can include comments as you congure by using the annotate statement. In this
example, comments are added by using the CLI for an already exisng conguraon:
114
Requirements
No special conguraon beyond device inializaon is required before conguring this example.
Before you add a comment, you must congure the following hierarchy on the router.
To quickly congure the inial conguraon for this example, copy the following command, paste it into
a text le, remove any line breaks and change any details necessary to match your network
conguraon, copy and paste this command into the CLI at the [edit] hierarchy level, and then enter
commit from conguraon mode.
set protocols ospf area 0.0.0.0 interface so-0/0/0.0 hello-interval 5
Now verify that you have this hierarchy congured.
user@host# show protocols
ospf {
area 0.0.0.0 {
interface so-0/0/0 {
hello-interval 5;
}
}
}
Overview
When you add comments by using the CLI, you do so in conguraon mode using the annotate
statement. Each comment you add is associated with a statement at the current level. Each statement
can have one single-line comment associated with it.
To congure the annotate statement, move to the level of the statement with which you want to associate
a comment. To view the comments, go to the top of the conguraon hierarchy and use the show
command.
Conguraon
IN THIS SECTION
CLI Quick Conguraon | 116
Including Comments in the CLI Conguraon Mode | 116
115

Results | 117
CLI Quick Conguraon
To quickly congure the comments for this example, copy the following commands, paste them into a
text le, remove any line breaks and change any details necessary to match your network conguraon,
copy and paste the commands into the CLI, starng at the [edit] hierarchy level, and then enter commit
from conguraon mode.
edit protocols ospf
annotate area 0.0.0.0 "Backbone area configuration added June 15, 2018"
edit area 0.0.0.0
annotate interface so-0/0/0.0 "Interface from router sj1 to router sj2"
Noce that the commands are moving you down the hierarchy as you annotate dierent secons of the
hierarchy.
Including Comments in the CLI Conguraon Mode
Step-by-Step Procedure
This procedure assumes that you have already congured the inial conguraon.
To add comments to a conguraon:
1. Move to the rst hierarchy level to which you need to add a comment.
[edit]
user@host# edit protocols ospf
2.
Add a comment to the area conguraon statement by using the annotate statement.
[edit protocols ospf]
user@host# annotate area 0.0.0.0 "Backbone area configuration added June 15, 1998"
116

3. Move down a level to the interface conguraon statement.
[edit protocols ospf]
user@host# edit area 0.0.0.0
4. Add a comment to interface so-0/0/0.0 by using the annotate statement.
[edit protocols ospf area 0.0.0.0]
user@host# annotate interface so-0/0/0.0 "Interface from router sj1 to router sj2"
Results
Move to the top of the hierarchy and use the show command to see the comments you added. The
comments precede the statement they are associated with.
[edit]
user@host# show protocols
ospf {
/* Backbone area configuration added June 15, 2018 */
area 0.0.0.0 {
/* Interface from router sj1 to router sj2 */
interface so-0/0/0.0 {
hello-interval 5;
}
}
}
Aer you have conrmed that the conguraon is correct, enter the commit command.
Example: Use the Wildcard Command with the Range Opon
IN THIS SECTION
Requirements | 118
Overview | 118
117

Conguraon | 118
If you need to make changes to the conguraon of a device, you can always remove the original
conguraon sengs using the delete command and add your new conguraon sengs using the set
command. However, there are other ways of modifying a conguraon that are more ecient and easier
to use.
This example shows how to use the wildcard command along with ranges in acvate, deacvate, delete,
protect, set, show, and unprotect conguraon commands.
NOTE: The wildcard command cannot create a conguraon hierarchy. You use it to modify
exisng statements. Expect CLI errors of the form warning: statement not found when you try to set
parameters, such as deacvate, on an empty hierarchy.
Requirements
Junos OS Release 12.1 or later running on the device.
Overview
The range opon with the wildcard command enables you to specify ranges in acvate, deacvate,
delete, protect, set, show, and unprotect commands. You can use ranges to specify a range of interfaces,
logical units, VLANs, and other numbered elements. The wildcard range opon expands the command
you entered into mulple commands, each of which corresponds to one item in the range.
The wildcard range opon enables you to congure mulple conguraon statements using a single set
command, instead of conguring each of them individually. For example, to congure 24 Gigabit
Ethernet interfaces with dierent port numbers, you can use a single wildcard range set command
instead of 24 individual set interfaces commands.
Similarly, to deacvate a group of 30 logical interfaces, you can use the wildcard range deacvate
command instead of deacvang each logical interface individually.
Conguraon
IN THIS SECTION
Use the wildcard command with range statements for a variety of conguraon tasks. | 119
118

Using the Range Opon for Conguring a Series of Named Ideners for a Conguraon
Statement | 120
Specifying Mulple Ranges in the Syntax | 121
Specifying a Range and Unique Numbers In the Syntax | 123
Excluding Some Values from a Range | 124
Specifying a Range with a Step Number | 125
Use Wildcard to Delete Policies p1-p10 | 126
Use the wildcard command with range statements for a variety of conguraon tasks.
Step-by-Step Procedure
1. You can use wildcard range with the acve, deacvate, delete, protect, set, show, and unprotect
conguraon commands.
[edit]
user@host# wildcard range ?
Possible completions:
activate Remove the inactive tag from a statement
annotate Annotate the statement with a comment
deactivate Add the inactive tag to a statement
delete Delete a data element
protect Protect the statement
set Set a parameter
show Show a parameter
unprotect Unprotect the statement
2. The wildcard statement can be qualied with a full conguraon hierarchy. When parked at a
conguraon hierarchy, the wildcard command is relave to the opons supported at that hierarchy.
[edit]
user@host# wildcard range set interfaces ?
Possible completions:
<interface-name> Interface name
+ apply-groups Groups from which to inherit configuration data
+ apply-groups-except Don't inherit configuration data from these groups
119

> interface-range Interface ranges configuration
> interface-set Logical interface set configuration
lo0 Interface name
> stacked-interface-set Stacked interface set configuration
> traceoptions Interface trace options
xe-0/0/0:0 Interface name
xe-0/0/0:1 Interface name
user@host# edit interfaces
[edit interfaces]
wildcard range set ?
Possible completions:
<interface-name> Interface name
+ apply-groups Groups from which to inherit configuration data
+ apply-groups-except Don't inherit configuration data from these groups
> interface-range Interface ranges configuration
> interface-set Logical interface set configuration
lo0 Interface name
> stacked-interface-set Stacked interface set configuration
> traceoptions Interface trace options
xe-0/0/0:0 Interface name
xe-0/0/0:1 Interface name
In the rst case the full path to the interfaces hierarchy is specied with the wildcard statement. In
the second, the user is parked at the interfaces hierarchy. The opons supported are the same with
either method.
Using the Range Opon for Conguring a Series of Named Ideners for a Conguraon Statement
Step-by-Step Procedure
To congure a series of the same type of interface with dierent port numbers (0 through 23), specify
the range for the port numbers with the following format.
1. [edit]
user@host# wildcard range set interfaces ge-0/0/[0-23] unit 0 family vpls
2. Display the result. The range wildcard range is expanded to 24 dierent set commands to congure
interfaces with port numbers ranging from 0 through 23. In this case the interfaces are created in
120

order to add the vpls protocol family. If the interfaces are already dened then just the family is
added.
root@R1# show | compare
[edit interfaces]
+ ge-0/0/0 {
+ unit 0 {
+ family vpls;
+ }
+ }
+ ge-0/0/1 {
+ unit 0 {
+ family vpls;
+ }
+ }
+ ge-0/0/2 {
+ unit 0 {
+ family vpls;
+ }
+ }
. . .
+ ge-0/0/23 {
+ unit 0 {
+ family vpls;
+ }
Specifying Mulple Ranges in the Syntax
Step-by-Step Procedure
You can have mulple ranges specied in a wildcard range command. Each range must be separated by a
comma. You can also have overlapping ranges.
NOTE: For the remaining examples you create a temporary copy of your conguraon with ten
policy statements. Having these statements avoids CLI errors that are reported when you try to
manipulate aributes in a null poron of the hierarchy.
[edit]
user@device# set policy-options policy-statement p1 then reject
121

set policy-options policy-statement p10 then reject
set policy-options policy-statement p2 then reject
set policy-options policy-statement p3 then reject
set policy-options policy-statement p4 then reject
set policy-options policy-statement p5 then reject
set policy-options policy-statement p6 then reject
set policy-options policy-statement p7 then reject
set policy-options policy-statement p8 then reject
set policy-options policy-statement p9 then reject
[edit]
user@device# save temp
Wrote 254 lines of configuration to 'temp'
1. To specify more than one range in the syntax, include the minimum and maximum values for each
range, separated by a comma.
[edit]
user@host# wildcard range deactivate policy-options policy-statement p[1-3,5-7,6-9]
2. Display the result. The wildcard range expands to add the deactivate statement to policies that have
names matching the specied ranges. Of note is the absence of
p4
and
p10
in the list of changes to
the candidate conguraon.
NOTE: An error is returned if the policy name specied does not already exist in the
conguraon. This is because you cannot add the deacvate statement to an empty poron
of the conguraon hierarchy.
[edit]
show | compare
[edit policy-options]
! inactive: policy-statement p1 { ... }
! inactive: policy-statement p2 { ... }
! inactive: policy-statement p3 { ... }
! inactive: policy-statement p5 { ... }
! inactive: policy-statement p6 { ... }
! inactive: policy-statement p7 { ... }
122

! inactive: policy-statement p8 { ... }
! inactive: policy-statement p9 { ... }
Specifying a Range and Unique Numbers In the Syntax
Step-by-Step Procedure
You can specify a combinaon of a range and unique numbers in the syntax of the wildcard range
command.
1. Reload the "temporary conguraon" on page 121.
[edit]
user@host# load override temp
load complete
1. To specify a range and a unique number, separate them with a comma. In this example 10 is added as
a unique number to a series of ranges.
[edit]
user@host# wildcard range deactivate policy-options policy-statement p[1-3,5,7,10]
2. Display the result. The wildcard range expands to add the deactivate statement to policies that have
names matching the specied ranges and also to the unique number. As a result the
p10
policy is also
deacvated in this example.
NOTE: An error is returned if the policy name specied does not already exist in the
conguraon. This is because you cannot add the deacvate statement to a empty
conguraon hierarchy.
[edit]
user@host# show | compare
[edit policy-options]
! inactive: policy-statement p1 { ... }
! inactive: policy-statement p10 { ... }
! inactive: policy-statement p2 { ... }
! inactive: policy-statement p3 { ... }
123

! inactive: policy-statement p5 { ... }
! inactive: policy-statement p7 { ... }
Excluding Some Values from a Range
Step-by-Step Procedure
You can exclude certain values from a range by marking the numbers or the range of numbers to be
excluded by using an exclamaon mark.
1. Reload the "temporary conguraon" on page 121.
[edit]
user@host# load override temp
load complete
2. To exclude certain values from a range, include the poron to be excluded with ! in the syntax.
[edit]
user@host# wildcard range deactivate policy-options policy-statement p[1-5,!3-4]
3. Display the result. The wildcard range expands to add the deactivate statement to policies that have
names matching the specied ranges. Note that policies
p3
and
p4
are absent in the list of
modicaons made to the candidate conguraon. They have been excluded from the wildcard
range.
NOTE: An error is returned if the policy name specied does not already exist in the
conguraon. This is because you cannot add the deacvate statement to a empty
conguraon hierarchy.
[edit]
user@host# show | compare
[edit policy-options]
! inactive: policy-statement p1 { ... }
! inactive: policy-statement p2 { ... }
! inactive: policy-statement p5 { ... }
124

Specifying a Range with a Step Number
Step-by-Step Procedure
You can provide a step number to have a constant interval in the range. The step value counts the rst
match, and then skips subsequent matches up to the specied step value.
1. Reload the "temporary conguraon" on page 121.
[edit]
user@host# load override temp
load complete
2. To provide a step, include the step value in the syntax preceded by a forward slash (/). Here we
specify a range of 1-10, skipping 1 number between each match using a step value of 2. The eect is
to skip all even numbered matches as we begin by matching an odd number (1).
[edit]
user@host# wildcard range deactivate policy-options policy-statement p[1-10/2]
3. Display the result. The wildcard range expands to add the deactivate statement to every other
matching statement, starng with the rst match.
NOTE: An error is returned if the policy name specied does not already exist in the
conguraon. This is because you cannot add the deacvate statement to a empty
conguraon hierarchy.
[edit]
user@host# show | compare
[edit policy-options]
! inactive: policy-statement p1 { ... }
! inactive: policy-statement p3 { ... }
! inactive: policy-statement p5 { ... }
! inactive: policy-statement p7 { ... }
! inactive: policy-statement p9 { ... }
125

To beer illustrate the step funcon, the temporary conguraon is restore and the wildcard
command is repeated, this me with a step value of 4. Now 3 entries are skipped aer each inial
match.
[edit]
user@host# load override temp
load complete
user@host## wildcard range deactivate policy-options policy-statement p[1-10/4]
\
4. Display the result. The wildcard range expands to add the deactivate statement to every fourth
matching statement, starng with the rst match.
[edit]
user@host# show | compare
[edit policy-options]
! inactive: policy-statement p1 { ... }
! inactive: policy-statement p5 { ... }
! inactive: policy-statement p9 { ... }
Use Wildcard to Delete Policies p1-p10
Step-by-Step Procedure
Delete the temporary policies added to test the wildcard funcon.
1. Use the delete statement with a wildcard range statement to delete policies
p1
through
p10
.
[edit]
user@host# wildcard range delete policy-options policy-statement p[1-10]
2.
Display the result. Our policy-options stanza contained only policies
p1
through
p10
. This results in an
empty policy-optionsconguraon hierarchy.
[edit]
user@host# show policy-options
126

Use Conguraon Groups to Quickly Congure
Devices
IN THIS SECTION
Conguraon Groups Overview | 128
Congure Conguraon Groups | 129
Create a Conguraon Group | 129
How to Apply a Conguraon Group | 131
Example: Create and Apply Conguraon Groups | 132
Example: Disable Inheritance of a Conguraon Group | 134
Example: Use the junos-defaults Conguraon Group | 136
Example: Use Wildcards with Conguraon Groups | 139
How to Improve Commit Time When Using Conguraon Groups | 142
Example: Congure Sets of Statements with Conguraon Groups | 143
Example: Congure Interfaces Using Conguraon Groups | 144
Example: Use Conguraon Groups to Congure a Consistent IP Address for the Management
Interface | 147
Example: Use Conguraon Groups to Congure Peer Enes | 149
Example: Use Conguraon Groups to Establish Regional Conguraons | 151
Example: Congure Wildcard Conguraon Group Names | 152
Example: Reference the Preset Statement from the Defaults Group | 154
Example: View Default Statements That Have Been Applied to the Conguraon | 155
Set Up Roung Engine Conguraon Groups | 156
How to Use Condions to Apply Conguraon Groups | 158
Example: Congure Condions for Applying Conguraon Groups | 159
Use conguraon groups to set up and apply common elements that are reused within the same
conguraon.
127

Conguraon Groups Overview
IN THIS SECTION
How Conguraon Groups Work | 128
Inheritance Model | 128
This topic provides an overview of conguraon groups and the inheritance model in the Junos OS CLI.
How Conguraon Groups Work
Conguraon groups enable you to create a group containing conguraon statements and to direct the
inheritance of that group’s statements in the rest of the conguraon. The same group can be applied to
dierent secons of the conguraon. Dierent secons of one group’s conguraon statements can
be inherited in dierent places in the conguraon.
Conguraon groups enable you to create smaller, more logically constructed conguraon les, making
it easier to congure and maintain Juniper Networks devices. For example, you can group statements
that are repeated in many places in the conguraon, such as when conguring interfaces. By grouping
statements, you can limit conguraon updates to just the group.
You can also use wildcards in a conguraon group. Any object that matches the wildcard expression
inherits the group conguraon data.
The conguraon group mechanism is separate from the grouping mechanisms used elsewhere in the
conguraon, such as BGP groups. Conguraon groups provide a generic mechanism that you can use
throughout the conguraon but that are known only to the CLI. The individual soware processes that
perform the acons directed by the conguraon receive the expanded form of the conguraon; they
have no knowledge of conguraon groups.
Inheritance Model
Conguraon groups use true inheritance, which involves a dynamic, ongoing relaonship between the
source of the conguraon data and the target of that data. The target automacally inherits data values
that you change in the conguraon group. The target does not need to contain the inherited
informaon. However, the inherited values can be overridden in the target without aecng the source
from which they were inherited.
This inheritance model enables you to see only the instance-specic informaon without seeing the
inherited details. A command pipe in conguraon mode enables you to display the inherited data.
128

Congure Conguraon Groups
For areas of your conguraon to inherit conguraon statements, you must rst put the statements
into a conguraon group. You then apply that group to the levels in the conguraon hierarchy that
require the statements.
For areas of your conguraon to inherit conguraon statements:
1. Congure statements into a conguraon group. To congure conguraon groups and inheritance,
you can include the groups statement at the [edit] hierarchy level:
[edit]
groups {
group-name
{
configuration-data
;
}
}
2. Apply the conguraon group from step 1 to the levels in the conguraon hierarchy that require the
statements.
Include the apply-groups [
group-names
] statement anywhere in the conguraon where the
conguraon statements contained in a conguraon group are needed.
Create a Conguraon Group
The Junos OS CLI enables you to create re-usable groups containing conguraon statements. You can
apply these groups to to dierent secons of the conguraon where the same conguraon
statements are repeated mulple mes.
When you apply the group in dierent secons of the conguraon, that part of the conguraon
inherits the statements congured in the group. Conguraon groups follow the rule of inheritance
where the dynamic, ongoing relaonship is set between the source of the conguraon data and the
target of that data. If you change the data values in the conguraon group, the inherited target reects
the changes automacally.
You can overwrite the values in the target conguraon if required, which does not aect the source in
the group.
129

This inheritance model enables you to see only the instance-specic informaon without seeing the
inherited details. A command pipe in conguraon mode enables you to display the inherited data. For
example, you may want to congure all of your ge-0/0/1 interfaces for the MTU value of 1500.
To do congure all of your ge-0/0/1 interfaces for the MTU value of 1500:
1. Create a group with MTU value 1500:
[edit groups group-1]
lab@vSRX3-05# show
interfaces {
ge-0/0/1 {
unit 0 {
family inet {
mtu 1500;
}
}
}
}
2. Next, you apply the group in the interface conguraon.
[edit interfaces ge-0/0/1]
lab@vSRX3-05# set apply-groups group-1
3. View the inherited conguraon.
[edit]
lab@vSRX3-05# show interfaces ge-0/0/1 | display inheritance
unit 0 {
family inet {
##
## '1500' was inherited from group 'group-1'
##
mtu 1500;
address 5.0.0.254/24;
}
}
130

If you want to congure MTU value for interface ge-0/0/1 in dierent parts of the conguraon, you can
apply the group statement using the apply-groups opon. If you do this manually and later want to
increase the MTU, you may have to manually change every interface. If you use a conguraon group,
you can change the group conguraon, thereby automacally updang all associated interfaces.
You can also use wildcards in a conguraon group to allow conguraon data to be inherited by any
object that matches a wildcard expression. For example:
[edit groups group-1]
lab@vSRX3-05# show
interfaces {
ge-* {
unit 0 {
family inet {
mtu 1500;
}
}
}
}
How to Apply a Conguraon Group
If you want a Juniper Networks device conguraon to inherit the statements from a conguraon
group, include the apply-groups statement in the conguraon.
apply-groups [
group-names
];
If you specify more than one group name, you must list the names in order of inheritance priority. The
conguraon data in the rst group takes priority over the data in subsequent groups.
For devices that support mulple Roung Engines, you can specify re0 and re1 group names. The
conguraon specied in group re0 is applied only if the current Roung Engine is in slot 0. Likewise, the
conguraon specied in group re1 is applied only if the current Roung Engine is in slot 1. Therefore,
both Roung Engines can use the same conguraon le, each using only the conguraon statements
that apply to it. Each re0 or re1 group contains at a minimum the conguraon for the hostname and the
management interface (fxp0). If each Roung Engine uses a dierent management interface, the group
also should contain the conguraon for the backup router and stac routes.
131

You can include only one apply-groups statement at each specic level of the conguraon hierarchy. The
apply-groups statement at a specic hierarchy level lists the conguraon groups to be added to the
containing statement’s list of conguraon groups.
Values specied at the specic hierarchy level override values inherited from the conguraon group.
Groups listed in nested apply-groups statements take priority over groups in outer statements. In the
following example, the BGP neighbor 10.0.0.1 inherits conguraon data from group one rst. It then
inherits conguraon data from group two and group three. Conguraon data in group one overrides data
in any other group. Data from group ten is used only if a statement is not contained in any other group.
apply-groups [ eight nine ten ];
protocols {
apply-groups seven;
bgp {
apply-groups [ five six ];
group some-bgp-group {
apply-groups four;
neighbor 10.0.0.1 {
apply-groups [ one two three ];
}
}
}
}
The root level is the default logical system. When you congure a group dened for the root level, you
cannot successfully apply that group to a nondefault logical system under the [edit logical-systems
logical-system-name
] hierarchy level. Although the device accepts the commit if you apply the group, the
conguraon group does not take eect for the nondefault logical system. You can instead create an
addional conguraon group at the root level and apply it within the logical system. Alternavely, you
can modify the original group so that it includes conguraon for both the default and nondefault logical
system hierarchy levels.
Example: Create and Apply Conguraon Groups
This example illustrates the creaon and applicaon of conguraon groups. In this example, the SNMP
conguraon is divided between the group basic and the normal conguraon hierarchy.
You gain mulple advantages by placing the system-specic conguraon (SNMP contact) into a
conguraon group, thus separang it from the normal conguraon hierarchy:
132

• You can replace either secon without discarding data from the other, by using the load replace
command.
• You can set a contact for a specic box because the group data is hidden by the device-specic data.
[edit]
groups {
basic { # User-defined group name
snmp { # This group contains some SNMP data
contact "My Engineering Group";
community BasicAccess {
authorization read-only;
}
}
}
}
apply-groups basic; # Enable inheritance from group "basic"
snmp { # Some normal (non-group) configuration
location "West of Nowhere";
}
This conguraon is equivalent to the following:
[edit]
snmp {
location "West of Nowhere";
contact "My Engineering Group";
community BasicAccess {
authorization read-only;
}
}
133

Example: Disable Inheritance of a Conguraon Group
You can disable inheritance of a conguraon group at any level except the top level of the hierarchy. To
disable inheritance, you include the apply-groups-except statement in the conguraon:
apply-groups-except [
group-names
];
This statement is useful when you use the apply-group statement at a specic hierarchy level but also
want to override the values inherited from the conguraon group for a specic parameter.
Example: Disable Inheritance on Interface so-1/1/0
In the following example, the apply-groups statement is applied globally at the interfaces level. The apply-
groups-except statement is also applied at interface so-1/1/0 so that it uses the default values for the hold-
time and link-mode statements.
[edit]
groups { # "groups" is a top-level statement
global { # User-defined group name
interfaces {
<*> {
hold-time down 640;
link-mode full-duplex;
}
}
}
}
apply-groups global;
interfaces {
so-1/1/0 {
apply-groups-except global; # Disables inheritance from group "global"
# so-1/1/0 uses default value for “hold-time”
# and "link-mode"
}
}
Conguraon groups can add some confusion regarding the actual values used by the device, because a
device can inherit conguraon data from conguraon groups. To view the actual values used by the
device, you use the display inheritance command aer the pipe ( | ) in a show command. This command
134

displays the inherited statements at the level at which they are inherited and the group from which they
have been inherited:
[edit]
user@host# show | display inheritance
snmp {
location "West of Nowhere";
##
## 'My Engineering Group' was inherited from group 'basic'
##
contact "My Engineering Group";
##
## 'BasicAccess' was inherited from group 'basic'
##
community BasicAccess {
##
## 'read-only' was inherited from group 'basic'
##
authorization read-only;
}
}
To display the expanded conguraon (the conguraon, including the inherited statements) without
the ## lines, you use the except command aer the pipe in a show command:
[edit]
user@host# show | display inheritance | except ##
snmp {
location "West of Nowhere";
contact "My Engineering Group";
community BasicAccess {
authorization read-only;
}
}
NOTE: Using the display inheritance | except ## opon removes all the lines with ##. Therefore, you
may not be able to view informaon about passwords or other important data where ## is used.
To view the complete conguraon details with all the informaon (without just the comments
marked with ##), you use the no-comments opon with the display inheritance command:
135

[edit]
user@host# show | display inheritance no-comments
snmp {
location "West of Nowhere";
contact "My Engineering Group";
community BasicAccess {
authorization read-only;
}
}
Example: Use the junos-defaults Conguraon Group
Junos OS provides a hidden and immutable conguraon group called junos-defaults that is automacally
applied to the conguraon of your device. The junos-defaults group contains precongured statements
that contain predened values for common applicaons. Some of the statements must be referenced to
take eect, such as denions for applicaons (for example, FTP or telnet sengs). Other statements
are applied automacally, such as terminal sengs.
NOTE: Many ideners included in the junos-defaults conguraon group begin with the name
junos-. Because ideners beginning with the name junos- are reserved for use by Juniper
Networks, you cannot dene any conguraon objects using this name.
You cannot include junos-defaults as a conguraon group name in an apply-groups statement.
To view the full set of available preset statements from the junos-defaults group, you issue the show groups
junos-defaults conguraon mode command at the top level of the conguraon. The following example
displays a paral list of Junos defaults groups:
user@host# show groups junos-defaults
# Make vt100 the default for the console port
system {
ports {
console type vt100;
}
}
applications {
136

# File Transfer Protocol
application junos-ftp {
application-protocol ftp;
protocol tcp;
destination-port 21;
}
# Trivial File Transfer Protocol
application junos-tftp {
application-protocol tftp;
protocol udp;
destination-port 69;
}
# RPC port mapper on TCP
application junos-rpc-portmap-tcp {
application-protocol rpc-portmap;
protocol tcp;
destination-port 111;
}
# RPC port mapper on UDP
}
To reference statements available from the junos-defaults group, you include the selected junos-
default-
name
statement at the applicable hierarchy level.
To view the list of applicaons from the junos-defaults group, you issue the show configuration groups junos-
defaults applications. The applicaons that begin with junos- are congured by Juniper Networks by
default. The following example displays a paral list of Junos defaults groups applicaons.
user@host>show configuration groups junos-defaults applications
## protect: groups junos-defaults
##
#
# File Transfer Protocol
#
application junos-ftp {
application-protocol ftp;
protocol tcp;
destination-port 21;
}
#
# Trivial File Transfer Protocol
#
137

application junos-ftp-data {
application-protocol ftp-data;
protocol tcp;
destination-port 20;
}
application junos-tftp {
application-protocol tftp;
protocol udp;
destination-port 69;
}
#
# Two-Way Active Measurement Protocol
#
application junos-twamp {
application-protocol twamp;
protocol tcp;
destination-port 862;
}
#
# Real Time Streaming Protocol
#
application junos-rtsp {
application-protocol rtsp;
protocol tcp;
destination-port 554;
}
#
# Network Basic Input Output System - networking protocol used on
# Windows networks session service port
#
application junos-netbios-session {
protocol tcp;
destination-port 139;
}
application junos-smb-session {
protocol tcp;
destination-port 445;
}
application junos-ssh {
protocol tcp;
destination-port 22;
}
application junos-telnet {
138

protocol tcp;
destination-port 23;
}
Example: Use Wildcards with Conguraon Groups
You can use wildcards to idenfy names and allow one statement to provide data for a variety of
statements.
Using wildcards in normal conguraon data is done in a style that is consistent with that used with
tradional UNIX shell wildcards. In this style, you can use the following metacharacters:
• Asterisk ( * )—Matches any string of characters.
• Queson mark ( ? )—Matches any single character.
• Open bracket ( [ )—Introduces a character class.
• Close bracket ( ] )—Indicates the end of a character class. If the close bracket is missing, the open
bracket matches an open bracket [ rather than introducing a character class.
• A character class matches any of the characters between the square brackets. Within a conguraon
group, you must enclose in quotaon marks an interface name that includes a character class.
• Hyphen ( - )—Species a range of characters.
• Exclamaon point ( ! )—You can complement the character class by making an exclamaon point the
rst character of the character class. To include a close bracket (]) in a character class, make it the
rst character listed (aer the !, if any). To include a minus sign, make it the rst or last character
listed.
NOTE: If using an idener inside the groups hierarchy, start the idener name with something
other than <. However, if you are dening a wildcard statement, you can use < because the
wildcard statement must have a closing >.
Using wildcards in conguraon groups follows the same rules as using them for normal conguraon.
However, < and > have a special meaning when used under the groups hierarchy. In the groups hierarchy,
139

you must enclose in angle brackets any term using a wildcard paern <
paern
> to dierenate it from
other wildcards in the conguraon le.
[edit]
groups {
sonet-default {
interfaces {
<so-*> {
sonet-options {
payload-scrambler;
rfc-2615;
}
}
}
}
}
Wildcard expressions match (and provide conguraon data for) exisng statements in the conguraon
that match their expression only. In the previous example, the expression <so-*> passes its sonet-options
statement to any interface that matches the expression so-*.
The following example shows how to specify a range of interfaces:
[edit]
groups {
gigabit-ethernet-interfaces {
interfaces {
"<ge-1/2/[5-8]>" {
description "These interfaces reserved for Customer ABC";
}
}
}
}
Angle brackets enable you to pass normal wildcards through without modicaon. In any matching
within the conguraon, whether it is done with or without wildcards, the rst item encountered in the
conguraon that matches is used. In the following example, data from the wildcarded BGP groups is
inherited in the order in which the groups are listed.
•
The preference value from <*a*> overrides the preference in <*b*>.
• The p value from <*c*> overrides the one from <*d*>
140

Data values from any of these groups override the data values from abcd:
[edit]
user@host# show
groups {
one {
protocols {
bgp {
group <*a*> {
preference 1;
}
group <*b*> {
preference 2;
}
group <*c*> {
out-delay 3;
}
group <*d*> {
out-delay 4;
}
group abcd {
preference 10;
hold-time 10;
out-delay 10;
}
}
}
}
}
protocols {
bgp {
group abcd {
apply-groups one;
}
}
}
[edit]
user@host# show | display inheritance
protocols {
bgp {
group abcd {
##
141

## ’1’ was inherited from group ’one’
##
preference 1;
##
## ’10’ was inherited from group ’one’
##
hold-time 10;
##
## ’3’ was inherited from group ’one’
##
out-delay 3;
}
}
}
How to Improve Commit Time When Using Conguraon Groups
You use conguraon groups to apply conguraons across other hierarchies without re-entering
conguraon data. You can specify every conguraon detail in a conguraon groups. You can also use
wildcards in conguraon groups to congure ranges of data, without detailing each conguraon line.
Another way to use conguraon groups is to create an inheritance path that includes a long string of
conguraons to be applied.
When a conguraon that uses conguraon groups is commied, the commit process expands and
reads all the conguraon data of the group into memory to apply the conguraons as intended. The
commit performance can be negavely aected if many conguraon groups are being applied,
especially if the conguraon groups use wildcards extensively.
If your system uses many conguraon groups that use wildcards, you can congure the persist-groups-
inheritance statement at the [edit system commit] hierarchy level to improve commit me performance.
Using this opon enables the system to build the inheritance path for each conguraon group inside
the database rather than in the process memory. This change can improve commit me performance.
However, it can also increase the database size.
142

Example: Congure Sets of Statements with Conguraon Groups
When sets of statements exist in conguraon groups, all values are inherited. For example:
[edit]
user@host# show
groups {
basic {
snmp {
interface so-1/1/1.0;
}
}
}
apply-groups basic;
snmp {
interface so-0/0/0.0;
}
[edit]
user@host# show | display inheritance
snmp {
##
## ’so-1/1/1.0’ was inherited from group ’basic’
##
interface [ so-0/0/0.0 so-1/1/1.0 ];
}
For sets that are not displayed within brackets, all values are also inherited. For example:
[edit]
user@host# show
groups {
worldwide {
system {
name-server {
10.0.0.100;
10.0.0.200;
}
}
}
}
apply-groups worldwide;
143

system {
name-server {
10.0.0.1;
10.0.0.2;
}
}
[edit]
user@host# show | display inheritance
system {
name-server {
##
## ’10.0.0.100’ was inherited from group ’worldwide’
##
10.0.0.100;
##
## ’10.0.0.200’ was inherited from group ’worldwide’
##
10.0.0.200;
10.0.0.1;
10.0.0.2;
}
}
Example: Congure Interfaces Using Conguraon Groups
You can use conguraon groups to separate the common interface media parameters from the
interface-specic addressing informaon. The following example places conguraon data for ATM
interfaces into a group called atm-options.
[edit]
user@host# show
groups {
atm-options {
interfaces {
<at-*> {
atm-options {
vpi 0 maximum-vcs 1024;
}
unit <*> {
144

encapsulation atm-snap;
point-to-point;
family iso;
}
}
}
}
}
apply-groups atm-options;
interfaces {
at-0/0/0 {
unit 100 {
vci 0.100;
family inet {
address 10.0.0.100/30;
}
}
unit 200 {
vci 0.200;
family inet {
address 10.0.0.200/30;
}
}
}
}
[edit]
user@host# show | display inheritance
interfaces {
at-0/0/0 {
##
## "atm-options" was inherited from group "atm-options"
##
atm-options {
##
## "1024" was inherited from group "atm-options"
##
vpi 0 maximum-vcs 1024;
}
unit 100 {
##
## "atm-snap" was inherited from group "atm-options"
##
encapsulation atm-snap;
145

##
## "point-to-point" was inherited from group "atm-options"
##
point-to-point;
vci 0.100;
family inet {
address 10.0.0.100/30;
}
##
## "iso" was inherited from group "atm-options"
##
family iso;
}
unit 200 {
##
## "atm-snap" was inherited from group "atm-options"
##
encapsulation atm-snap;
##
## "point-to-point" was inherited from group "atm-options"
##
point-to-point;
vci 0.200;
family inet {
address 10.0.0.200/30;
}
##
## "iso" was inherited from group "atm-options"
##
family iso;
}
}
}
[edit]
user@host# show | display inheritance | except ##
interfaces {
at-0/0/0 {
atm-options {
vpi 0 maximum-vcs 1024;
}
unit 100 {
encapsulation atm-snap;
point-to-point;
146

vci 0.100;
family inet {
address 10.0.0.100/30;
}
family iso;
}
unit 200 {
encapsulation atm-snap;
point-to-point;
vci 0.200;
family inet {
address 10.0.0.200/30;
}
family iso;
}
}
}
SEE ALSO
Interface Naming Convenons Used in Operaonal Commands | 282
Example: Use Conguraon Groups to Congure a Consistent IP Address
for the Management Interface
On devices with mulple Roung Engines, each Roung Engine is congured with a separate IP address
for the management interface. To access the primary Roung Engine, you must know which Roung
Engine is acve and use the appropriate IP address.
Another opon for consistent access to the primary Roung Engine is to congure an addional IP
address. You then use this address for the management interface regardless of which Roung Engine is
acve. This addional IP address is acve only on the management interface for the primary Roung
Engine. During switchover, the address moves to the new primary Roung Engine.
This example congures address 10.17.40.131 for both Roung Engines and includes a master-only
statement. With this conguraon, the
10.17.40.131
address is acve only on the primary Roung Engine.
147

The address remains consistent regardless of which Roung Engine is acve. Address 10.17.40.132 is
assigned to fxp0 on re0, and 10.17.40.133 is assigned to fxp0 on re1.
[edit groups re0 interfaces fxp0]
unit 0 {
family inet {
address 10.17.40.131/25 {
master-only;
}
address 10.17.40.132/25;
}
}
[edit groups re1 interfaces fxp0]
unit 0 {
family inet {
address 10.17.40.131/25 {
master-only;
}
address 10.17.40.133/25;
}
}
This feature is available on all routers that include dual Roung Engines. On a roung matrix composed
of the TX Matrix router, this feature is applicable to the switch-card chassis (SCC) only. Likewise, on a
roung matrix composed of a TX Matrix Plus router, this feature is applicable to the switch-fabric
chassis (SFC) only.
NOTE:
• You must assign unique IP addresses for two interfaces that have duplicate addresses on
private and public interfaces. When graceful Roung Engine switchover (GRES) is enabled, the
CLI displays an appropriate commit error message if it nds idencal addresses. This error can
occur if you congure the same IP address for a management interface or internal interface
such as fxp0 and an external physical interface such as ge-0/0/1.
•
The em0 management Ethernet interface is used for the TX Matrix Plus router, T1600 routers
in a roung matrix, and PTX Series Packet Transport Routers. Junos OS automacally creates
the device's management Ethernet interface, em0.
148

Example: Use Conguraon Groups to Congure Peer Enes
This example creates a group some-isp that contains conguraon data relang to another ISP. It then
inserts apply-group statements at various points to allow those locaons in the conguraon hierarchy to
inherit this data.
[edit]
user@host# show
groups {
some-isp {
interfaces {
<xe-*> {
gigether-options {
flow-control;
}
}
}
protocols {
bgp {
group <*> {
neighbor <*> {
remove-private;
}
}
}
pim {
interface <*> {
version 1;
}
}
}
}
}
interfaces {
xe-0/0/0 {
apply-groups some-isp;
unit 0 {
family inet {
address 10.0.0.1/24;
}
}
149

}
}
protocols {
bgp {
group main {
neighbor 10.254.0.1 {
apply-groups some-isp;
}
}
}
pim {
interface xe-0/0/0.0 {
apply-groups some-isp;
}
}
}
[edit]
user@host# show | display inheritance
interfaces {
xe-0/0/0 {
##
## "gigether-options" was inherited from group "some-isp"
##
gigether-options {
##
## "flow-control" was inherited from group "some-isp"
##
flow-control;
}
unit 0 {
family inet {
address 10.0.0.1/24;
}
}
}
}
protocols {
bgp {
group main {
neighbor 10.254.0.1 {
##
## "remove-private" was inherited from group "some-isp"
##
150

remove-private;
}
}
}
pim {
interface xe-0/0/0.0 {
##
## "1" was inherited from group "some-isp"
##
version 1;
}
}
}
Example: Use Conguraon Groups to Establish Regional Conguraons
This example populates one group with conguraon data that is standard throughout the company,
while another group contains regional deviaons from this standard:
[edit]
user@host# show
groups {
standard {
interfaces {
<t3-*> {
t3-options {
compatibility-mode larscom subrate 10;
idle-cycle-flag ones;
}
}
}
}
northwest {
interfaces {
<t3-*> {
t3-options {
long-buildout;
compatibility-mode kentrox;
}
151

}
}
}
}
apply-groups standard;
interfaces {
t3-0/0/0 {
apply-groups northwest;
}
}
[edit]
user@host# show | display inheritance
interfaces {
t3-0/0/0 {
##
## "t3-options" was inherited from group "northwest"
##
t3-options {
##
## "long-buildout" was inherited from group "northwest"
##
long-buildout;
##
## "kentrox" was inherited from group "northwest"
##
compatibility-mode kentrox;
##
## "ones" was inherited from group "standard"
##
idle-cycle-flag ones;
}
}
}
Example: Congure Wildcard Conguraon Group Names
Wildcards are conguraon group names that use special characters to create a paern that you can
apply to mulple statements. Wildcards are useful for copying one set of conguraon opons to many
dierent conguraon groups. You must set up your wildcard name properly to ensure that the wildcard
conguraon opons get copied to the appropriate conguraon groups.
152

This example congures dierent values for the <*-major> and <*-minor> wildcard groups under the label-
switched-path statement. The asterisk (*) character represents a secon of the wildcard name that can
match any string of characters. For example, the conguraon opons under label-switched-path <*-major>
are passed on to label-switched-path metro-major and any other label-switched-path conguraon group
containing -major in its name.
[edit]
user@host# show
groups {
mpls-conf {
protocols {
mpls {
label-switched-path <*-major> {
retry-timer 5;
bandwidth 155m;
optimize-timer 60;
}
label-switched-path <*-minor> {
retry-timer 15;
bandwidth 64k;
optimize-timer 120;
}
}
}
}
}
apply-groups mpls-conf;
protocols {
mpls {
label-switched-path metro-major {
to 10.0.0.10;
}
label-switched-path remote-minor {
to 10.0.0.20;
}
}
}
[edit]
user@host# show | display inheritance
protocols {
mpls {
label-switched-path metro-major {
153

to 10.0.0.10;
##
## "5" was inherited from group "mpls-conf"
##
retry-timer 5;
## "155m" was inherited from group "mpls-conf"
##
bandwidth 155m;
##
## "60" was inherited from group "mpls-conf"
##
optimize-timer 60;
}
label-switched-path remote-minor {
to 10.0.0.20;
##
## "15" was inherited from group "mpls-conf"
##
retry-timer 15;
##
## "64k" was inherited from group "mpls-conf"
##
bandwidth 64k;
##
## "120" was inherited from group "mpls-conf"
##
optimize-timer 120;
}
}
}
Example: Reference the Preset Statement from the Defaults Group
The following example is a preset statement from the defaults group that is available for FTP in a
stateful rewall:
[edit]
groups {
junos-defaults {
154

applications {
application junos-ftp {# Use FTP default configuration
application-protocol ftp;
protocol tcp;
destination-port 21;
}
}
}
To reference a preset default statement from the defaults group, include the junos-
default-name
statement
at the applicable hierarchy level. For example, to reference the default statement for FTP in a stateful
rewall, include the junos-ftp statement at the [edit services stateful-firewall rule my-rule term my-term from
applications] hierarchy level:
[edit]
services {
stateful-firewall {
rule my-rule {
term my-term {
from {
applications junos-ftp; #Reference predefined statement, junos-ftp
}
}
}
}
}
Example: View Default Statements That Have Been Applied to the
Conguraon
To view the defaults that have been applied to the device conguraon, you issue the show | display
inheritance defaults command. This example displays the inherited defaults at the [edit system ports]
hierarchy level:
user@host# show system ports | display inheritance defaults
## ## 'console' was inherited from group 'junos-defaults'
155

## 'vt100' was inherited from group 'junos-defaults'
## console type vt100;
If you choose not to use exisng default statements, you can create your own conguraon groups
manually.
To view the complete conguraon informaon oming any comments marked with ##, use the no-
comments opon with the display inheritance command.
Set Up Roung Engine Conguraon Groups
In a device with two Roung Engines, both Roung Engines should share one conguraon. This setup
ensures that both Roung Engine conguraons are idencal. Within this conguraon, create two
Roung Engine groups, one for each Roung Engine. Within these groups, you specify the Roung
Engine–specic parameters.
For more informaon about the inial conguraon for redundant Roung Engine systems and the re0
group, see Junos OS High Availability User Guide.
To set up a Roung Engine conguraon group:
1. Create the conguraon group re0. The re0 group is a special group designator that RE0 uses, only in
a redundant roung plaorm.
[edit]
root# set groups re0
2. Navigate to the groups re0 level of the conguraon hierarchy.
[edit]
root# edit groups re0
3. Specify the device hostname.
[edit groups re0]
root# set system host-name
host-name
156

NOTE: The DNS server does not use the hostname that you specify in the device
conguraon to resolve to the correct IP address. The DNS server uses this hostname to
display the name of the Roung Engine in the CLI. For example, the hostname appears at
the command-line prompt when you are logged in to the CLI:
user-name
@
host-name
>
4. Congure the IP address and prex length for the device Ethernet interface.
• For all devices
except
the TX Matrix Plus router, T1600 or T4000 routers in a roung matrix,
and PTX Series Packet Transport Routers:
[edit]
root@# set interfaces fxp0 unit 0 family inet address
address
/
prefix-length
• For the TX Matrix Plus router, T1600 or T4000 routers in a roung matrix only, and PTX Series
Packet Transport Routers:
[edit]
root@# set interfaces em0 unit 0 family inet address
address
/
prefix-length
To use em0 as an out-of-band management Ethernet interface, you must congure its logical port,
em0.0, with a valid IP address.
5. Return to the top level of the hierarchy.
[edit groups re0]
root# top
6. Create the conguraon group re1.
[edit]
root# set groups re1
7.
Navigate to the groups re1 level of the conguraon hierarchy.
[edit]
root# edit groups re1
157

8. Specify the device hostname.
[edit groups re1]
root# set system host-name
host-name
9. Congure the IP address and prex length for the device Ethernet interface.
• For all devices
except
the TX Matrix Plus router, T1600 or T4000 routers in a roung matrix,
and PTX Series Packet Transport Routers:
[edit]
root@# set interfaces fxp0 unit 0 family inet address
address
/
prefix-length
• For the TX Matrix Plus router and T1600 or T4000 routers in a roung matrix only:
[edit]
root@# set interfaces em0 unit 0 family inet address
address
/
prefix-length
To use em0 as an out-of-band management Ethernet interface, you must congure its logical port,
em0.0, with a valid IP address.
10. Return to the top level of the hierarchy.
[edit groups re0]
root# top
11. Specify the group applicaon order.
[edit]
root# set apply-groups [ re0 re1 ]
How to Use Condions to Apply Conguraon Groups
You can use the when statement at the [edit groups
group-name
] hierarchy level to dene condions under
which to apply a conguraon group.
You can congure a group to apply based on the type of chassis, model, or Roung Engine,
virtual
chassis
member, cluster node, and start and oponal end me of day or date.
158

For example, you could use the when statement to create a generic conguraon group for each type of
node and then apply the conguraon based on certain node properes, such as chassis or model.
Example: Congure Condions for Applying Conguraon Groups
IN THIS SECTION
Requirements | 159
Overview | 159
Conguraon | 160
This example shows how to congure condions under which a specied conguraon group is to be
applied.
Requirements
No special conguraon beyond device inializaon is required before you congure this example.
Overview
You can congure your group conguraon data at the [edit groups
group-name
] hierarchy level. You can
then use the when statement to apply the group conguraon based on condions such as these: Type of
chassis, model, roung-engine, virtual chassis member, cluster node, and start and oponal end me of
day or date.
If you specify mulple condions in a single conguraon group, all condions must be met before the
conguraon group is applied.
You can specify the start me or the me duraon for the conguraon group to be applied. If only the
start me is specied, the conguraon group is applied at the specied me and it remains in eect
unl the me is changed. If the end me is specied, then on each day, the applied conguraon group
is started and stopped at the specied mes.
This example sets condions in a conguraon group, test1, such that this group is applied only when all
of the following condions are met: the router is a model MX240 router with chassis type LCC0, with a
Roung Engine operang as RE0, is member0 of the virtual chassis on node0, and the conguraon
group will only be in eect from 9:00 a.m. unl 5:00 p.m. each day.
159

Conguraon
IN THIS SECTION
Vericaon | 162
CLI Quick Conguraon
To quickly congure this example, copy the following commands, paste them into a text le, remove any
line breaks, change any details necessary to match your network conguraon, and then copy and paste
the commands into the CLI at the [edit] hierarchy level.
set groups test1 when model mx240
set groups test1 when chassis lcc0
set groups test1 when routing-engine re0
set groups test1 when member member0
set groups test1 when node node0
set groups test1 when time 9 to 5
Procedure
Step-by-Step Procedure
To congure condions for conguraon group test1:
1. Set the condion that idenes the model MX240 router.
[edit groups test1 when]
user@host# set model mx240
2. Set the condion that idenes the chassis type as LCC0.
[edit groups test1 when]
user@host# set chassis lcc0
160

3. Set the condion that idenes the Roung Engine operang as RE0.
[edit groups test1 when]
user@host# set routing-engine re0
4. Set the condion that idenes the virtual chassis member0.
[edit groups test1 when]
user@host# set member member0
5. Set the condion that idenes the cluster node0.
[edit groups test1 when]
user@host# set node node0
6. Set the condion that applies the group only between the hours of 9:00 a.m. and 5:00 p.m. daily.
[edit groups test1 when]
user@host# set time 9 to 5
NOTE: The syntax for specifying the me is: time
<start-time>
[to
<end-time>
] using the me
format yyyy-mm-dd.hh:mm, hh:mm, or hh.
7. Commit the conguraon.
user@host# commit
Results
In conguraon mode, conrm your conguraon by entering the show groups test1 command. If the
output does not display the intended conguraon, repeat the instrucons in this example to correct
the conguraon.
user@host# show groups test1
when {
161

time 9 to 5;
chassis lcc0;
model mx240;
routing-engine re0;
member member0;
node node0;
}
Vericaon
IN THIS SECTION
Check Group Inheritance with Condional Data | 162
Check Group Inheritance with Condional Data
Purpose
Verify that condional data from a conguraon group is inherited when applied.
Acon
Issue the show | display inheritance operaonal command with the when data to display the condional
inheritance. Using this example, you can issue one of these commands to determine that the condional
data was inherited:
user@host> show | display inheritance when model mx240
user@host> show | display inheritance when chassis lcc0
user@host> show | display inheritance when routing-engine re0
user@host> show | display inheritance when member member0
user@host> show | display inheritance when node node0
user@host> show | display inheritance when time 9 to 5
162

View the Conguraon
IN THIS SECTION
Display the Current Conguraon | 163
Example: Display the Current Conguraon | 164
Display Addional Informaon About the Conguraon | 166
Display set Commands from the Conguraon | 169
The show conguraon mode command displays the current conguraon for a device running Junos OS.
Display the Current Conguraon
To display the current conguraon for a Juniper Networks device, use the show command in
conguraon mode. This command displays the conguraon at the current hierarchy level or at the
specied level.
user@host# show
<statement-path>
The conguraon statements appear in a xed order, interfaces appear alphabecally by type, and then
in numerical order by slot number, PIC number, and port number. Note that when you congure the
device, you can enter statements in any order.
You also can use the CLI operaonal mode show configuration command to display the last commied
conguraon, which is the conguraon currently running on the router:
user@host> show configuration
163

When you show a conguraon, a mestamp at the top of the conguraon indicates when the
conguraon was last changed:
## Last commit: 2018-07-18 11:21:58 PDT by echen
version 8.3
If you have omied a required statement at a specic hierarchy level, when you issue the show command
in conguraon mode, a message indicates which statement is missing. If a mandatory statement is
missing, the CLI connues to display this message each me you issue a show command.
For example:
[edit]
user@host# show
protocols {
pim {
interface so-0/0/0 {
priority 4;
version 2;
# Warning: missing mandatory statement(s): 'mode'
}
}
}
Unsupported statements included in the CLI conguraon are displayed with the “unsupported” text in
the conguraon. For example, if a statement is congured on an unsupported plaorm, the CLI displays
a message that the statement is ignored in the conguraon because it is congured on an unsupported
plaorm. When you issue the show command with the | display xml opon, you can see the
unsupported="unsupported” aribute for conguraon that is unsupported.
The “unsupported” aribute included in text conguraon or XML conguraon is provided to scripts
when the unsupported="unsupported" aribute is included in the <get-configuration> RPC call.
Example: Display the Current Conguraon
The following example shows how you can display the current device conguraon.
164

Set and commit a conguraon:
[edit]
user@host# set protocols ospf area 0.0.0.0 interface xe-0/0/0 hello-interval 5
[edit]
user@host# commit
commit complete
[edit]
user@host# quit
exiting configuration mode
Display the current conguraon:
[edit]
user@host# show
protocols {
ospf {
area 0.0.0.0 {
interface xe-0/0/0 {
hello-interval 5;
}
}
}
}
Display the conguraon at a parcular hierarchy:
[edit]
user@host# show protocols ospf area 0.0.0.0
interface xe-0/0/0 {
hello-interval 5;
}
Move down a level and display the conguraon at that level:
[edit]
user@host# edit protocols ospf area 0.0.0.0
[edit protocols ospf area 0.0.0.0]
user@host# show
interface xe-0/0/0 {
165

hello-interval 5;
}
Display the last commied conguraon:
user@host> show configuration
## Last commit: 2018-08-10 11:21:58 PDT by user
version 8.3
protocols {
ospf {
area 0.0.0.0 {
interface xe-0/0/0 {
hello-interval 5;
}
}
}
}
Display Addional Informaon About the Conguraon
In conguraon mode only, to display addional informaon about the device conguraon, use the
display detail command aer the pipe ( | ) in conjuncon with a show command. The addional
informaon includes the help string that explains each conguraon statement and the permission bits
required to add and modify the conguraon statement.
user@host# show <
hierarchy-level
> | display detail
For example:
[edit]
user@host# show | display detail
##
## version: Software version information
## require: system
##
version 21.3-202107190949.0;
system {
##
166

## host-name: Host name for this router
## match: ^[[:alnum:]._-]+$
## require: system
##
}
host-name router-name;
##
## domain-name: Domain name for this router
## match: ^[[:alnum:]._-]+$
## require: system
##
domain-name isp.net;
##
## backup-router: Address of router to use while booting
##
backup-router 192.168.100.1;
root-authentication {
##
## encrypted-password: Encrypted password string
##
encrypted-password "$ABC123"; # SECRET-DATA
}
##
## name-server: DNS name servers
## require: system
##
name-server {
##
## name-server: DNS name server address
##
208.197.1.0;
}
login {
##
## class: User name (login)
## match: ^[[:alnum:]_-]+$
##
class super-user {
##
## permissions: Set of permitted operation categories
##
permissions all;
}
167

...
##
## services: System services
## require: system
##
services {
## services: Service name
##
ftp;
##
## services: Service name
##
telnet;
##
}
syslog {
##
## file-name: File to record logging data
##
file messages {
##
## Facility type
## Level name
##
any notice;
##
## Facility type
## Level name
##
authorization info;
}
}
}
chassis {
alarm {
sonet {
##
## lol: Loss of light
## alias: loss-of-light
##
lol red;
}
}
168

}
interfaces {
##
## Interface name
##
xe-2/1/1 {
atm-options {
##
## vpi: Virtual path index
## range: 0 .. 255
## maximum-vcs: Maximum number of virtual circuits on this VP
##
vpi 0 maximum-vcs 512;
}
##
## unit: Logical unit number
## range: 0 .. 16384
##
unit 0 {
##
## vci: ATM point-to-point virtual circuit identifier ([vpi.]vci)
}
##
vci 0.128;
}
}
...
Display set Commands from the Conguraon
IN THIS SECTION
Example: Display set Commands from the Conguraon | 170
Example: Display set Commands with the match Opon | 172
169

In conguraon mode, you can display the conguraon as a series of conguraon mode commands
required to re-create the conguraon. This is useful if you are not familiar with how to use
conguraon mode commands or if you want to cut, paste, and edit the displayed conguraon.
To display the conguraon as a series of conguraon mode commands, which are required to re-
create the conguraon from the top level of the hierarchy as set commands, issue the show conguraon
mode command with the display set opon:
user@host# show | display set <explicit>
When you issue the show configuration command with the | display set pipe opon to view the
conguraon as set commands, those porons of the conguraon that you do not have permissions to
view are substuted with the text ACCESS-DENIED.
You can use the <explicit> opon with the | display set command, to explicitly display all the
conguraon statements that the system internally creates, as a series of set commands, when you
congure certain statements from the top level of the hierarchy.
For example, assume you issue the set interfaces ge-0/0/0.0 family inet conguraon mode command.
You then show the resulng conguraon with the show interfaces ge-0/0/0 | display set command.
The output displays the same set command you entered. If you include the explicit argument, the output
also shows the conguraon statements needed to create the hierarchy where the family inet statement
is specied. Specically for this example, the output therefore includes the set interfaces ge-0/0/0 unit
0 statement in addion to the set interfaces ge-0/0/0.0 family inet statement.
Example: Display set Commands from the Conguraon
Display the set commands from the conguraon at the [edit interfaces] hierarchy level:
[edit interfaces xe-0/0/0]
user@host# show
unit 0 {
family inet {
address 192.107.1.230/24;
}
family iso;
family mpls;
}
inactive: unit 1 {
family inet {
address 10.0.0.1/8;
}
170

}
[edit interfaces ge-0/0/0]
user@host# show | display set
set interfaces ge-0/0/0 unit 0 family inet address 192.107.1.230/24
set interfaces xe-0/0/0 unit 1 family inet address 10.0.0.1/8
deactivate interfaces xe-0/0/0 unit 1
[edit interfaces ge-0/0/0]
user@host# show | display set | explicit
set interfaces ge-0/0/0 unit 0 family inet address 192.107.1.230/24
set interfaces xe-0/0/0 unit 0 family iso
set interfaces xe-0/0/0 unit 0 family mpls
set interfaces ge-0/0/0 unit 0 family inet
set interfaces ge-0/0/0 unit 0
set interfaces xe-0/0/0 unit 1 family inet address 10.0.0.1/8
deactivate interfaces xe-0/0/0 unit 1
To display the conguraon as a series of conguraon mode commands required to re-create the
conguraon from the current hierarchy level, issue the show conguraon mode command with the show
| display set relative opon. You can use the <explicit> opon to explicitly display, as a series of
commands, all the conguraons that the system internally creates when you congure certain
statements from the current hierarchy level.
[edit interfaces fe-0/0/0]
user@host# show
unit 0 {
family inet {
address 192.107.1.230/24;
}
family iso;
family mpls;
}
inactive: unit 1 {
family inet {
address 10.0.0.1/8;
}
}
[edit interfaces xe-0/0/0]
user@host# show | display set relative
set unit 0 family inet address 192.107.1.230/24
171

set unit 0 family iso
set unit 0 family mpls
set unit 1 family inet address 10.0.0.1/8
deactivate unit 1
user@host# show | display set relative | explicit
set unit 0 family inet address 192.168.1.230/24
set unit 0 family inet
set unit 0 family iso
set unit 0 family mpls
set unit 0
set unit 1 family inet address 10.0.0.1/8
set unit 1 family inet
deactivate unit 1
Example: Display set Commands with the match Opon
To display the conguraon as set commands and search for text matching a regular expression by
ltering output, specify the match opon aer the pipe ( | ):
user@host# show | display set | match
regular-expression
Display IP addresses associated with an interface:
xe-2/3/0 {
unit 0 {
family inet {
address 192.107.9.106/30;
}
}
}
so-5/1/0 {
unit 0 {
family inet {
address 192.107.9.15/32 {
destination 192.107.9.192;
}
}
}
}
172

lo0 {
unit 0 {
family inet {
address 127.0.0.1/32;
}
}
}
user@host# show interfaces | display set | match address
set interfaces xe-2/3/0 unit 0 family inet address 192.168.9.106/30
set interfaces so-5/1/0 unit 0 family inet address 192.168.9.15/32 destination 192.168.9.192
set interfaces lo0 unit 0 family inet address 127.0.0.1/32
Verify the Device Conguraon
To verify that the syntax of a Juniper Networks device conguraon is correct, use the conguraon
mode commit check command:
[edit]
user@host# commit check
configuration check succeeds
[edit]
user@host#
If the commit check command nds an error, a message indicates the locaon of the error.
RELATED DOCUMENTATION
Commit a Device Conguraon | 176
173

Commit the Conguraon
IN THIS SECTION
The Commit Model for Conguraons | 174
Commit a Device Conguraon | 176
Commit Operaon When Mulple Users Congure the Soware | 177
Commit Preparaon and Acvaon Overview | 178
Commit Device Conguraons in Two Steps: Preparaon and Acvaon | 180
Acvate a Device Conguraon with Conrmaon | 182
Schedule a Commit Operaon | 183
Monitor the Commit Process | 184
Add a Comment to Describe the Commied Conguraon | 186
Batch Commits Overview | 187
Example: Congure Batch Commit Server Properes | 188
Back Up the Commied Conguraon on the Alternate Boot Drive | 199
The commit conguraon mode command enables you to save the device conguraon changes to the
conguraon database and to acvate the conguraon on the device.
The Commit Model for Conguraons
The device conguraon is saved using a commit model—a candidate conguraon is modied as
desired and then commied to the system. When a conguraon is commied, the device checks the
conguraon for syntax errors, and if no errors are found, the conguraon is saved as juniper.conf.gz
and acvated. The formerly acve conguraon le is saved as the rst rollback conguraon le
(juniper.conf.1.gz), and any other rollback conguraon les are incremented by 1. For example,
juniper.conf.1.gz is incremented to juniper.conf.2.gz, making it the second rollback conguraon le.
The device can have a maximum of 49 rollback conguraons (numbered 1 through 49) saved on the
system.
174

On the device, the current conguraon le and the rst three rollback les (juniper.conf.gz.1,
juniper.conf.gz.2, juniper.conf.gz.3) are located in the /cong directory. (The remaining rollback les, 4
through 49, are located in /var/db/cong.)
If the recovery conguraon le rescue.conf.gz exists, this le is also located in the /cong directory.
The factory default les are located in the /etc/cong directory.
There are two mechanisms used to propagate the conguraons between Roung Engines within a
device:
• Synchronizaon: Propagates a conguraon from one Roung Engine to a second Roung Engine
within the same device chassis.
To synchronize conguraons, use the commit synchronize CLI command. If one of the Roung Engines
is locked, the synchronizaon fails. If synchronizaon fails because of a locked conguraon le, you
can use the commit synchronize force command. This command overrides the lock and synchronizes the
conguraon les.
• Distribuon: Propagates a conguraon across the roung plane on a mulchassis device.
Distribuon occurs automacally. There is no user command available to control the distribuon
process. If a conguraon is locked during a distribuon of a conguraon, the locked conguraon
does not receive the distributed conguraon le, so the synchronizaon fails. You need to clear the
lock before the conguraon and resynchronize the roung planes.
NOTE: When you use the commit synchronize force CLI command on a mulchassis plaorm, the
forced synchronizaon of the conguraon les does not aect the distribuon of the
conguraon le across the roung plane. If a conguraon le is locked on a device remote
from the device where the command was issued, the synchronizaon fails on the remote
device. You need to clear the lock and reissue the synchronization command.
SEE ALSO
Conguring Junos OS for the First Time on a Device with a Single Roung Engine
175

Commit a Device Conguraon
To save device conguraon changes to the conguraon database and to acvate the conguraon on
the device, use the commit conguraon mode command. You can issue the commit command from any
hierarchy level:
[edit]
user@host# commit
commit complete
[edit]
user@host#
When you enter the commit command, the conguraon is rst checked for syntax errors (commit check).
Then, if the syntax is correct, the conguraon is acvated and becomes the current, operaonal device
conguraon.
NOTE: We do not recommend performing a commit operaon on the backup Roung Engine
when graceful Roung Engine switchover is enabled on the router.
A conguraon commit can fail for any of the following reasons:
• The conguraon includes incorrect syntax, which causes the commit check to fail.
• The candidate conguraon that you are trying to commit is larger than 700 MB.
• The conguraon is locked by a user who entered the configure exclusive command.
If the conguraon contains syntax errors, a message indicates the locaon of the error, and the
conguraon is not acvated. The error message has the following format:
[edit
edit-path
]
‘
offending-statement
;’
error-message
For example:
[edit firewall filter login-allowed term allowed from]
‘icmp-type [ echo-request echo-reply ];’
keyword ‘echo-reply’ unrecognized
176

You must correct the error before recomming the conguraon. To return quickly to the hierarchy
level where the error is located, copy the path from the rst line of the error and paste it at the
conguraon mode prompt at the [edit] hierarchy level.
The uncommied, candidate conguraon le is /var/rundb/juniper.db. It is limited to 700 MB. If the
commit fails with a message configuration database size limit exceeded, view the le size from conguraon
mode by entering the command run file list /var/rundb detail. You can simplify the conguraon and
reduce the le size by creang conguraon groups with wildcards or dening less specic match
policies in your rewall lters.
NOTE: CLI commit-me warnings displayed for conguraon changes at the [edit interfaces]
hierarchy level are removed and are logged as system log messages.
This is also applicable to VRRP conguraon at the following hierarchy levels:
• [edit interfaces
interface-name
unit
logical-unit-number
family (
inet
|
inet6
) address
address
]
• [edit logical-systems
logical-system-name
interfaces
interface-name
unit
logical-unit-number
family
(inet | inet6) address
address
]
When you commit a conguraon, you commit the enre conguraon in its current form.
NOTE:
• We do not recommend performing a commit operaon on the backup Roung Engine when
graceful Roung Engine switchover
is enabled on the device.
• If you congure the same IP address for a management interface or internal interface such as
fxp0 and an external physical interface such as ge-0/0/1, when graceful Roung Engine
switchover (GRES) is enabled, the CLI displays an appropriate commit error message that
idencal addresses have been found on the private and public interfaces. In such cases, you
must assign unique IP addresses for the two interfaces that have duplicate addresses.
Commit Operaon When Mulple Users Congure the Soware
Up to 32 users can be in conguraon mode simultaneously making changes to the conguraon. All
changes made by all users are visible to everyone eding the conguraon—the changes become visible
as soon as the user presses the Enter key at the end of a command that changes the conguraon, such
as set, edit, or delete.
177

When any of the users eding the conguraon issues a commit command, the CLI checks and acvates
all changes by all users.
If you enter conguraon mode with the configure private command, each user has a private candidate
conguraon to edit somewhat independently of other users. When you commit the conguraon, the
CLI commits only your own changes. To synchronize your copy of the conguraon aer other users
have commied changes, you can run the update command in conguraon mode. A commit operaon
also updates all the private candidate conguraons. For example, suppose user X and user Y are both in
configure private mode, and user X commits a conguraon change. When user Y performs a subsequent
commit operaon and then views the new conguraon, the new conguraon seen by user Y includes
the changes made by user X.
If you enter conguraon mode with the configure exclusive command, you lock the candidate
conguraon for as long as you remain in conguraon mode. This allows you to make changes without
interference from other users. Other users can enter and exit conguraon mode, but they cannot
commit the conguraon. This is true even if the other users entered conguraon mode before you
enter the configure exclusive command. For example, suppose user X is already in the configure private or
configure mode. Then suppose user Y enters the configure exclusive mode. User X cannot commit any
changes to the conguraon, even if user X entered those changes before user Y logged in. If user Y
exits configure exclusive mode, user X can then commit the changes made in configure private or configure
mode.
Commit Preparaon and Acvaon Overview
You can complete the commit process in two steps. The two-step commit feature enables you to
congure several devices and simultaneously acvate the conguraons. Two-step commit provides a
denive me window for the commit to be eecve on the system. You can enter commit mode aer
the commit is prepared, but you will receive a message that the commit is pending acvaon.
In the rst step, the preparaon stage, the commit is validated and a new database with the necessary
les is generated. If the conguraon contains any syntax errors, an appropriate error message is
displayed, and the conguraon is not prepared. In the event of failure during the preparaon stage, the
error message commit check-out faileddisplays.
In the second step, the acvaon stage, the previously prepared conguraon is acvated. Next, if you
need to clear the prepared conguraon, you can do so by using clear system commit prepared command. A
log message is generated upon successful clearing of the pending commit.
NOTE: You cannot perform commit operaons in between preparaon and acvaon stages.
178

The two-step commit process is superior to the single-step process for me-crical commits. In the
single-step process, the preparaon me can vary depending on the exisng conguraon on the
device. In the two-step process, the complex preparaon work is more eciently handled.
Conguraon commands are provided that allow you to prepare the conguraon cache and acvate
the conguraon. You can prepare the devices with new conguraons and acvate them at the exact
mes you want.
The commit prepare command validates the conguraons, and the commit activate command acvates the
conguraons. The commands have the following conguraon opons:
• and-quit
• no-synchronize
• peers-synchronize
• synchronize
The commit prepare and commit activate commands are available for private, exclusive and shared commits
only. The commands are not applicable for dynamic and ephemeral modes. This feature is applicable for
mulchassis devices, but it is not applicable for batch commits.
To support this funconality using Network Conguraon Protocol (NETCONF), the following new
remote procedure calls (RPCs) are provided:
• <commit-configuration>< prepare/></commit-configuration>
• <commit-configuration><activate/></commit-configuration>
• <clear-system-commit><prepared/></clear-system-commit>
NOTE:
• In an MX Series Virtual Chassis setup the following applies: When commit prepare is issued on
one Roung Engine followed by switchover, the Roung Engine where the switchover
command is issued reboots. Therefore, the prepared cache is cleared in that Roung Engine.
• In an MX Series Virtual Chassis setup, it is advisable to execute clear system commit prepared
command only on VC primary.
179

Commit Device Conguraons in Two Steps: Preparaon and Acvaon
You can complete the commit process in two steps. This enables you to congure several devices, and
the conguraons can be acvated simultaneously. In the rst step, known as the preparaon stage, the
commit is validated and a new database along with necessary les is generated. If the conguraon
contains any syntax errors, an appropriate error message is displayed, and the conguraon is not
prepared. In the second step, referred to as the acvaon stage, the previously prepared conguraon is
acvated and becomes the current, operaonal device conguraon.
To prepare the conguraon:
1. At the [edit] hierarchy level in conguraon mode, make the necessary changes to the conguraon.
For example, to congure the scripts of the system, issue the following command:
[edit]
user@host# set system scripts
language
For example:
[edit]
user@host#set system scripts language python
2. Issue the commit prepare command.
[edit]
user@host# commit prepare
The message commit prepare successful is displayed.
If the preparaon stage fails, the error message commit check-out failed is displayed.
[edit]
user@host# set interfaces ge-0/0/0 unit 0 family inet address 1.1.1.2/2
[edit]
user@host# set interfaces ge-0/0/1 unit 0 family inet address 1.1.1.2/24
[edit]
user@host# commit prepare
[edit interfaces ge-2/0/0 unit 0 family inet]
'address 1.1.1.2/24'
180

Cannot have the same local address on the same unit of an interface
error: configuration check-out failed
3. To verify the output of the show system commit command aer commit prepare is issued, use the following
command:
user@host> show system commit
commit prepared by user via cli is pending activation
To acvate the prepared conguraon:
1. Use the commit activate command
[edit]
user@host# commit activate
The message commit complete is displayed.
2. To verify the acvated system conguraon, use the following command:
user@host> show configuration system scripts
language python;
To verify the output of the show system commit and show system commit revision detail commands aer commit
activate is issued, issue the following commands.
user@host> show system commit
0 2018-07-12 22:54:46 PDT by user via cli commit activate
user@host> show system commit revision detail
Revision: re0-1499925285-2214
User : user
Client : cli
Time : 2018-07-12 22:54:46 PDT
Comment : commit activate
181

Acvate a Device Conguraon with Conrmaon
When you commit the current candidate conguraon, you can require an explicit conrmaon for the
commit to become permanent. This is useful if you want to verify that a conguraon change works
correctly and does not prevent access to the device. If the change prevents access or causes other
errors, the device automacally returns to the previous conguraon and restores access aer the
rollback conrmaon meout passes. This feature is called automac rollback.
To commit the current candidate conguraon but require an explicit conrmaon for the commit to
become permanent, use the commit confirmed conguraon mode command:
[edit]
user@host# commit confirmed
commit confirmed will be automatically rolled back in 10 minutes unless confirmed
commit complete
#commit confirmed will be rolled back in 10 minutes
[edit]
user@host#
Once you have veried that the change works correctly, you can keep the new conguraon acve by
entering a commit or commit check command within 10 minutes of the commit confirmed command. For
example:
[edit]
user@host# commit check
configuration check succeeds
If the commit is not conrmed within a certain me (10 minutes by default), the operang system
automacally rolls back to the previous conguraon and a broadcast message is sent to all logged-in
users.
To show when a rollback is scheduled aer a commit confirmed command, enter the show system commit
command. For example:
user@host>show system commit
0 2018-01-05 15:00:37 PST by root via cli commit confirmed, rollback in 3mins
Like the commit command, the commit confirmed command veries the conguraon syntax and reports any
errors. If there are no errors, the conguraon is acvated temporarily (10 minutes by default) and
begins running on the device.
182

Figure 4: Conrm a Conguraon
To change the amount of me before you must conrm the new conguraon, specify the number of
minutes when you issue the command:
[edit]
user@host# commit confirmed
minutes
commit complete
[edit]
user@host#
You can also use the commit confirmed command in the [edit private] conguraon mode.
Schedule a Commit Operaon
You can schedule when you want your candidate conguraon to become acve. To save device
conguraon changes and acvate the conguraon on the device at a future me or upon reboot, use
the commit at conguraon mode command, specifying reboot or a future me at the [edit] hierarchy level:
[edit]
user@host # commit at
string
string
is reboot or the future me to acvate the conguraon changes. You can specify me in two
formats:
•
A me value in the form
hh
:
mm
[:
ss
] (hours, minutes, and oponally seconds)—Commit the
conguraon at the specied me, which must be in the future but before 11:59:59 PM on the day
the commit at conguraon mode command is issued. Use 24-hour me for the
hh
value; for example,
183

04:30:00 is 4:30:00 AM, and 20:00 is 8:00 PM. The me is interpreted with respect to the clock and
me zone sengs on the router.
• A date and me value in the form
yyyy-mm-dd hh
:
mm
[:
ss
] (year, month, date, hours, minutes, and,
oponally, seconds)—Commit the conguraon at the specied day and me, which must be aer
the commit at command is issued. Use 24-hour me for the
hh
value. For example, 2018-08-21 12:30:00 is
12:30 PM on August 21, 2018. The me is interpreted with respect to the clock and me zone
sengs on the router.
Enclose the
string
value in quotaon marks (" "). For example, commit at "18:00:00". For date and me,
include both values in the same set of quotaon marks. For example, commit at "2018-03-10 14:00:00".
A commit check is performed immediately when you issue the commit at conguraon mode command. If
the result of the check is successful, then the current user is logged out of conguraon mode, and the
conguraon data is le in a read-only state. No other commit can be performed unl the scheduled
commit is completed.
NOTE: If the device soware fails before the conguraon changes become acve, all
conguraon changes are lost.
You cannot enter the commit at conguraon command aer you issue the request system reboot
command.
You cannot enter the request system reboot command once you schedule a commit operaon for a
specic me in the future.
You cannot commit a conguraon when a scheduled commit is pending. For informaon about
how to cancel a scheduled conguraon by means of the clear command, see the CLI Explorer.
NOTE: We do not recommend performing a commit operaon on the backup Roung Engine
when graceful Roung Engine switchover is enabled on the device.
Monitor the Commit Process
To monitor the device conguraon commit process, use the display detail command aer the pipe with
the commit command:
user@host# commit | display detail
184

For example:
[edit]
user@host# commit | display detail
2018-09-22 15:39:39 PDT: exporting juniper.conf
2018-09-22 15:39:39 PDT: setup foreign files
2018-09-22 15:39:39 PDT: propagating foreign files
2018-09-22 15:39:39 PDT: complete foreign files
2018-09-22 15:39:40 PDT: copying configuration to juniper.data+
2018-09-22 15:39:40 PDT: dropping unchanged foreign files
2018-09-22 15:39:40 PDT: daemons checking new configuration
2018-09-22 15:39:41 PDT: commit wrapup...
2018-09-22 15:39:42 PDT: activating '/var/etc/ntp.conf'
2018-09-22 15:39:42 PDT: activating '/var/etc/kmd.conf'
2018-09-22 15:39:42 PDT: activating '/var/db/juniper.data'
2018-09-22 15:39:42 PDT: notifying daemons of new configuration
2018-09-22 15:39:42 PDT: signaling 'Firewall daemon', pid 24567, signal 1,
status 0
2018-09-22 15:39:42 PDT: signaling 'Interface daemon', pid 24568, signal 1,
status 0
2018-09-22 15:39:43 PDT: signaling 'Routing protocol daemon', pid 25679,
signal 1, status 0
2018-09-22 15:39:43 PDT: signaling 'MIB2 daemon', pid 24549, signal 1,
status 0
2018-09-22 15:39:43 PDT: signaling 'NTP daemon', pid 37863, signal 1, status 0
2018-09-22 15:39:43 PDT: signaling 'Sonet APS daemon', pid 24551, signal 1,
status 0
2018-09-22 15:39:43 PDT: signaling 'VRRP daemon', pid 24552, signal 1,
status 0
2018-09-22 15:39:43 PDT: signaling 'PFE daemon', pid 2316, signal 1, status 0
2018-09-22 15:39:43 PDT: signaling 'Traffic sampling control daemon', pid 24553
signal 1, status 0
2018-09-22 15:39:43 PDT: signaling 'IPsec Key Management daemon', pid
24556, signal 1, status 0
2018-09-22 15:39:43 PDT: signaling 'Forwarding UDP daemon', pid 2320,
signal 1, status 0
commit complete
185

Add a Comment to Describe the Commied Conguraon
You can include a comment that describes changes to the commied conguraon. To do so, include the
commit comment statement. The comment can be as long as 512 bytes and you must type it on a single line.
[edit]
user@host# commit comment
comment-string
comment-string
is the text of the comment.
NOTE: You cannot include a comment with the commit check command.
To add a comment to the commit command, include the comment statement aer the commit command:
[edit]
user@host# commit comment "add user joe"
commit complete
[edit]
user@host#
To add a comment to the commit confirmed command, include the comment statement aer the commit
confirmed command:
[edit]
user@host# commit confirmed comment "add customer to port 27"
commit confirmed will be automatically rolled back in 10 minutes unless confirmed
commit complete
[edit]
user@host#
To view these commit comments, issue the show system commit operaonal mode command.
NOTE: You can also use the commit confirmed command in the [edit private] conguraon mode.
Starng in Junos OS Release 24.2R1, Junos OS enforces you to issue a comment for each commit
request. This helps to track changes made by mulple users or administrators at the me of commit.
186

NOTE: The commit command does not execute without the comment argument.
To enforce the user to add a comment for each commit request, congure force-commit-log opon at the
[edit system commit] hierarchy level.
Batch Commits Overview
IN THIS SECTION
Aggregaon and Error Handling | 187
Batch commit aggregates or merges mulple conguraon edits from dierent CLI sessions or users and
adds them to a batch commit queue. A batch commit server running on the device takes one or more
jobs from the batch commit queue, applies the conguraon changes to the shared conguraon
database, and then commits the conguraon changes in a single commit operaon.
Batches are priorized by the commit server based on priority of the batch specied by the user or the
me when the batch job is added. When one batch commit is complete, the next set of conguraon
changes are aggregated and loaded into the batch queue for the next session of the batch commit
operaon. Batches are created unl there are no commit entries le in the queue directory.
When compared to the regular commit operaon where all commits are independently commied
sequenally, batch commits save me and system resources by comming mulple small conguraon
edits in a single commit operaon.
Batch commits are performed from the [edit batch] conguraon mode. The commit server properes
can be congured at the [edit system commit server] hierarchy level.
Aggregaon and Error Handling
When there is a load-me error in one of the aggregated jobs, the commit job that encounters the error
is discarded and the remaining jobs are aggregated and commied.
For example, if there are ve commit jobs (commit-1, commit-2, commit-3, commit-4, and commit-5) being
aggregated, and commit-3 encounters an error while loading, commit-3 is discarded and commit-1, commit-2,
commit-4, and commit-5 are aggregated and commied.
187

If there is an error during the commit operaon when two or more jobs are aggregated and commied,
the aggregaon is discarded and each of those jobs is commied individually like a regular commit
operaon.
For example, if there are ve commit jobs (commit-1, commit-2, commit-3, commit-4, and commit-5) that are
aggregated and if there is a commit error caused because of commit-3, the aggregaon is discarded,
commit-1, commit-2, commit-3, commit-4, and commit-5 are commied individually, and the CLI reports a commit
error for commit-3.
Example: Congure Batch Commit Server Properes
IN THIS SECTION
Requirements | 188
Overview | 188
Conguraon | 189
Vericaon | 192
This example shows how to congure batch commit server properes to manage batch commit
operaons.
Requirements
This example uses the following hardware and soware components:
• MX Series 5G Universal Roung Plaorm
Overview
You can control how the batch commit queue is handled by the commit server by conguring the server
properes at the [edit system commit server] hierarchy level. This enables you to control how many commit
jobs are aggregated or merged into a single batch commit, the maximum number of jobs that can be
added to the queue, days to keep batch commit error logs, interval between two batch commits, and
tracing operaons for batch commit operaons.
188

Conguraon
IN THIS SECTION
CLI Quick Conguraon | 189
Conguring the Commit Server Properes | 189
Comming the Conguraon from Batch Conguraon Mode | 191
CLI Quick Conguraon
To quickly congure this secon of the example, copy the following commands, paste them into a text
le, remove any line breaks, change any details necessary to match your network conguraon, and
then copy and paste the commands into the CLI at the [edit] hierarchy level. You can congure the
commit server properes from either the regular [edit] mode or the [edit batch] mode.
Device R0
set system commit server maximum-aggregate-pool 4
set system commit server maximum-entries 500
set system commit server commit-interval 5
set system commit server days-to-keep-error-logs 30
set system commit server traceoptions file commitd_nov
set system commit server traceoptions flag all
Conguring the Commit Server Properes
Step-by-Step Procedure
1. (Oponal) Congure the number of commit transacons to aggregate or merge in a single commit
operaon.
The default value for maximum-aggregate-pool is 5.
NOTE: Seng maximum-aggregate-pool to 1 commits each of the jobs individually.
189

In this example, the number of commit transacons is set to 4 indicang that four dierent commit
jobs are aggregated into a single commit before the commit operaon is iniated.
[edit system commit server]
user@R0# set maximum-aggregate-pool 4
2. (Oponal) Congure the maximum number of jobs allowed in a batch.
This limits the number of commits jobs that are added to the queue.
[edit system commit server]
user@R0# set maximum-entries 500
NOTE: If you set maximum-entries to 1, the commit server cannot add more than one job to the
queue, and the CLI displays an appropriate message when you try to commit more than one
job.
3. (Oponal) Congure the me (in seconds) to wait before starng the next batch commit operaon.
[edit system commit server]
user@R0# set commit-interval 5
4. (Oponal) Congure the number of days to keep error logs.
The default value is 30 days.
[edit system commit server]
user@R0# set days-to-keep-error-logs 30
5. (Oponal) Congure tracing operaons to log batch commit events.
In this example, the lename for logging batch commit events is commitd_nov, and all traceopon ags
are set.
[edit system commit server]
user@R0# set traceoptions commitd_nov
user@R0# set traceoptions flag all
190

Results
From conguraon mode, conrm your conguraon by entering the show system commit server command.
If the output does not display the intended conguraon, repeat the instrucons in this example to
correct the conguraon.
user@R0# show system commit server
maximum-aggregate-pool 4;
maximum-entries 500;
commit-interval 5;
days-to-keep-error-logs 30;
traceoptions {
file commitd_nov;
flag all;
}
Comming the Conguraon from Batch Conguraon Mode
Step-by-Step Procedure
To commit the conguraon from the [edit batch] mode, do one of the following:
• Log in to the device and enter commit.
[edit batch]
user@R0# commit
Added to commit queue request-id: 1000
• To assign a higher priority to a batch commit job, issue the commit command with the priority opon.
[edit batch]
user@R0# commit priority
Added to commit queue request-id: 1001
191

• To commit a conguraon without aggregang the conguraon changes with other commit jobs in
the queue, issue the commit command with the atomic opon.
[edit batch]
user@R0# commit atomic
Added to commit queue request-id: 1002
• To commit a conguraon without aggregang the conguraon changes with other commit jobs in
the queue, and issuing a higher priority to the commit job, issue the commit command with the atomic
priority opon.
[edit batch]
user@R0# commit atomic priority
Added to commit queue request-id: 1003
Vericaon
IN THIS SECTION
Checking the Batch Commit Server Status | 192
Checking the Batch Commit Status | 193
Viewing the Patch Files in a Batch Commit Job | 194
Viewing the Trace Files for Batch Commit Operaons | 197
Conrm that the conguraon is working properly.
Checking the Batch Commit Server Status
Purpose
Check the status of the batch commit server.
192

Acon
user@R0> show system commit server
Commit server status : Not running
By default, the status of the commit server is Not running. The commit server starts running only when a
batch commit job is added to the queue.
When a batch commit job is added to the queue, the status of the commit server changes to Running.
user@R0> show system commit server
Commit server status : Running
Jobs in process:
1003 1004 1005
Meaning
The Jobs in process eld lists the commit IDs of jobs that are in process.
Checking the Batch Commit Status
Purpose
Check the commit server queue for the status of the batch commits.
Acon
user@R0> show system commit server queue
Pending commits:
Id: 1005
Last Modified: Tue Nov 1 23:56:43 2018
Completed commits:
Id: 1000
Last Modified: Tue Nov 1 22:46:43 2018
Status: Successfully committed 1000
Id: 1002
193

Last Modified: Tue Nov 1 22:50:35 2018
Status: Successfully committed 1002
Id: 1004
Last Modified: Tue Nov 1 22:51:48 2018
Status: Successfully committed 1004
Id: 1007
Last Modified: Wed Nov 2 01:08:04 2018
Status: Successfully committed 1007
Id: 1009
Last Modified: Wed Nov 2 01:16:45 2018
Status: Successfully committed 1009
Id: 1010
Last Modified: Wed Nov 2 01:19:25 2018
Status: Successfully committed 1010
Id: 1011
Last Modified: Wed Nov 2 01:28:16 2018
Status: Successfully committed 1011
Error commits:
Id: 1008
Last Modified: Wed Nov 2 01:08:18 2018
Status: Error while commiting 1008
Meaning
Pending commits displays commit jobs that are added to the commit queue but are not commied yet.
Completed commits displays the list of commit jobs that are successful. Error commits are commits that failed
because of an error.
Viewing the Patch Files in a Batch Commit Job
Purpose
View the mestamps, patch les, and the status of each of the commit jobs. Patch les show the
conguraon changes that occur in each commit operaon that is added to the batch commit queue.
194

Acon
1. Use the show system commit server queue patch command to view the patches for all commit operaons.
user@R0> show system commit server queue patch
Pending commits:
none
Completed commits:
Id: 1000
Last Modified: Tue Nov 1 22:46:43 2018
Status: Successfully committed 1000
Patch:
[edit groups]
re1 { ... }
+ GRP-DHCP-POOL-NOACCESS {
+ access {
+ address-assignment {
+ pool <*> {
+ family inet {
+ dhcp-attributes {
+ maximum-lease-time 300;
+ grace-period 300;
+ domain-name verizon.net;
+ name-server {
+ 4.4.4.1;
+ 4.4.4.2;
+ }
+ }
+ }
+ }
+ }
+ }
+ }
Id: 1002
Last Modified: Tue Nov 1 22:50:35 2018
Status: Successfully committed 1002
Patch:
[edit]
195

+ snmp {
+ community abc;
+ }
Id: 1010
Last Modified: Wed Nov 2 01:19:25 2018
Status: Successfully committed 1010
Patch:
[edit system syslog]
file test { ... }
+ file j {
+ any any;
+ }
Error commits:
Id: 1008
Last Modified: Wed Nov 2 01:08:18 2018
Status: Error while commiting 1008
Patch:
[edit system]
+ radius-server {
+ 10.1.1.1 port 222;
+ }
The output shows the changes in conguraon for each commit job ID.
2. To view the patch for a specic commit job ID, issue the show system commit server queue patch id
<id-
number>
command.
user@R0> show system commit server queue patch id 1000
Completed commits:
Id: 1000
Last Modified: Tue Nov 1 22:46:43 2018
Status: Successfully committed 1000
Patch:
[edit system]
+ radius-server {
+ 192.168.69.162 secret teH.bTc/RVbPM;
+ 192.168.64.10 secret teH.bTc/RVbPM;
+ 192.168.60.52 secret teH.bTc/RVbPM;
196

+ 192.168.60.55 secret teH.bTc/RVbPM;
+ 192.168.4.240 secret teH.bTc/RVbPM;
+ }
Meaning
The output shows the patch created for a commit job. The + or - sign indicates the changes in the
conguraon for a specic commit job.
Viewing the Trace Files for Batch Commit Operaons
Purpose
View the trace les for batch commit operaons. You can use the trace les for troubleshoong
purposes.
Acon
• Use the file show /var/log/
<filename>
command to view all entries in the log le.
user@R0> file show/var/log/commitd_nov
The output shows commit server event logs and other logs for batch commits.
Nov 1 22:46:43 Successfully committed 1000
Nov 1 22:46:43 pausing after commit for 0 seconds
...
Nov 1 22:46:43 Done working on queue
...
Nov 1 22:47:17 maximum-aggregate-pool = 5
Nov 1 22:47:17 maximum-entries= 0
Nov 1 22:47:17 asynchronous-prompt = no
Nov 1 22:47:17 commit-interval = 0
Nov 1 22:47:17 days-to-keep-error-logs = -1
...
Nov 1 22:47:17 Added to commit queue request-id: 1001
Nov 1 22:47:17 Commit server status=running
Nov 1 22:47:17 No need to pause
...
197

Nov 1 22:47:18 Error while commiting 1001
Nov 1 22:47:18 doing rollback
...
• To view log entries only for successful batch commit operaons, issue the file show /var/log/
<filename>
command with the | match committed pipe opon.
The output shows batch commit job IDs for successful commit operaons.
user@R0> file show/var/log/commitd_nov | match committed
Nov 1 22:46:43 Successfully committed 1000
Nov 1 22:50:35 Successfully committed 1002
Nov 1 22:51:48 Successfully committed 1004
Nov 2 01:08:04 Successfully committed 1007
Nov 2 01:16:45 Successfully committed 1009
Nov 2 01:19:25 Successfully committed 1010
Nov 2 01:28:16 Successfully committed 1011
• To view log entries only for failed batch commit operaons, issue the file show /var/log/
<filename>
command with the | match “Error while” pipe opon.
The output shows commit job IDs for failed commit operaons.
user@R0> file show/var/log/commitd_nov | match “Error while”
Nov 1 22:47:18 Error while commiting 1001
Nov 1 22:51:10 Error while commiting 1003
Nov 1 22:52:15 Error while commiting 1005
...
• To view log entries only for commit server events, issue the file show /var/log/
<filename>
command
with the | match “commit server” pipe opon.
The output shows commit server event logs.
user@R0> file show/var/log/commitd_nov | match “commit server”
Nov 1 22:46:39 Commit server status=running
Nov 1 22:46:39 Commit server jobs=1000
Nov 1 22:46:43 Commit server status=not running
198

Nov 1 22:46:43 Commit server jobs=
Nov 1 22:47:17 Commit server status=running
Nov 1 22:47:18 Commit server jobs=1001
Nov 1 22:47:18 2 errors reported by commit server
Nov 1 22:47:18 Commit server status=not running
Nov 1 22:47:18 Commit server jobs=
Nov 1 22:50:31 Commit server status=running
Nov 1 22:50:31 Commit server jobs=1002
Nov 1 22:50:35 Commit server status=not running
Nov 1 22:50:35 Commit server jobs=
Nov 1 22:51:09 Commit server status=running
Nov 1 22:51:10 Commit server jobs=1003
Nov 1 22:51:10 2 errors reported by commit server
Nov 1 22:51:10 Commit server status=not running
...
Back Up the Commied Conguraon on the Alternate Boot Drive
Aer you commit the conguraon and are sased that it is running successfully, you should issue the
request system snapshot command to back up the new soware onto the /altconfig le system. If you do
not issue the request system snapshot command, the conguraon on the alternate boot drive is out of
sync with the conguraon on the primary boot drive.
The request system snapshot command backs up the root le system to /altroot, and /config to /altconfig.
The root and /config le systems are on the router’s ash drive, and the /altroot and /altconfig le
systems are on the router’s hard disk (if available).
Aer you issue the request system snapshot command, you cannot return to the previous version of the
soware because the running and backup copies of the soware are idencal.
RELATED DOCUMENTATION
Overview of the Congure Command | 65
199

4
CHAPTER
Managing Conguraons
Conguraon Files Overview | 201
Managing Conguraons | 203
Autoinstallaon of Conguraon Files Overview | 226
Loading Conguraon Files | 231
Back Up Conguraons to an Archive Site | 249
Factory Default Conguraon Overview | 252
Rescue Conguraon | 253
Encrypt and Decrypt Conguraon Files | 255
Example: Protecng the Junos OS Conguraon from Modicaon or Deleon |
259
Synchronizing Conguraons Across Roung Engines | 270

Conguraon Files Overview
IN THIS SECTION
Conguraon Files Overview | 201
Device Conguraon Storage Overview | 203
You use conguraon les to congure devices and to streamline device conguraon tasks. A
conguraon le stores the complete conguraon of a device. Keep in mind these disncons
between conguraon les:
• The acve (running) conguraon is the operaonal le of the device. These les control device
behavior.
• The candidate conguraon is the working copy that stores conguraon updates. These are the
les that you use to automac device conguraon.
Conguraon Files Overview
IN THIS SECTION
Conguraon File Terms | 202
A conguraon le stores the complete conguraon of a network device. The current conguraon of
a device is called the acve conguraon. You can alter this current conguraon, and you can also
return to a previous conguraon or to a rescue conguraon.
The 50 most recently commied conguraon les on a device are saved so that you can return to a
previous conguraon. The conguraon les are named as follows:
• juniper.conf.gz—The current acve conguraon
•
juniper.conf.1.gz to juniper.conf.49.gz—Rollback conguraons
201

To make changes to the conguraon le, you must use conguraon mode in the CLI. When making
changes to a conguraon le, you are viewing and changing the candidate conguraon le. The
candidate conguraon enables you to make conguraon changes without causing operaonal
changes to the acve conguraon or causing potenal damage to your current network operaons.
Aer you commit the changes you made to the candidate conguraon, the system updates the acve
conguraon.
Conguraon File Terms
Table 8: Conguraon File Terms
Term Denion
acve conguraon Current commied conguraon of a device.
candidate conguraon Working copy of the conguraon that enables users to make conguraonal changes
without causing any operaonal changes unl this copy is commied.
conguraon group Group of conguraon statements that the rest of the conguraon can inherit.
commit a conguraon The act of checking a conguraon for proper syntax, acvang it, and marking as the
current conguraon le running on the device.
conguraon hierarchy A hierarchy of statements comprising the system conguraon. The two types of
statements are container and leaf: Container statements contain other statements.
Leaf statements do not contain other statements. All the container and leaf statements
together form the conguraon hierarchy.
default conguraon The inial values set for each conguraon parameter when a device is shipped.
rescue conguraon Well-known conguraon that recovers a device from a conguraon that denies
management access. Through the CLI, you set a current commied conguraon to be
the rescue conguraon.
roll back a conguraon The act of returning to a previously commied conguraon.
202

Device Conguraon Storage Overview
When you edit a Juniper Networks device conguraon, you work in a copy of the current conguraon
to create a candidate conguraon. The changes that you make to the candidate conguraon are
visible in the CLI immediately. Therefore, if mulple users are eding the conguraon at the same me,
all users can see all changes.
You commit your changes to cause a candidate conguraon to take eect. At this point, the candidate
le is checked for proper syntax, acvated, and marked as the current, operaonal soware
conguraon le. If mulple users are eding the conguraon simultaneously, all changes made by all
the users take eect when you commit the candidate conguraon.
In addion to saving the current conguraon, the CLI saves the current operaonal version and the
previous 49 versions of commied conguraons. The most recently commied conguraon is version
0, which is the current operaonal version. This current operaonal version is the default conguraon
that the system returns to if you roll back to a previous conguraon. The oldest saved conguraon is
version 49.
By default, the current conguraon and three previous versions of the commied conguraon are
saved on the device CompactFlash card. The currently operaonal device conguraon is stored in the
le juniper.conf.gz, and the last three commied conguraons are stored in the les juniper.conf.1.gz,
juniper.conf.2.gz, and conf.3.gz. These four les are stored on the device’s CompactFlash card in the
directory /cong.
The remaining 46 previous versions of commied conguraons, the les juniper.conf.4 through
juniper.conf.49, are stored in the directory /var/db/cong on the hard disk.
Managing Conguraons
IN THIS SECTION
The show | compare | display xml Command Output | 204
Returning to the Most Recently Commied Conguraon | 213
Returning to a Previously Commied Conguraon | 214
Using Conguraon Revision Ideners | 218
Saving a Conguraon to a File | 220
About Compressing the Current Conguraon File | 221
203

Free Up System Storage Space | 222
Clean Up Files with the CLI | 224
The show | compare | display xml Command Output
IN THIS SECTION
Add a Statement (create Operaon) | 205
Delete a Statement (delete Operaon) | 206
Change a Statement (delete and create Operaons) | 208
Change Metadata (inacve Aribute and Operaon) | 208
Add an Annotaon (comment Tag and create Operaon) | 210
Change an Annotaon (comment Tag, and delete and create Operaons) | 211
Add a Statement Inside a Container (create Operaon, and insert and key Aributes) | 211
Change the Order Inside a Container (merge Operaon, and insert and key Aributes) | 212
The compare | display xml lter compares the candidate conguraon with the current commied
conguraon and displays the dierences between the two conguraons in XML. To compare
conguraons, enter compare | display xml aer the pipe ( | ) symbol in either operaonal or conguraon
mode.
Example in operaonal mode:
user@host> show configuration | compare | display xml
Example in conguraon mode:
[edit]
user@host# show | compare | display xml
204

You can enter a specic conguraon hierarchy immediately preceding the compare lter, for example, show
configuration system syslog | compare | display xml. In conguraon mode, you can navigate to a hierarchy
where the command is applied.
The dierences from the compare lter funcon are output in XML. The configuration tag starts the
output. The context for changes is established with hierarchy name tags relave to the root of the
compare. For element changes, an operation aribute is output in the tag where a change occurs. This
aribute has the value create, delete, or merge. For metadata changes, the metadata name is specied. For
example, if a statement is marked inacve, the inactive="inactive" aribute and value are output. The nc
namespace is used when necessary to indicate that an aribute is in the NETCONF namespace rather
than the operang system namespace.
NOTE: Beginning with Junos OS Release 16.2R2, the show | compare | display xml command omits
the <configuration> tag in the XML output if the comparison returns no dierences or if the
comparison returns only dierences for non-nave conguraon data, for example, conguraon
data associated with an OpenCong data model.
The following secons explain the XML that is generated for specic types of conguraon changes.
The corresponding text changes are shown for comparison.
Add a Statement (create Operaon)
The following example shows the addion of IPv4 address 2.2.2.2 to unit 1.
The tags through name provide the context for the addion. The operation="create" aribute indicates that
a unit statement was created and is dened by the conguraon within the unit tag.
[edit interfaces ge-0/0/0]
user@host> show configuration | compare
[edit interfaces ge-0/0/0]
+ unit 1 {
+ family inet {
+ address 2.2.2.2/32;
+ }
+ }
[edit interfaces ge-0/0/0]
user@host# show | compare | display xml
<configuration>
<interfaces>
<interface>
205

<name>ge-0/0/0</name>
<unit nc:operation="create">
<name>1</name>
<family>
<inet>
<address>
<name>2.2.2.2/32</name>
</address>
</inet>
</family>
</unit>
</interface>
</interfaces>
</configuration>
Delete a Statement (delete Operaon)
The following example shows the deleon of a simple statement in the conguraon hierarchy. The tags
through system provide the context for the deleon. The operation="delete" aribute indicates that the
services statement was deleted. The conguraon following the services statement was deleted though is
not output.
[edit system]
user@host> show configuration | compare
[edit system]
- services {
- ftp;
- }
[edit system]
user@host# show | compare | display xml
<configuration>
<system>
<services operation="delete"/>
</system>
</configuration>
206

The following example shows the deleon of unit 1 from the ge-0/0/0 interface. The conguraon
following the unit statement was deleted though is not output.
[edit interfaces ge-0/0/0]
user@host> show configuration | compare
[edit interfaces ge-0/0/0]
- unit 1 {
- family inet {
- address 2.2.2.2/32;
- }
- }
[edit interfaces ge-0/0/0]
user@host# show | compare | display xml
<configuration>
<interfaces>
<interface>
<name>ge-0/0/0</name>
<unit nc:operation="delete">
<name>1</name>
</unit>
</interface>
</interfaces>
</configuration>
The following example shows the deleon of the apply-groups conguraon. The groups that are deleted
are not shown in the output.
[edit]
user@host# delete apply-groups
[edit]
user@host> show configuration | compare
[edit]
- apply-groups [ g1 g2 g3 ];
[edit]
user@host# show | compare | display xml
<configuration>
<apply-groups operation="delete"/>
</configuration>
207

Change a Statement (delete and create Operaons)
The following example shows a change in a statement in the hierarchy. The tags through system provide
the context for the change. The operation="delete" aribute indicates that the host-name statement was
deleted. The conguraon following the host-name statement was deleted, but this is not shown in the
output. The operation="create" aribute indicates that a host-name statement was created and is dened by
the conguraon within the host-name tag.
[edit system]
user@host> show configuration | compare
[edit system]
- host-name router1;
+ host-name router2;
[edit system]
user@host# show | compare | display xml
<configuration>
<system>
<host-name nc:operation="delete"/>
<host-name nc:operation="create">router2</host-name>
</system>
</configuration>
Change Metadata (inacve Aribute and Operaon)
The following example shows the inacvaon of a statement in the hierarchy. The tags through system
provide the context for the change. The inactive="inactive" aribute indicates that the syslog statement
was inacvated.
[edit system]
user@host> show configuration | compare
[edit system]
! inactive: syslog { ... }
[edit system]
user@host# show | compare | display xml
<configuration>
<system>
<syslog inactive="inactive"/>
208

</system>
</configuration>
The following example shows the addion of an inacve syslog statement. The operation="create" aribute
indicates that the syslog statement was created and is dened by the conguraon within the syslog tag.
The inactive="inactive" aribute indicates that the syslog statement was inacvated.
[edit system]
user@host> show configuration | compare
[edit system]
+ inactive: syslog {
+ file foo {
+ any any;
+ }
+ }
[edit system]
user@host# show | compare | display xml
<configuration>
<system>
<syslog nc:operation="create"
inactive="inactive">
<file>
<name>foo</name>
<contents>
<name>any</name>
<any/>
</contents>
</file>
</syslog>
</system>
</configuration>
209

Add an Annotaon (comment Tag and create Operaon)
The following example shows the addion of a comment to a statement. The tags through syslog provide
the context for the annotaon. The operation="create" aribute for the junos:comment tag indicates that a
comment was added to the [edit system syslog] hierarchy.
[edit system]
user@host> show configuration | compare
[edit system]
+ /* my-comments-simple */
syslog { ... }
[edit system]
user@host# show | compare | display xml
<configuration>
<system>
<junos:comment nc:operation="create">/* my-comments-simple
*/</junos:comment>
<syslog/>
</system>
</configuration>
The following example shows the addion of a comment to a statement. The tags through syslog provide
the context for the annotaon. The operation="create" aribute for the junos:comment tag indicates that a
comment was added to the [edit system syslog] hierarchy for the statement output within the syslog tag.
[edit system syslog]
user@host> show configuration | compare
+ /* my-comments-ele */
file f1 { ... }
[edit system syslog]
user@host# show | compare | display xml
<configuration>
<system>
<syslog>
<junos:comment nc:operation="create">/* my-comments-elem
*/</junos:comment>
<file>
<name>f1</name>
</file>
210

</syslog>
</system>
</configuration>
Change an Annotaon (comment Tag, and delete and create Operaons)
The following example shows the change of a comment for a statement. The tags through system provide
the context for the annotaon.
• The operation="delete" aribute for the junos:comment tag indicates that a comment was deleted from
the [edit system] hierarchy at the syslog statement.
• The operation="create" aribute for the junos:comment tag indicates that a comment was added to the
[edit system] hierarchy for the syslog statement.
[edit system]
user@host> show configuration | compare
- /* my-comments-1 */
+ /* my-comments-2 */
syslog { ... }
[edit system]
user@host# show | compare | display xml
<configuration>
<system>
<junos:comment nc:operation="delete"/>
<junos:comment nc:operation="create">/* my-comments-2
*/</junos:comment>
<syslog/>
</system>
</configuration>
Add a Statement Inside a Container (create Operaon, and insert and key Aributes)
The following example shows the addion of a file statement at the [edit system syslog] hierarchy. The
tags through syslog provide the context for the addion.
• The operation="create" aribute for the file tag indicates that a file statement was added.
•
The yang:insert="after" aribute indicates that the le was added aer the posion indicated by the
yang:key="[name='file-1']" aribute.
211

• The le-1 value represents the posion within the exisng file statements, where one is the rst le.
• In this example, the new file statement was added aer the rst le.
[edit system syslog]
user@host> show configuration | compare
[edit system syslog]
file file-1 { ... }
+ file file-2 {
+ any any;
+ }
[edit system syslog]
user@host# show | compare | display xml
<configuration>
<system>
<syslog>
<file nc:operation="create"
yang:insert="after"
yang:key="[name='file-1']">
<name>file-2</name>
<contents>
<name>any</name>
<any/>
</contents>
</file>
</syslog>
</system>
</configuration>
Change the Order Inside a Container (merge Operaon, and insert and key Aributes)
The following example shows the change in order of file statements at the [edit system syslog] hierarchy.
The tags through syslog provide the context for the change.
•
The operation="merge" aribute for the file tag indicates that an exisng file statement was moved.
• The yang:insert="after" aribute indicates that the le was moved aer the le in the posion
indicated by the yang:key="[name='file-1']" aribute.
• The le-1 value represents a posion within the exisng file statements, where one is the rst le.
•
The value at the name tag, le-3, represents a posion within the exisng le statements.
212

• In this example, the file statement in the third posion was moved aer the rst le.
[edit system syslog]
user@host> show configuration | compare
[edit system syslog]
file f1 { ... }
! file f3 { ... }
[edit system syslog]
user@host# show | compare | display xml
<configuration>
<system>
<syslog>
<file nc:operation="merge"
yang:insert="after"
yang:key="[name='file-1']">
<name>file-3</name>
</file>
</syslog>
</system>
</configuration>
Returning to the Most Recently Commied Conguraon
To return to the most recently commied conguraon and load it into conguraon mode without
acvang it, use the rollback conguraon mode command:
[edit]
user@host# rollback
load complete
To acvate the conguraon to which you rolled back, use the commit command:
[edit]
user@host# rollback
213

load complete
[edit]
user@host# commit
Returning to a Previously Commied Conguraon
IN THIS SECTION
Example of Returning to a Previous Conguraon | 214
Example of Displaying Previous Conguraons | 214
About Comparing Conguraon Versions | 216
This topic explains how you can return to an earlier conguraon than the most recently commied one.
Example of Returning to a Previous Conguraon
To return to a previous conguraon, you include the conguraon number, 0 through 49, in the rollback
command. The most recently saved conguraon is number 0 (which is the default conguraon to
which the system returns), and the oldest saved conguraon is number 49.
Example:
[edit]
user@host# rollback
number
load complete
Example of Displaying Previous Conguraons
To display previous conguraons, you use the rollback ? command. You include the rollback number,
date, me, the name of the user who commied changes, and the method of commit.
Example:
[edit]
user@host# rollback ?
Possible completions:
214

<[Enter]> Execute this command
<number> Numeric argument
0 2018-02-27 12:52:10 PST by abc via cli
1 2018-02-26 14:47:42 PST by def via cli
2 2018-02-14 21:55:45 PST by ghi via cli
3 2018-02-10 16:11:30 PST by jkl via cli
4 2018-02-10 16:02:35 PST by mno via cli
5 2018-03-16 15:10:41 PST by pqr via cli
6 2018-03-16 14:54:21 PST by stu via cli
7 2018-03-16 14:51:38 PST by vwx via cli
8 2018-03-16 14:43:29 PST by yzz via cli
9 2018-03-16 14:15:37 PST by abc via cli
10 2018-03-16 14:13:57 PST by def via cli
11 2018-03-16 12:57:19 PST by root via other
12 2018-03-16 10:45:23 PST by root via other
13 2018-03-16 10:08:13 PST by root via other
14 2018-03-16 01:20:56 PST by root via other
15 2018-03-16 00:40:37 PST by ghi via cli
16 2018-03-16 00:39:29 PST by jkl via cli
17 2018-03-16 00:32:36 PST by mno via cli
18 2018-03-16 00:31:17 PST by pqr via cli
19 2018-03-15 19:59:00 PST by stu via cli
20 2018-03-15 19:53:39 PST by vwx via cli
21 2018-03-15 18:07:19 PST by yzz via cli
22 2018-03-15 17:59:03 PST by abc via cli
23 2018-03-15 15:05:14 PST by def via cli
24 2018-03-15 15:04:51 PST by ghi via cli
25 2018-03-15 15:03:42 PST by jkl via cli
26 2018-03-15 15:01:52 PST by mno via cli
27 2018-03-15 14:58:34 PST by pqr via cli
28 2018-03-15 13:09:37 PST by root via other
29 2018-03-12 11:01:20 PST by stu via cli
30 2018-03-12 10:57:35 PST by vwx via cli
31 2018-03-11 10:25:07 PST by yzz via cli
32 2018-03-10 23:40:58 PST by abc via cli
33 2018-03-10 23:40:38 PST by def via cli
34 2018-03-10 23:14:27 PST by ghi via cli
35 2018-03-10 23:10:16 PST by jkl via cli
36 2018-03-10 23:01:51 PST by mno via cli
37 2018-03-10 22:49:57 PST by pqr via cli
38 2018-03-10 22:24:07 PST by stu via cli
39 2018-03-10 22:20:14 PST by vwx via cli
40 2018-03-10 22:16:56 PST by yzz via cli
215

41 2018-03-10 22:16:41 PST by abc via cli
42 2018-03-10 20:44:00 PST by def via cli
43 2018-03-10 20:43:29 PST by ghi via cli
44 2018-03-10 20:39:14 PST by jkl via cli
45 2018-03-10 20:31:30 PST by root via other
46 2018-03-10 18:57:01 PST by mno via cli
47 2018-03-10 18:56:18 PST by pqr via cli
48 2018-03-10 18:47:49 PST by stu via cli
49 2018-03-10 18:47:34 PST by vw via cli
| Pipe through a command
[edit]
About Comparing Conguraon Versions
In conguraon mode only, when you have made changes to the conguraon, you can compare the
candidate conguraon with a prior version. To compare versions, you use the compare command to
display the conguraons. The compare command compares the candidate conguraon with either the
current commied conguraon or a conguraon le. This command also displays the dierences
between the two conguraons.
To compare conguraons, you specify the compare command aer the pipe:
[edit]
user@host# show | compare (
filename
| rollback
n
)
•
filename
is the full path to a conguraon le. The le must be in the proper format: a hierarchy of
statements.
•
n
is the index into the list of previously commied conguraons. The most recently saved
conguraon is number 0, and the oldest saved conguraon is number 49. If you do not specify
arguments, the system compares candidate conguraon against the acve conguraon le (/
cong/juniper.conf).
The comparison output includes the following symbols in the prex for statements that are:
• In the candidate conguraon only: a plus sign (+).
• In the comparison le only: a minus sign (-).
• Unchanged; a single blank space ( ).
216

The following example shows various changes, followed by a comparison of the candidate conguraon
with the acve conguraon. The example shows only the changes made at the [edit protocols bgp]
hierarchy level:
[edit]
user@host# edit protocols bgp
[edit protocols bgp]
user@host# show
group my-group {
type internal;
hold-time 60;
advertise-inactive;
allow 10.1.1.1/8;
}
group fred {
type external;
peer-as 33333;
allow 10.2.2.2/8;
}
group test-peers {
type external;
allow 10.3.3.3/8;
}
[edit protocols bgp]
user@host# set group my-group hold-time 90
[edit protocols bgp]
user@host# delete group my-group advertise-inactive
[edit protocols bgp]
user@host# set group fred advertise-inactive
[edit protocols bgp]
user@host# delete group test-peers
[edit protocols bgp]
user@host# show | compare
[edit protocols bgp group my-group]
-hold-time 60;
+hold-time 90;
-advertise-inactive;
[edit protocols bgp group fred]
+advertise-inactive;
[edit protocols bgp]
-group test-peers {
-type external;
217

-allow 10.3.3.3/8;
}
[edit protocols bgp]
user@host# show
group my-group {
type internal;
hold-time 90;
allow 10.1.1.1/8;
}
group fred {
type external;
advertise-inactive;
peer-as 3333;
allow 10.2.2.2/8;
}
Using Conguraon Revision Ideners
Every commit has a conguraon revision idener (CRI) associated with it. The CRI is a unique string
that, unlike the rollback index, does not change when new conguraons are commied.
Because the CRI for a given commied conguraon is xed, it has advantages over using a rollback
index. Network management systems (NMS) can cache the CRI for a given commit. At a later date, the
NMS can compare the cached value to the CRI of the current conguraon on the network device to
detect if other systems made out-of-band conguraon changes to the device, for example, during a
maintenance window.
Addionally, starng in Junos OS and Junos OS Evolved Release 20.4R1, you can use the CRI associated
with a commied conguraon to:
• View the conguraon.
• Compare two conguraons.
• Revert to the conguraon.
• Retrieve the current rollback index associated with that conguraon.
218

To view the CRI associated with each commit, use the show system commit include-configuration-revision
command. This will display the system commit history and the CRI for each commit.
user@host> show system commit include-configuration-revision
0 2020-08-02 00:42:58 IST by user via cli re0-1596309177-4
1 2020-08-02 00:42:53 IST by user via cli re0-1596309173-3
2 2020-08-02 00:42:50 IST by user via cli re0-1596309170-2
3 2020-08-02 00:42:40 IST by user via other re0-1596309160-1
Alternavely, you can view the CRI for a specic rollback number by issuing the show system rollback
number
configuration-revision command.
user@host> show system rollback 0 configuration-revision
The corresponding configuration revision is: re0-1596309177-4
Once you have the CRI string for a specic commit, you can view that conguraon with the show system
configuration revision
cri-string
command.
user@host> show system configuration revision re0-1596309177-4
You can compare 2 conguraons by using the compare opon with both CRIs.
user@host> show system configuration revision compare re0-1596309177-4 re0-1596309173-3
You can also use view the rollback number for a specic CRI by including the rollback-number
cri-string
opon.
user@host> show system configuration revision rollback-number re0-1596309160-1
The corresponding rollback number is: 3
Addionally, in conguraon mode, you can roll back to a conguraon by specifying the CRI instead of
the rollback index.
[edit]
user@host# rollback revision re0-1596309160-1
load complete
219

[edit]
user@host# commit
Saving a Conguraon to a File
Saving a device conguraon to a le allows you to edit it with any plain text editor of your choice. You
can save your current conguraon to an ASCII le, which saves the conguraon in its current form,
including any uncommied changes. If more than one user is modifying the conguraon, all changes
made by all users are saved.
To save soware conguraon changes to an ASCII le, use the save conguraon mode command:
[edit]
user@host# save
filename
[edit]
user@host#
The contents of the current level of the statement hierarchy (and below) are saved, along with the
statement hierarchy containing it. This allows a secon of the conguraon to be saved, while fully
specifying the statement hierarchy.
By default, the conguraon is saved to a le in your home directory, which is on the ash drive.
When you issue this command from anywhere in the hierarchy (except the top level), a replace tag is
automacally included at the beginning of the le. You can use the replace tag to control how a
conguraon is loaded from a le.
Example:
user@host> file show /var/home/user/myconf
replace:
protocols {
bgp {
disable;
group int {
type internal;
}
}
isis {
disable;
220

interface all {
level 1 disable;
}
interface fxp0.0 {
disable;
}
}
ospf {
traffic-engineering;
reference-bandwidth 4g;
...
}
}
About Compressing the Current Conguraon File
By default, the current operaonal conguraon le is compressed and is stored in the le
juniper.conf.gz in the /cong le system. The operaonal conguraon le is stored along with the last
three commied versions of the conguraon. If you have large networks, the current conguraon le
might exceed the available space in the /cong le system. Compressing the current conguraon le
enables the le to t in the le system, typically reducing the size of the le by 90 percent. You might
want to compress your current operaonal conguraon les when they reach 3 megabytes (MB) in
size.
When you compress the current conguraon le, the names of the conguraon les change. To
determine the size of the les in the /cong le system, you issue the file list /config detail command.
NOTE: We recommend that you compress the conguraon les (this is the default) to minimize
the amount of disk space that they require.
• If you want to compress the current conguraon le, include the compress-configuration-files
statement at the [edit system] hierarchy level:
[edit system]
compress-configuration-files;
221

• Commit the current conguraon le to include the compression-configuration-files statement. Commit
the conguraon again to compress the current conguraon le:
[edit system]
user@host# set compress-configuration-files
user@host# commit
commit complete
• If you do not want to compress the current operaonal conguraon le, include the no-compress-
configuration-files statement at the [edit system] hierarchy level:
[edit system]
no-compression-configuration-files;
• Commit the current conguraon le to include the no-compress-configuration-files statement. Commit
the conguraon again to uncompress the current conguraon le:
[edit system]
user@host# set no-compress-configuration-files
user@host# commit
commit complete
Free Up System Storage Space
IN THIS SECTION
Problem | 223
Soluon | 223
222

Problem
Descripon
The system le storage space on the device is full. Reboong the switch does not solve the problem.
The following error message appears during a typical operaon on the device aer the le storage space
is full:
user@host% cli
user@host> configure
/var: write failed, filesystem is full
Soluon
Clean up the le storage on the device by deleng system les.
1. Issue a request to clean up (delete) system les.
user@host> request system storage cleanup
The list of les to be deleted is displayed.
List of files to delete:
Size Date Name
11B Jul 26 20:55 /var/jail/tmp/alarmd.ts
124B Aug 4 18:05 /var/log/default-log-messages.0.gz
1301B Jul 26 20:42 /var/log/install.0.gz
387B Jun 3 14:37 /var/log/install.1.gz
4920B Aug 4 18:05 /var/log/messages.0.gz
20.0K Jul 26 21:00 /var/log/messages.1.gz
16.3K Jun 25 13:45 /var/log/messages.2.gz
804B Aug 4 18:05 /var/log/security.0.gz
16.8K Aug 3 11:15 /var/log/security.1.gz
487B Aug 4 18:04 /var/log/wtmp.0.gz
855B Jul 29 22:54 /var/log/wtmp.1.gz
920B Jun 30 16:32 /var/log/wtmp.2.gz
94B Jun 3 14:36 /var/log/wtmp.3.gz
353.2K Jun 3 14:37 /var/sw/pkg/jloader-qfx-11.2I20110303_1117_dc-builder.tgz
223

124.0K Jun 3 14:30 /var/tmp/gres-tp/env.dat
0B Apr 14 16:20 /var/tmp/gres-tp/lock
0B Apr 14 17:37 /var/tmp/if-rtsdb/env.lck
12.0K Jul 26 20:55 /var/tmp/if-rtsdb/env.mem
2688.0K Jul 26 20:55 /var/tmp/if-rtsdb/shm_usr1.mem
132.0K Jul 26 20:55 /var/tmp/if-rtsdb/shm_usr2.mem
2048.0K Jul 26 20:55 /var/tmp/if-rtsdb/trace.mem
155B Jul 26 20:55 /var/tmp/krt_gencfg_filter.txt
0B Jul 26 20:55 /var/tmp/rtsdb/if-rtsdb
1400.6K Aug 3 10:13 /var/tmp/sfid.core.0.gz
1398.9K Aug 3 17:01 /var/tmp/sfid.core.1.gz
Delete these files ? [yes,no] (no)
2. Select yes to delete the les.
3. Reboot the device.
BEST PRACTICE: We recommend that you regularly issue a request to clean up the system
le storage. Cleaning up the system le storage space opmizes device performance.
Clean Up Files with the CLI
You can use the CLI request system storage cleanup command to rotate log les and delete unnecessary les
on the device. If you are running low on storage space, the le cleanup procedure quickly idenes les
that you can delete.
The le cleanup procedure performs the following tasks:
• Rotates log les—Archives all informaon in the current log les, deletes old archives, and creates
fresh log les.
• Deletes log les in /var/log—Deletes any les that are not currently being wrien to.
• Deletes temporary les in /var/tmp—Deletes any les that have not been accessed within two days.
•
Deletes all crash les in /var/crash—Deletes any core les that the device has wrien during an error.
• Deletes all soware images (*.tgz les) in /var/sw/pkg—Deletes any soware images copied to this
directory during soware upgrades.
To rotate log les and delete unnecessary les with the CLI:
224

1. Enter operaonal mode in the CLI.
2. Rotate log les and idenfy the les that you can safely delete.
user@host> request system storage cleanup
The device rotates log les and displays the les that you can delete.
3. Enter yes at the prompt to delete the les.
NOTE: You can issue the request system storage cleanup dry-run command to review the list of les
that you can safely delete . The dry-run acon lets you review the list before you issue the request
system storage cleanup command to delete the les.
NOTE: On SRX Series Firewalls, the /var hierarchy is hosted in a separate paron (instead of the
root paron). If the operang system installaon fails as a result of insucient space:
• Use the request system storage cleanup command to delete temporary les.
• Delete any user-created les in both the root paron and under the /var hierarchy.
Change History Table
Feature support is determined by the plaorm and release you are using. Use Feature Explorer to
determine if a feature is supported on your plaorm.
Release
Descripon
16.2R2
Beginning with Junos OS Release 16.2R2, the show | compare | display xml command omits the
<configuration> tag in the XML output if the comparison returns no dierences or if the comparison
returns only dierences for non-nave conguraon data, for example, conguraon data associated
with an OpenCong data model.
225

Autoinstallaon of Conguraon Files Overview
IN THIS SECTION
Conguraon File Autoinstallaon—An Overview | 226
Conguring Autoinstallaon of Conguraon Files (CLI Procedure) | 229
Autoinstallaon is the automac conguraon of devices over the network without manual
intervenon, including manual conguraon. You (the network administrator) use autoinstallaon to
save me and to implement the same conguraon consistently across devices.
Conguraon File Autoinstallaon—An Overview
IN THIS SECTION
Typical Uses for Autoinstallaon | 227
Autoinstallaon Conguraon Files and IP Addresses | 227
Typical Autoinstallaon Process on a New Device | 227
Autoinstallaon is the automac conguraon of a device over the network from a preexisng
conguraon le that you create and store on a conguraon server—typically a Trivial File Transfer
Protocol (TFTP) server. You can use autoinstallaon to congure new devices automacally and to
deploy mulple devices from a central locaon in the network.
You enable autoinstallaon so that network devices implement autoinstallaon when they are powered
on. To congure autoinstallaon, you specify a conguraon server, an autoinstallaon interface, and a
protocol for IP address acquision.
226

NOTE: The QFX5200 switches work only with HTTP for autoinstallaon. They do not support
TFTP or FTP protocols. Autoinstallaon as a feature is not supported on all devices. Refer to your
hardware informaon for specic details.
Typical Uses for Autoinstallaon
Typical uses for autoinstallaon of the soware include:
• Deploy and update mulple devices from a central locaon in the network.
• Update a device automacally, when powered on.
Autoinstallaon Conguraon Files and IP Addresses
For the autoinstallaon process to work, you must store one or more host-specic or default
conguraon les on a conguraon server in the network. In addion, you must ensure that a service
such as Dynamic Host Conguraon Protocol (DHCP) is available to assign an IP address to thedevice.
You can set up the following conguraon les for autoinstallaon on the device:
• network.conf—Default conguraon le for autoinstallaon, in which you specify IP addresses and
associated hostnames for devices on the network.
• switch.conf—Default conguraon le for autoinstallaon on a switch. This le contains just enough
conguraon informaon for you to telnet to the device and congure it manually.
•
hostname
.conf—Host-specic conguraon le for autoinstallaon on a device. This le contains all
the conguraon informaon necessary for the device. In the lename, replace
hostname
with the
hostname assigned to the device.
If the server with the autoinstallaon conguraon le is not on the same LAN segment as the new
device, or if a specic device is required by the network, you must congure an intermediate device. You
must aach this intermediate device directly to the new device so that the new device can send TFTP,
Boot Protocol (BOOTP), and Domain Name System (DNS) requests through the intermediate device. In
this case, you specify the IP address of the intermediate device as the locaon at which to receive TFTP
autoinstallaon requests.
Typical Autoinstallaon Process on a New Device
When the device congured for autoinstallaon is powered on, it performs the following autoinstallaon
tasks:
227
1. The device sends out DHCP or BOOTP requests on each connected interface simultaneously to
obtain an IP address.
If a DHCP server responds to these requests, it provides the device with some or all of the following
informaon:
• An IP address and subnet mask for the autoinstallaon interface.
• The locaon of the (typically) TFTP server, HTTP server, or FTP server on which the conguraon
le is stored.
• The name of the conguraon le to be requested from the TFTP server.
• The IP address or hostname of the TFTP server.
If the DHCP server provides the server’s hostname, a DNS server must be available on the
network to resolve the name to an IP address.
• The IP address of an intermediate device if the conguraon server is on a dierent LAN segment
from the device.
2. Aer the device acquires an IP address, the autoinstallaon process on the device aempts to
download a conguraon le in the following ways:
a. If the DHCP server species the host-specic conguraon le
hostname
.conf, the device uses
that lename in the TFTP server request. The autoinstallaon process on the new device makes
three unicast TFTP requests for
hostname
.conf. If these aempts fail, the device broadcasts three
requests to any available TFTP server for the le.
b. If the device does not locate a
hostname
.conf le, the autoinstallaon process sends three unicast
TFTP requests for a network.conf le that contains the device’s hostname-to-IP-address mapping
informaon. If these aempts fail, the device broadcasts three requests to any available TFTP
server for the le.
c. If the device fails to nd a network.conf le that contains a hostname entry for the device, the
autoinstallaon process sends out a DNS request and aempts to resolve the device's IP address
to a hostname.
d. If the device determines its hostname, it sends a TFTP request for the
hostname
.conf le.
e. If the device is unable to map its IP address to a hostname, it sends TFTP requests for the default
conguraon le device.conf. The TFTP request procedure is the same as for the network.conf
le.
3. Aer the device locates a conguraon le on a TFTP server, the autoinstallaon process downloads
the le, installs the le on the device, and commits the conguraon.
228

Conguring Autoinstallaon of Conguraon Files (CLI Procedure)
Autoinstallaon is the automac conguraon of a device over the network from a pre-exisng
conguraon le that you create and store on a conguraon server. A conguraon server is typically a
Trivial File Transfer Protocol (TFTP) server. You can use autoinstallaon to deploy mulple devices
automacally from a central locaon in the network.
Before you can congure autoinstallaon, you must enable autoinstallaon to run when you power on a
device already installed in your network. You enable it by specifying one or more interfaces, protocols,
and conguraon servers to be used for autoinstallaon.
To enable autoinstallaon to run, complete the following steps:
1. Ensure that a service such as Dynamic Host Conguraon Protocol (DHCP) is available to assign an
IP address to the device.
2. Congure a DHCP server on your network to meet your network requirements. You can congure a
switch to operate as a DHCP server.
3. Create one of the following conguraon les, and store it on a TFTP server (or HTTP server or FTP
server) in the network:
• A host-specic le with the name
hostname
.conf for each device undergoing autoinstallaon.
Replace
hostname
with the name of a device. The
hostname
.conf le typically contains all the
conguraon informaon necessary for the device with this hostname.
• A default conguraon le named device.conf with the minimum conguraon necessary to
enable you to telnet into the new device for further conguraon.
4. Physically aach the device to the network using a Gigabit Ethernet port.
5. If you congured the DHCP server to provide only the TFTP server hostname, add an IP address-to-
hostname mapping entry for the TFTP server. Map the TFTP server hostname to the DNS database
le on the Domain Name System (DNS) server in the network.
6. If the device is not on the same network segment as the DHCP server (or other device providing IP
address resoluon), congure an exisng device as an intermediate device to receive TFTP and DNS
requests and forward them to the TFTP server and the DNS server. You must congure the LAN or
serial interface on the intermediate device with the IP addresses of the hosts providing TFTP and
DNS services. Connect this interface to the device.
7. If you are using
hostname
.conf les for autoinstallaon, you must also complete the following tasks:
• Congure the DHCP server to provide a
hostname
.conf lename to each device. Each device uses
its
hostname
.conf lename to request a conguraon le from the TFTP server. Copy the
necessary
hostname
.conf conguraon les to the TFTP server.
229

• Create a default conguraon le named network.conf, and copy it to the TFTP server. This le
contains IP-address-to-hostname mapping entries. If the DHCP server does not send a
hostname
.conf lename to a new device, the device uses network.conf to resolve its hostname
based on its IP address.
Alternavely, you can add the IP-address-to-hostname mapping entry for the device to a DNS
database le.
The device uses the hostname to request a
hostname
.conf le from the TFTP server.
Before you explicitly enable and congure autoinstallaon on the device, perform these tasks as needed
for your network conguraon:
To congure autoinstallaon:
1. Specify the URL address of one or more servers from which to obtain conguraon les.
[edit system]
user@host# set autoinstallation configuration-servers tftp://tftpconfig.example.com
NOTE: You can also use an FTP address such as p://
user
:
password
@spcong.example.com.
2. Congure one or more Ethernet interfaces to perform autoinstallaon and one or two procurement
protocols for each interface. The switch uses the protocols to send a request for an IP address for the
interface:
[edit system]
user@host# set autoinstallation interfaces ge-0/0/0 bootp
To verify autoinstallaon, from the CLI enter the show system autoinstallation status command.
Example:
user@host> show system autoinstallation status
Autoinstallation status:
Master state: Active
Last committed file: None
Configuration server of last committed file: 10.25.100.1
Interface:
Name: ge-0/0/0
230

State: Configuration Acquisition
Acquired:
Address: 192.168.124.75
Hostname: host-ge-000
Hostname source: DNS
Configuration filename: device-ge-000.conf
Configuration filename server: 10.25.100.3
Address acquisition:
Protocol: DHCP Client
Acquired address: None
Protocol: RARP Client
Acquired address: None
Interface:
Name: ge-0/0/1
State: None
Address acquisition:
Protocol: DHCP Client
Acquired address: None
Protocol: RARP Client
Acquired address: None
Loading Conguraon Files
IN THIS SECTION
Examples for Loading a Conguraon from a File or the Terminal | 232
How Character Encoding Works on Juniper Networks Devices | 235
About Specifying Statements and Ideners | 237
About Loading a Conguraon from a File | 241
Upload a Conguraon File | 245
Load JSON Conguraon Data With Unordered List Entries | 246
Loading conguraon les on the device are helpful for loading parts of conguraon les that might be
common across many devices within a network.
231

Examples for Loading a Conguraon from a File or the Terminal
You can create a le containing conguraon data for a Juniper Networks device, copy the le to the
local device, and then load the le into the CLI. Aer you have loaded the le, you can commit it to
acvate the conguraon on the device, or you can edit the conguraon interacvely using the CLI
and commit the conguraon at a later me.
You can also create a conguraon while typing at the terminal and then load the conguraon. Loading
a conguraon from the terminal is useful when you are cung exisng porons of the conguraon
and pasng them elsewhere in the conguraon.
To load an exisng conguraon le that is located on the device, you use the load conguraon mode
command:
[edit]
user@host# load (factory-default | merge | override | patch | replace | set | update)
filename
<relative> <json>
To load a conguraon from the terminal, you use the following version of the load conguraon mode
command. Press Ctrl-d to end the input.
[edit]
user@host# load (factory-default | merge | override | patch | replace | set | update) terminal
<relative> <json>
To replace an enre conguraon, you specify the override opon at any level of the hierarchy. A load
override operaon completely replaces the current candidate conguraon with the le you are loading.
Thus, if you saved a complete conguraon, you use this opon.
An override operaon discards the current candidate conguraon and loads the conguraon in
lename
or the conguraon that you type at the terminal. When you use the override opon and
commit the conguraon, all system processes reparse the conguraon.
To replace porons of a conguraon, you specify the replace opon. The load replace operaon looks for
replace: tags that you added to the loaded le. The operaon then replaces those parts of the candidate
conguraon with whatever is specied aer the tag. This is useful when you want more control over
exactly what is being changed. For this operaon to work, you must include replace: tags in the le or
conguraon that you type at the terminal. The soware searches for the replace: tags, deletes the
exisng statements of the same name, if any, and replaces them with the incoming conguraon. If no
statement of the same name exists, the replace operaon adds to the conguraon the statements
marked with the replace: tag.
232
If, in an override or merge operaon, you specify a le or type text that contains replace: tags, the replace:
tags are ignored. In this scenario, the override or merge operaon takes precedence and is performed.
If you are performing a replace operaon, and if the le that you specify lacks replace: tags, the replace
operaon runs as a merge operaon. The replace operaon also runs as a merge operaon if the text you
type lacks replace: tags. This informaon might be useful if you are running automated scripts and
cannot know in advance whether the scripts need to perform a replace operaon or a merge operaon.
The scripts can use the replace operaon to cover either case.
The load merge operaon merges the conguraon from the saved le or terminal with the exisng
candidate conguraon. This informaon is useful if you are adding new conguraon secons. For
example, suppose that you are adding a BGP conguraon to the [edit protocols] hierarchy level, where
there was no BGP conguraon before. You can use the load merge operaon to combine the incoming
conguraon with the exisng candidate conguraon. If the exisng conguraon and the incoming
conguraon contain conicng statements, the statements in the incoming conguraon override
those in the exisng conguraon.
To replace only those parts of the conguraon that have changed, you specify the update opon at any
level of the hierarchy. The load update operaon compares the candidate conguraon and the new
conguraon data. This operaon changes only those parts of the candidate conguraon that are
dierent from the new conguraon. You would use this operaon, for example, if there is an exisng
BGP conguraon and the le you are loading changes it in some way.
The merge, override, and update opons support loading conguraon data in JavaScript Object Notaon
(JSON) format. When loading conguraon data that uses JSON format, you must specify the json
opon in the command. To load JSON conguraon data that contains unordered list entries, that is, list
entries where the list key is not necessarily the rst element in the list entry, see "Load JSON
Conguraon Data With Unordered List Entries" on page 246.
To change part of the conguraon with a patch le, you specify the patch opon. The load patch
operaon loads a le or terminal input that contains conguraon changes. First, on a device that
already has the conguraon changes, you type the show | compare command to output the dierences
between two conguraons. Then you can load the dierences on another device. The advantage of the
load patch command is that it saves you from having to copy snippets from dierent hierarchy levels into
a text le before loading them into the target device. This might be a useful me saver if you are
conguring several devices with the same opons. For example, suppose that you congure a roung
policy on router1 and you want to replicate the policy conguraon on router2, router3, and router4.
You can use the load patch operaon.
In this example, you rst run the show | compare command.
233

Example:
user@router1# show | compare rollback 3
[edit protocols ospf]
+ export default-static;
- export static-default
[edit policy-options]
+ policy-statement default-static {
+ from protocol static;
+ then accept;
+ }
Connuing this example, you copy the output of the show | compare command to the clipboard, making
sure to include the hierarchy levels. On router2, router3, and router4, you type load patch terminal and
paste the output. You then press Enter and press Ctrl-d to end the operaon. If the patch input species
dierent values for an exisng statement, the patch input overrides the exisng statement.
To use the merge, replace, set, or update opon without specifying the full hierarchy level, you specify the
relative opon. This opon loads the incoming conguraon relave to your current edit point in the
conguraon hierarchy.
Example:
[edit system]
user@host# show static-host-mapping
bob sysid 987.654.321ab
[edit system]
user@host# load replace terminal relative
[Type ^D at a new line to end input]
replace: static-host-mapping {
bob sysid 0123.456.789bc;
}
load complete
[edit system]
user@host# show static-host-mapping
bob sysid 0123.456.789bc;
To load a conguraon that contains set conguraon mode commands, specify the set opon. This
opon executes the conguraon instrucons line by line as they are stored in a le or from a terminal.
The instrucons can contain any conguraon mode command, such as set, edit, exit, and top.
234

To copy a conguraon le from another network system to the local router, you can use the SSH and
Telnet ulies, as described in the CLI Explorer.
NOTE: If you are working in a Common Criteria environment, system log messages are created
whenever a secret aribute is changed (for example, password changes or changes to the
RADIUS shared secret). These changes are logged during the following conguraon load
operaons:
load merge
load replace
load override
load update
How Character Encoding Works on Juniper Networks Devices
Junos OS conguraon data and operaonal command output might contain non-ASCII characters,
which are outside of the 7-bit ASCII character set. When displaying operaonal or conguraon data in
certain formats or within a certain type of session, the soware escapes and encodes these characters.
The soware escapes or encodes the characters using the equivalent UTF-8 decimal character
reference.
The CLI aempts to display any non-ASCII characters in conguraon data that is produced in text, set,
or JSON format. The CLI also aempts to display these characters in command output that is produced
in text format. In the excepon cases, the CLI displays the UTF-8 decimal character reference instead.
(Excepon cases include conguraon data in XML format and command output in XML or JSON
format,) In NETCONF and Junos XML protocol sessions, you see a similar result if you request
conguraon data or command output that contains non-ASCII characters. In this case, the server
returns the equivalent UTF-8 decimal character reference for those characters for all formats.
For example, suppose the following user account, which contains the Lan small leer n with a lde (ñ),
is congured on the device.
[edit]
user@host# set system login user mariap class super-user uid 2007 full-name "Maria Peña"
235

When you display the resulng conguraon in text format, the CLI prints the corresponding character.
[edit]
user@host# show system login user mariap
full-name "Maria Peña";
uid 2007;
class super-user;
When you display the resulng conguraon in XML format in the CLI, the ñ character maps to its
equivalent UTF-8 decimal character reference ñ. The same result occurs if you display the
conguraon in any format in a NETCONF or Junos XML protocol session.
[edit]
user@host# show system login user mariap | display xml
<rpc-reply xmlns:junos="http://xml.juniper.net/junos/17.2R1/junos">
<configuration junos:changed-seconds="1494033077" junos:changed-localtime="2017-05-05
18:11:17 PDT">
<system>
<login>
<user>
<name>mariap</name>
<full-name>Maria Peña</full-name>
<uid>2007</uid>
<class>super-user</class>
</user>
</login>
</system>
</configuration>
<cli>
<banner>[edit]</banner>
</cli>
</rpc-reply>
When you load conguraon data onto a device, you can load non-ASCII characters using their
equivalent UTF-8 decimal character references.
236

About Specifying Statements and Ideners
IN THIS SECTION
Specifying Statements | 237
Performing CLI Type Checking | 239
This topic provides details about CLI container statements and leaf statements so that you know how to
must specify them when creang ASCII conguraon les. This topic also describes how the CLI
performs type checking to verify that the data you entered is in the correct format.
Specifying Statements
Statements are shown one of two ways, either with braces ({ }) or without:
• Statement name and idener, with one or more lower-level statements enclosed in braces:
statement-name1
identifier-name
{
statement-name2
;
additional-statements
;
}
• Statement name, idener, and a single idener:
statement-name
identifier-name1
identifier-name2
;
The
statement-name
is the name of the statement. The
idener-name
is a name or other string that
uniquely idenes an instance of a statement. You use an idener when a statement can be specied
more than once in a conguraon.
When specifying a statement, you must specify a statement name, an idener name, or both,
depending on the statement hierarchy.
You specify ideners in one of the following ways:
•
idener-name
—The
idener-name
is a keyword used to uniquely idenfy a statement when a
statement can be specied more than once in a statement.
237

•
idener-name value
—The
idener-name
is a keyword, and the
value
is a required opon variable.
•
idener-name
[
value1 value2 value3
...]—The
idener-name
is a keyword that accepts mulple
values. The brackets are required when you specify a set of values; however, they are oponal when
you specify only one value.
The following examples illustrate how statements and ideners are specied in the conguraon:
protocol { # Top-level statement (
statement-name
).
ospf { # Statement under "protocol" (
statement-name
).
area 0.0.0.0 { # OSPF area "0.0.0.0" (
statement-name identifier-name
),
interface so-0/0/0 { # which contains an interface named "so-0/0/0."
hello-interval 25; # Identifier and value (
identifier-name value
).
priority 2; # Identifier and value (
identifier-name value
).
disable; # Flag identifier (
identifier-name
).
}
interface so-0/0/1; # Another instance of "interface," named so-0/0/1,
} # this instance contains no data, so no braces
} # are displayed.
}
policy-options { # Top-level statement (
statement-name
).
term term1 { # Statement under "policy-options"
# (
statement-name value
).
from { # Statement under "term" (
statement-name
).
route-filter 10.0.0.0/8 orlonger reject; # One identifier ("route-
filter") with
route-filter 127.0.0.0/8 orlonger reject; # multiple values.
route-filter 128.0.0.0/16 orlonger reject;
route-filter 149.20.64.0/24 orlonger reject;
route-filter 172.16.0.0/12 orlonger reject;
route-filter 191.255.0.0/16 orlonger reject;
}
then { # Statement under "term" (
statement-name
).
next term; # Identifier (
identifier-name
).
}
}
}
When you create an ASCII conguraon le, you specify statements and ideners. Each statement has
a preferred style, and the CLI uses that style when displaying the conguraon in response to a
conguraon mode show command. You can specify statements and ideners in one of the following
ways:
238

• Statement followed by ideners:
statement-name identifier-name
[...]
identifier-name
value
[...];
• Statement followed by ideners enclosed in braces:
statement-name
{
identifier-name
;
[...]
identifier-name
value
;
[...]
}
• For some repeang ideners, you can use one set of braces for all the statements:
statement-name
{
identifier-name value1
;
identifier-name value2
;
}
Performing CLI Type Checking
When you specify ideners and values, the CLI performs type checking to verify that the data you
entered is in the correct format. For example, for a statement in which you must specify an IP address,
the CLI requires that you enter an address in a valid format. Otherwise, an error message indicates what
you need to type. lists the data types the CLI checks. The following are CLI conguraon input types:
Table 9: CLI
Conguraon Input Types
Data Type Format Examples
Physical interface
name (used in the
[edit interfaces]
hierarchy)
type-fpc
/
pic
/
port
Correct: et-0/0/1
Incorrect: et-0
239

Table 9: CLI Conguraon Input Types
(Connued)
Data Type Format Examples
Full interface name
type-fpc
/
pic
/
port
<:
channel
>.
logical
Correct: et-0/0/1.0
Incorrect: et-0/0/1
Full or abbreviated
interface name
(used in places
other than the [edit
interfaces]
hierarchy)
type-
<
fpc
</
pic
/
port
>><<:
channel
>.
logical>
Correct: et, et-1, et-1/2/3:4.5
IP address
0x
hex-bytesoctet
<.
octet
<.
octet
.
<
octet
>>>
Correct: 1.2.3.4, 0x01020304, 128.8.1, 128.8
Sample translaons:
1.2.3 becomes 1.2.3.0
0x01020304 becomes 1.2.3.4
0x010203 becomes 0.1.2.3
IP address
(desnaon prex)
and prex length
0x
hex-bytes
<
/length
>
octet
<
octet
<
octet
.<
octet
>>><
/length
>
Correct: 10/8, 128.8/16, 1.2.3.4/32, 1.2.3.4
Sample translaons:
1.2.3 becomes 1.2.3.0/32
0x01020304 becomes 1.2.3.4/32
0x010203 becomes 0.1.2.3/32
default becomes 0.0.0.0/0
Internaonal
Organizaon for
Standardizaon
(ISO) address
hex-nibble
<
hex-nibble
...> Correct: 47.1234.2345.3456.00, 47123423453456.00,
47.12.34.23.45.34.56.00
Sample translaons:
47123456 becomes 47.1234.56
47.12.34.56 becomes 47.1234.56
4712.3456 becomes 47.1234.56
240

Table 9: CLI Conguraon Input Types
(Connued)
Data Type Format Examples
OSPF area
idener (ID)
0x
hex-bytesoctet
<.
octet
<.
octet
.<
octet
>>>
decimal-number
Correct: 54, 0.0.0.54, 0x01020304, 1.2.3.4
Sample translaons:
54 becomes 0.0.0.54
257 becomes 0.0.1.1
128.8 becomes 128.8.0.0
0x010203 becomes 0.1.2.3
About Loading a
Conguraon from a File
The following examples demonstrate the process of loading a conguraon from a le.
Figure 5: Overriding the Current Conguraon
241

Figure 6: Using the replace Opon
Figure 7: Using the merge Opon
242

Figure 8: Using a Patch File
243

Figure 9: Using the set Opon
244
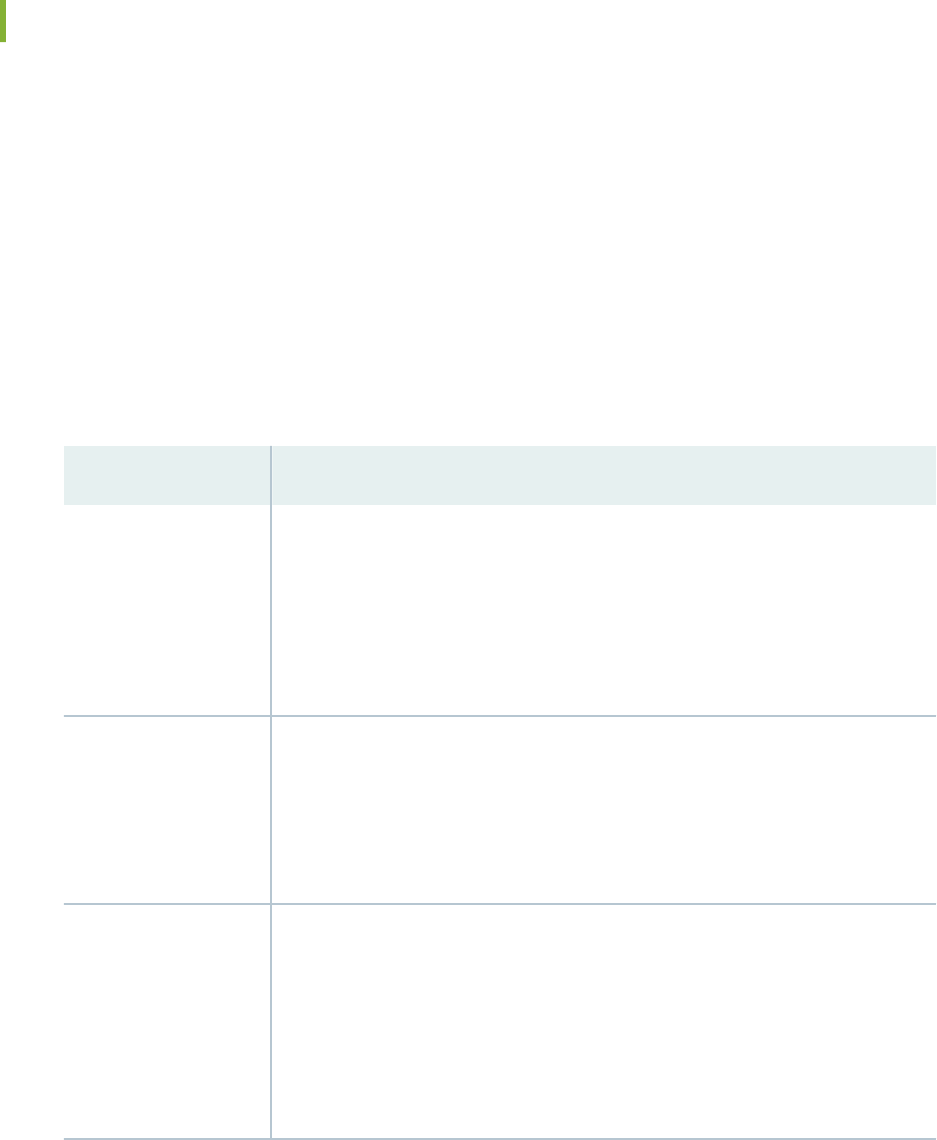
Upload a Conguraon File
You can create a conguraon le on your local system, copy the le to the device, and then load the le
into the CLI. Aer you have loaded the conguraon le, you can commit it to acvate the conguraon
on the device. You can also edit the conguraon interacvely using the CLI and commit it at a later
me.
To upload a conguraon le from your local system:
1. Create the conguraon le using a text editor such as Notepad, making sure that the syntax of the
conguraon le is correct.
2. In the conguraon text le, include one or more of the following opons to perform the required
acon when the le is loaded.
Table 10: Opons for the load Command
Opons Descripon
merge Combines the current acve conguraon with either the conguraon in the
lename that you specify or the conguraon that you type in the terminal
window. A merge operaon is useful when you are adding a new secon to an
exisng conguraon. If the acve conguraon and the incoming conguraon
contain conicng statements, the statements in the incoming conguraon
override those in the acve conguraon.
override Discards the current candidate conguraon. Loads either the conguraon in
the lename that you specify or the conguraon that you type at the terminal.
When you use the override opon and commit the conguraon, all system
processes reparse the conguraon. You can use the override opon at any level
of the hierarchy.
replace Searches for the replace tags, deletes the exisng statements of the same name,
if any, and replaces the exisng statements with the incoming conguraon. If no
statement of the same name exists, the replace operaon adds the statements
marked with the replace tag to the acve conguraon.
NOTE: For this operaon to work, you must include replace tags in the text le or
in the conguraon that you enter at the terminal.
3. Press Ctrl+a to select all the text in the conguraon le.
4. Press Ctrl+c to copy the contents of the conguraon text le to the Clipboard.
5. Log in to the device using your username and password.
245

6. Enter conguraon mode: user@host> configure
[edit]
user@host#
7. Load the conguraon le: [edit] user@host# load merge terminal
8. At the cursor, paste the contents of the Clipboard using the mouse and the Paste icon: [edit]
user@host# load merge terminal [Type ^D at a new line to end input] >Cursor is here. Paste the
contents of the clipboard here<
9. Press Enter.
10. Press Ctrl+d to set the end-of-le marker.
To view results of the conguraon steps before comming the conguraon, type the show command
at the user prompt.
To commit these changes to the acve conguraon, type the commit command at the user prompt. You
can also edit the conguraon interacvely using the CLI and commit it at a later me.
Load JSON Conguraon Data With Unordered List Entries
The Junos schema denes certain conguraon objects as lists. In JSON conguraon data, a list
instance is encoded as a name/array pair, and the array elements are JSON objects. Generally, the order
of members in a JSON-encoded list entry is arbitrary because JSON objects are fundamentally
unordered collecons of members. However, the Junos schema requires that list keys precede any other
siblings within a list entry and appear in the order specied by the schema.
For example, the user object at the [edit system login] hierarchy level is a list where name is the list key that
uniquely idenes each user.
list user {
key name;
description "Username";
uses login-user-object;
}
In the following sample conguraon data, the list key (name) is the rst element for each user. By default,
when you load JSON conguraon data, Junos devices require that the list keys precede any other
siblings within a list entry and appear in the order specied by the schema.
{
"configuration" : {
246

"system" : {
"login" : {
"user" : [
{
"name" : "operator",
"class" : "operator",
"uid" : 3001
},
{
"name" : "security-admin",
"class" : "super-user",
"uid" : 3002
}
]
}
}
}
}
Junos devices provide two opons to load JSON conguraon data that contains unordered list entries,
that is, list entries where the list key is not necessarily the rst element.
• Use the request system convert-json-configuration operaonal mode command to produce JSON
conguraon data with ordered list entries before loading the data on the device.
• Congure the reorder-list-keys statement at the [edit system configuration input format json] hierarchy
level. Aer you congure the statement, you can load JSON conguraon data with unordered list
entries, and the device reorders the list keys as required by the Junos schema during the load
operaon.
NOTE: When you congure the reorder-list-keys statement, the load operaon can take
signicantly longer to parse the conguraon, depending on the size of the conguraon and the
number of lists. Thus, for large conguraons or conguraons with many lists, we recommend
using the request system convert-json-configuration command instead of the reorder-list-keys
statement.
247

For example, suppose the user-data.json le contains the following JSON conguraon. If you tried to
load the conguraon, the device would emit a load error for admin2 because the list key name is not the
rst element in that list entry.
user@host> file show /var/tmp/user-data.json
{
"configuration" : {
"system" : {
"login" : {
"user" : [
{
"name" : "admin1",
"class" : "super-user",
"uid" : 3003
},
{
"class" : "super-user",
"name" : "admin2",
"uid" : 3004
}
]
}
}
}
}
If you use the request system convert-json-configuration command with the previous le as input, the
command generates the specied output le with JSON conguraon data that the Junos device can
parse during the load operaon.
user@host> request system convert-json-configuration /var/tmp/user-data.json output-filename
user-data-ordered.json
user@host> file show user-data-ordered.json
{
"configuration":{
"system":{
"login":{
"user":[
{
"name":"admin1",
248

"class":"super-user",
"uid":3003
},
{
"name":"admin2",
"class":"super-user",
"uid":3004
}
]
}
}
}
}
Alternavely, you can congure the reorder-list-keys conguraon statement.
user@host# set system configuration input format json reorder-list-keys
user@host# commit
Aer you congure the statement, you can load the original JSON conguraon le with unordered list
entries, and the device handles the list entries when it parses the conguraon.
user@host# load merge json /var/tmp/user-data.json
load complete
Back Up Conguraons to an Archive Site
IN THIS SECTION
Congure the Transfer of the Acve Conguraon | 250
You can congure a device to transfer its conguraon to an archive le periodically.
249

Congure the Transfer of the Acve Conguraon
If you want to back up your device’s current conguraon to an archive site, you can congure the
device to transfer its acve conguraon by FTP, HTTP, secure copy (SCP), or SFTP periodically or aer
each commit.
To congure the device to transfer its acve conguraon to an archive site, include statements at the
[edit system archival configuration] hierarchy level:
[edit system archival configuration]
archive-sites {
file:/
path
;
file:///
path
;
ftp://
username
@
host
<:
port
>//
url-path
;
http://
username
@
host
<:
port
>/
url-path
;
scp://
username
@
host
<:
port
>/
url-path
;
sftp://
username
@
host
<:
port
>/
url-path
;
}
routing-instance
routing-instance
;
transfer-interval
interval
;
transfer-on-commit;
When you congure the device to transfer its conguraon les, you specify an archive site to which
the les are transferred. If you specify more than one archive site, the device aempts to transfer les to
the rst archive site in the list, moving to the next site only if the transfer fails.
When you use the archive-sites statement, you can specify a desnaon as an FTP URL, HTTP URL,
SCP-style remote le specicaon, or SFTP URL. The URL type le: is also supported. When you specify
the archive site, do not add a forward slash (/) to the end of the URL.
NOTE:
• The URL type le: is supported only for local les.
• When using the FTP opon, specify a double forward slash (//) aer the host:port. For
example: p://username@host<:port>//url-path
le:/path/ is the minimal representaon of a local le with no authority eld and an absolute path that
begins with a slash "/" as dened in RFC 8089.
le:///path is an example for a tradional le URI for a local le with an empty authority as dened in
RFC 8089.
250

NOTE: When specifying a URL in a statement using an IPv6 host address, you must enclose the
enre URL in quotaon marks ("") and enclose the IPv6 host address in brackets ([ ]). For
example, "p://
username
<:
password
>@[
ipv6-host-address
]<:
port
>//
url-path
"
To congure the device to periodically transfer its acve conguraon to an archive site, include the
transfer-interval statement at the [edit system archival configuration] hierarchy level:
[edit system archival configuration]
transfer-interval
interval
;
The
interval
is a period of me ranging from 15 through 2880 minutes.
To congure the device to transfer the conguraon to an archive site each me you commit the
conguraon, include the transfer-on-commit statement at the [edit system archival configuration] hierarchy
level:
[edit system archival configuration]
transfer-on-commit;
If the network device reaches the archive server through a specic roung instance, congure the
routing-instance statement at the [edit system archival configuration] hierarchy level, and specify the
roung instance.
[edit system archival configuration]
routing-instance
routing-instance
;
The desnaon lename is saved in the following format, where
n
corresponds to the number of the
compressed conguraon rollback le that has been archived:
<
router-name
>_
YYYYMMDD_HHMMSS
_juniper.conf.
n
.gz
NOTE: The me included in the desnaon lename is in Coordinated Universal Time (UTC).
251
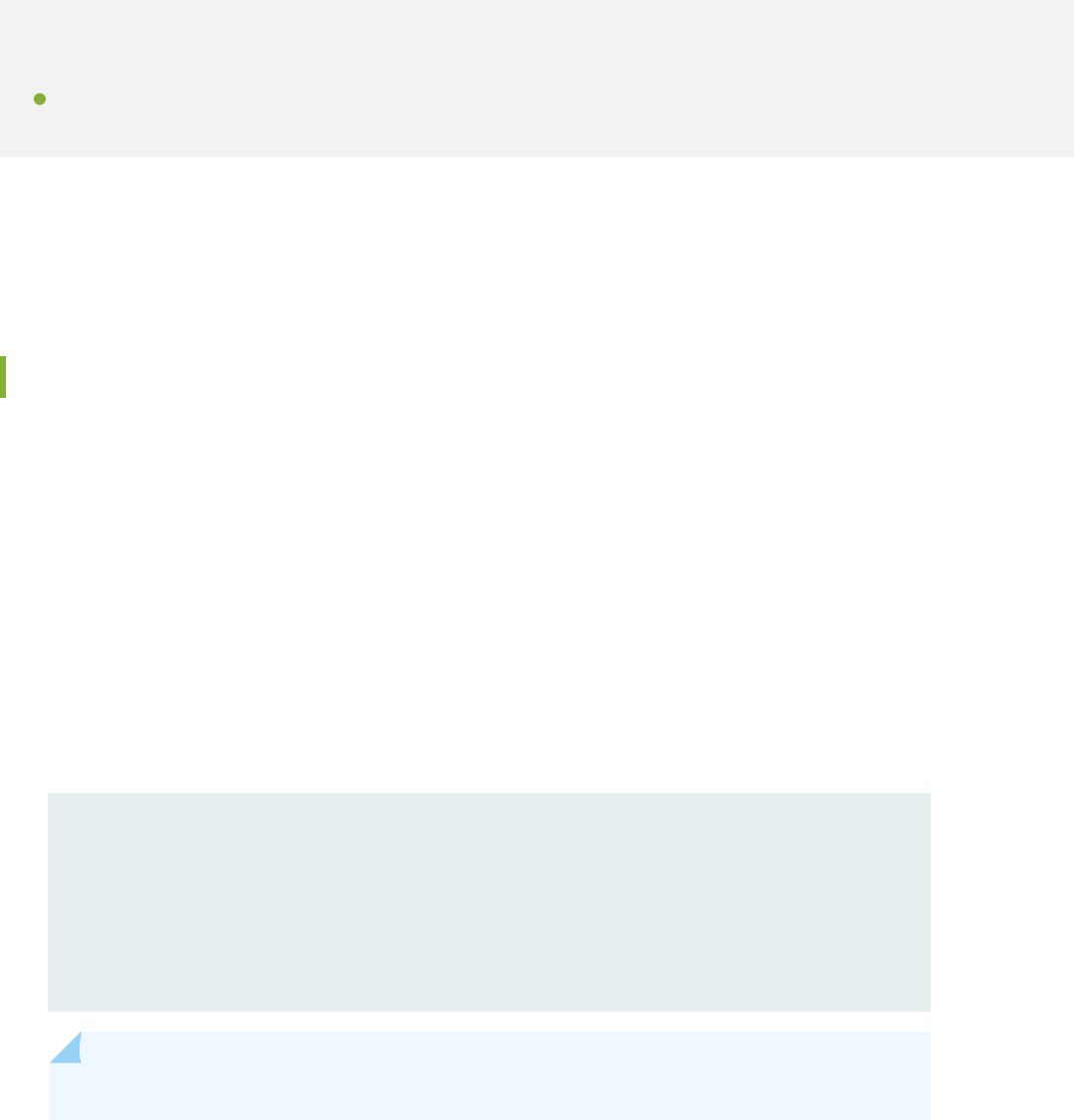
Factory Default Conguraon Overview
IN THIS SECTION
Restore the Default Factory Conguraon | 252
The default factory conguraon contains the basic device conguraon sengs. This rst
conguraon of the device is loaded automacally the rst me you install the device and power it on.
Restore the Default Factory Conguraon
If for any reason the current acve conguraon fails, you can restore the default factory conguraon.
The default factory conguraon contains the basic conguraon sengs and is somemes referred to
as the rescue conguraon. This is the rst conguraon of the device and is loaded the rst me you
install the device and power it on.
The load factory default command is a standard conguraon command. This conguraon command
replaces the current acve conguraon with the default factory conguraon.
To restore the switch to the default factory conguraon:
1. Make sure you are in conguraon mode.
2. Enter the following commands at the CLI:
[edit]
user@switch# load factory-default
[edit]
user@switch# delete system commit factory-settings
[edit]
user@switch# commit
NOTE: This process clears prior commied conguraon parameters, except for those that
preserve a Virtual Chassis conguraon. A Virtual Chassis is a group of devices congured to
252

work together as if they were a single device. You can use the load factory-default command to
restore the factory default conguraon on a Virtual Chassis without removing anything
needed to keep the Virtual Chassis working.
3. Make sure you congure the root (superuser) password. Set the root authencaon password and
commit. If you congure the plain-text-password opon, you are prompted to enter and conrm the
password.
[edit]
user@switch# set system root-authentication plain-text-password
New password:
type password here
Retype new password:
retype password here
user@switch# commit
SEE ALSO
No Link Title
Rescue Conguraon
IN THIS SECTION
Creang and Returning to a Rescue Conguraon | 253
A rescue conguraon is the known working conguraon. If the acve conguraon is corrupted, the
device automacally loads the rescue conguraon le as the acve conguraon.
Creang and Returning to a Rescue Conguraon
A
rescue conguraon
allows you to dene a known working conguraon or a conguraon with a
known state for recovery, if necessary. This alleviates the necessity of having to remember the rollback
number with the
rollback
command. The rescue conguraon rolls back the device to a known
253

conguraon, or can serve as a last resort if your device conguraon and the backup conguraon les
become damaged beyond repair.
To save the most recently commied conguraon as the rescue conguraon so that you can return to
it at any me, issue the request system configuration rescue save command:
user@host> request system configuration rescue save
To return to the rescue conguraon, use the rollback rescue conguraon mode command. To commit
the rescue conguraon, thereby acvang it, use the commit command.
[edit]
user@host# rollback rescue
load complete
NOTE: If the rescue conguraon does not exist, or if the rescue conguraon is not a complete,
viable conguraon, then the rollback command fails, an error message appears, and the current
conguraon remains acve.
To delete an exisng rescue conguraon, issue the request system configuration rescue delete command:
user@host> request system configuration rescue delete
user@host>
NOTE: We recommend seng the rescue conguraon. This enables the device to automacally
load the rescue conguraon le as the acve conguraon if for any reason the current acve
conguraon fails. A minor alarm Rescue configuration is not set is raised if you do not set the
rescue conguraon using the request system configuration rescue save command.
254

Encrypt and Decrypt Conguraon Files
IN THIS SECTION
Encrypt Conguraon Files | 255
Decrypt Conguraon Files | 257
Modify the Encrypon Key | 258
You store conguraon data and sensive network informaon in conguraon les. Encrypng
conguraon les enables you to secure the informaon they store. Decrypng means disabling the
encrypon of conguraon les on a device and making the les readable to all.
NOTE: Encrypon features are not available on all Juniper Networks devices. If these features
are not available on one or more of your devices, the Junos OS CLI encrypon-related commands
described in this topic may be hidden or may not funcon. See your hardware documentaon for
details.
Encrypt Conguraon Files
To encrypt conguraon les on a Juniper Networks device, you need an encrypon key. You congure
an encrypon key in EEPROM and determine which encrypon process is appropriate for your network.
To congure an encrypon key, select the most appropriate request system set-encryption-key command in
operaonal mode, as described in the following table.
255

Table 11: The request system set-encrypon-key CLI Commands
CLI Command Descripon
request system set-encryption-key
Sets the encrypon key and enables default
conguraon le encrypon:
• AES encrypon for the Canada and U.S. version of
the operang system
• DES encrypon for the internaonal version of the
operang system
request system set-encryption-key algorithm des
Sets the encrypon key and species conguraon le
encrypon by DES.
request system set-encryption-key unique
Sets the encrypon key and enables default
conguraon le encrypon with a unique encrypon
key that includes the chassis serial number of the
device.
When you encrypt conguraon les with the unique
key, you can decrypt the les on the current device
only. You cannot copy encrypt conguraon les to
another device and decrypt them.
request system set-encryption-key des unique
Sets the encrypon key and species conguraon le
encrypon by DES with a unique encrypon key.
To encrypt conguraon les on a device:
1. Enter operaonal mode in the CLI.
2. Congure an encrypon key in EEPROM and determine the encrypon process; for example, enter
the request system set-encryption-key command.
user@host> request system set-encryption-key
Enter EEPROM stored encryption key:
256

3. At the prompt, enter the encrypon key. The encrypon key must have at least six characters.
Enter EEPROM stored encryption key:juniper1
Verifying EEPROM stored encryption key:
4. At the second prompt, reenter the encrypon key.
5. Enter conguraon mode in the CLI.
6. Enable conguraon le encrypon to take place.
[edit]
user@host# edit system
user@host# set encrypt-configuration-files
7. Begin the encrypon process by comming the conguraon.
[edit]
user@host# commit
commit complete
Decrypt Conguraon Files
Decrypng conguraon les means disabling the le encrypon on a device, which makes the les
readable to all.
To disable the encrypon of conguraon les on a device:
1. Enter operaonal mode in the CLI.
2. Verify your permission to decrypt conguraon les on this device by entering the encrypon key for
the device.
Example:
user@host> request system set-encryption-key
Enter EEPROM stored encryption key:
Verifying EEPROM stored encryption key:
3. At the second prompt, reenter the encrypon key.
4. Enter conguraon mode in the CLI.
257

5. Enable conguraon le decrypon.
[edit]
user@host# edit system
user@host# set no-encrypt-configuration-files
6. Begin the decrypon process by comming the conguraon.
[edit]
user@host# commit
commit complete
Modify the Encrypon Key
When you modify the encrypon key, the conguraon les are decrypted and then reencrypted with
the new encrypon key.
To modify the encrypon key:
1. Enter operaonal mode in the CLI.
2. Congure a new encrypon key in EEPROM, and determine the encrypon process; for example,
enter the request system set-encryption-key command.
user@host> request system set-encryption-key
Enter EEPROM stored encryption key:
3. At the prompt, enter the new encrypon key. The encrypon key must have at least six characters.
Enter EEPROM stored encryption key:juniperone
Verifying EEPROM stored encryption key:
4. At the second prompt, reenter the new encrypon key.
258

Example: Protecng the Junos OS Conguraon
from Modicaon or Deleon
IN THIS SECTION
Requirements | 259
Overview | 260
Protecng a Parent-Level Hierarchy | 260
Protecng a Child Hierarchy | 261
Protecng a Conguraon Statement Within a Hierarchy | 262
Protecng a List of Ideners for a Conguraon Statement | 263
Protecng an Individual Member from a Homogenous List | 264
Unprotecng a Conguraon | 265
Vericaon | 266
This example shows how to use the protect and unprotect commands in the conguraon mode to protect
and unprotect the CLI conguraon.
Requirements
This example uses the following hardware and soware components:
• An M Series, MX Series, PTX Series, or T Series device
• Junos OS 11.2 or later running on all devices
259

Overview
IN THIS SECTION
Topology | 260
The Junos OS enables you to protect the device conguraon from being modied or deleted by other
users. This can be accomplished by using the protect command in the conguraon mode of the CLI.
Likewise, you can also unprotect a protected conguraon by using the unprotect command.
These commands can be used at any level of the conguraon hierarchy—a top-level parent hierarchy or
a conguraon statement or an idener within the lowest level of the hierarchy.
If a conguraon hierarchy is protected, users cannot perform the following acvies:
• Deleng or modifying a hierarchy or a statement or idener within the protected hierarchy
• Inserng a new conguraon statement or an idener within the protected hierarchy
• Renaming a statement or idener within the protected hierarchy
• Copying a conguraon into a protected hierarchy
• Acvang or deacvang statements within a protected hierarchy
• Annotang a protected hierarchy
Topology
Protecng a Parent-Level Hierarchy
IN THIS SECTION
Procedure | 261
260

Procedure
Step-by-Step Procedure
To protect a conguraon at the top level of the hierarchy:
Idenfy the hierarchy that you want to protect and issue the protect command for the hierarchy at the
[edit] hierarchy level.
For example, if you want to protect the enre [edit access] hierarchy level, use the following command:
[edit]
user@host# protect access
Results
Protects all elements under the parent hierarchy.
NOTE: If you issue the protect command for a hierarchy that is not used in the conguraon, the
Junos OS CLI displays the following error message:
[edit]
user@host# protect access
warning: statement not found
Protecng a Child Hierarchy
IN THIS SECTION
Procedure | 262
261

Procedure
Step-by-Step Procedure
To protect a child hierarchy contained within a parent hierarchy:
Navigate to the parent container hierarchy. Use the protect command for the hierarchy at the parent
level.
For example, if you want to protect the [edit system syslog console] hierarchy level, use the following
command at the [edit system syslog] hierarchy level.
[edit system syslog]
user@host# protect console
Results
Protects all elements under the child hierarchy.
Protecng a Conguraon Statement Within a Hierarchy
IN THIS SECTION
Procedure | 262
Procedure
Step-by-Step Procedure
To protect a conguraon statement within a hierarchy level:
Navigate to the hierarchy level containing the statement that you want to protect and issue the protect
command for the hierarchy.
262

For example, if you want to protect the host-name statement under the [edit system] hierarchy level, use
the following command:
[edit system]
user@host# protect host-name
Results
Protecng a List of Ideners for a Conguraon Statement
IN THIS SECTION
Procedure | 263
Procedure
Step-by-Step Procedure
Some conguraon statements can take mulple values. For example, the address statement at the [edit
system login deny-sources] hierarchy level can take a list of hostnames, IPv4 addresses, or IPv6 addresses.
Suppose you have the following conguraon:
[edit system login]
deny-sources {
address [ 172.17.28.19 172.17.28.20 172.17.28.21 172.17.28.22];
}
To protect all the addresses for the address statement, use the following command at the [edit] level:
[edit]
user@host# protect system login deny-sources address
263

Results
All the addresses ([172.17.28.19 172.17.28.20 172.17.28.21 172.17.28.22]) for the address statement
are protected.
Protecng an Individual Member from a Homogenous List
IN THIS SECTION
Procedure | 264
Procedure
Step-by-Step Procedure
Suppose you have the following conguraon:
[edit groups ]
test1 {
system {
name-server {
10.1.2.1;
10.1.2.2;
10.1.2.3;
10.1.2.4;
}
}
}
To protect one or more individual addresses for the name-server statement, issue the following command
at the [edit] level:
[edit]
user@host# protect groups test1 system name-server 10.1.2.1
user@host# protect groups test1 system name-server 10.1.2.4
264

Results
Addresses 10.1.2.1 and 10.1.2.4 are protected.
Unprotecng a Conguraon
IN THIS SECTION
Procedure | 265
Procedure
Step-by-Step Procedure
Suppose you have the following conguraon at the [edit system] hierarchy level:
protect: system {
host-name bigping;
domain-search 10.1.2.1;
login {
deny-sources {
protect: address [ 172.17.28.19 172.17.28.173 172.17.28.0 174.0.0.0 ];
}
}
}
To unprotect the enre [edit system] hierarchy level, issue the following command at the [edit] level:
[edit]
user@host# unprotect system
Results
The enre system hierarchy level is unprotected.
265

Vericaon
IN THIS SECTION
Verify That a Hierarchy Is Protected Using the show Command | 266
Verify That a Hierarchy Is Protected by Aempng to Modify a Conguraon | 267
Verify Usage of the protect Command | 267
View the Conguraon in XML | 268
Verify That a Hierarchy Is Protected Using the show Command
Purpose
To check that a conguraon hierarchy is protected.
Acon
In the conguraon mode, issue the show command at the [edit] hierarchy level to see all the
conguraon hierarchies and conguraon statements that are protected.
NOTE: All protected hierarchies or statements are prexed with a protect: string.
...
protect: system {
host-name bigping;
domain-search 10.1.2.1;
login {
deny-sources {
protect: address [ 172.17.28.19 172.17.28.173 172.17.28.0 174.0.0.0 ];
}
}
}
...
266

Verify That a Hierarchy Is Protected by Aempng to Modify a Conguraon
Purpose
To verify that a conguraon is protected by trying to modify the conguraon using the activate, copy,
insert, rename, and delete commands.
Acon
To verify that a conguraon is protected:
1. Try using the activate, copy, insert, rename, and delete commands for a top-level hierarchy or a child-level
hierarchy or a statement within the hierarchy.
For a protected hierarchy or statement, the Junos OS displays an appropriate warning that the
command has not executed. For example:
protect: system {
host-name a;
inactive: domain-search [ a b ];
}
2. To verify that the hierarchy is protected, try issuing the activate command for the domain-search
statement:
[edit system]
user@host# activate system domain-search
The Junos OS CLI displays an appropriate message:
warning: [system] is protected, 'system domain-search' cannot be activated
Verify Usage of the protect Command
Purpose
To view the protect commands used for protecng a conguraon.
267

Acon
1. Navigate to the required hierarchy.
2. Issue the show | display set relative command.
user@host> show | display set relative
set system host-name bigping
set system domain-search 10.1.2.1
set system login deny-sources address 172.17.28.19
set system login deny-sources address 172.17.28.173
set system login deny-sources address 172.17.28.0
set system login deny-sources address 174.0.0.0
protect system login deny-sources address
protect system
View the Conguraon in XML
Purpose
To check if the protected hierarchies or statements are also displayed in the XML. Protected hierarchies,
statements, or ideners are displayed with the | display xml aribute in the XML.
Acon
To view the conguraon in XML:
1. Navigate to the hierarchy you want to view.
2. Use the show command with the pipe symbol and opon | display xml:
[edit system]
user@host# show | display xml
[edit]
user@host# show system | display xml
<rpc-reply xmlns:junos="http://xml.juniper.net/junos/11.2I0/junos">
<configuration junos:changed-seconds="1291279234" junos:changed-localtime="2017-12-02
00:40:34 PST">
<system protect="protect">
<host-name>bigping</host-name>
268

<domain-search>10.1.2.1</domain-search>
<login>
<message>
\jnpr
\tUNAUTHORIZED USE OF THIS ROUTER
\tIS STRICTLY PROHIBITED!
</message>
<class>
<name>a</name>
<allow-commands>commit-synchronize</allow-commands>
<deny-commands>commit</deny-commands>
</class>
<deny-sources>
<address protect="protect">172.17.28.19</address>
<address protect="protect">172.17.28.173</address>
<address protect="protect">172.17.28.0</address>
<address protect="protect">174.0.0.0</address>
</deny-sources>
</login>
<syslog>
<archive>
</archive>
</syslog>
</system>
</configuration>
<cli>
<banner>[edit]</banner>
</cli>
</rpc-reply>
NOTE: Loading an XML conguraon with the unprotect="unprotect" tag unprotects an already
protected hierarchy. For example, suppose you load the following XML hierarchy:
<protocols unprotect="unprotect">
<ospf>
269

<area>
<name>0.0.0.0</name>
<interface>
<name>all</name>
</interface>
</area>
</ospf>
</protocols>
The [edit protocols] hierarchy becomes unprotected if it is already protected.
Synchronizing Conguraons Across Roung
Engines
IN THIS SECTION
Roung Engine Synchronizaon Overview | 270
Congure Mulple Roung Engines to Synchronize Commied Conguraons Automacally | 274
On devices with redundant Roung Engines, you can perform a commit synchronize, which acvates and
synchronizes the conguraon on both Roung Engines.
Roung Engine Synchronizaon Overview
If your device has two Roung Engines, you can manually direct one Roung Engine to synchronize its
conguraon with the other by issuing the commit synchronize command. The Roung Engine on which
you execute this command (the requesng Roung Engine) rst commits the conguraon. The
requesng Roung Engine then copies and loads its candidate conguraon to the responding Roung
Engine. Each Roung Engine performs a syntax check on the candidate conguraon le before
comming it. The commit synchronizaon process takes place one Roung Engine at a me.
270

If no errors are found, the conguraon is acvated and becomes the current operaonal conguraon
on both Roung Engines.
NOTE: If the commit fails on either Roung Engine, the commit process is rolled back on the
other Roung Engine as well. This safeguard ensures that both Roung Engines have the same
conguraon.
NOTE: If your conguraon includes a large amount of text or many apply-groups, commit mes
can be longer than desired.
For example, you may want both Roung Engines to have the same conguraon. In this scenario, if you
are logged in to re1 (requesng Roung Engine), you issue the commit synchronize command on re1.
Roung Engine re1 copies and loads its candidate conguraon to re0 (responding Roung Engine). Both
Roung Engines then perform a syntax check on the candidate conguraon le being commied. If no
errors are found, the re1 candidate conguraon is acvated and becomes the current operaonal
conguraon on both Roung Engines.
NOTE: When you issue the commit synchronize command, you must use the groups re0 and re1. For
informaon about how to use the apply-groups statement, see "Applying a Conguraon Group"
on page 131.
You can synchronize a Roung Engine's current operaonal conguraon le with the other Roung
Engine's conguraon le. To do this, you log in to the Roung Engine from which you want to
synchronize and issue the commit synchronize command.
Example:
[edit]
user@host# commit synchronize
re0:
configuration check succeeds
re1:
commit complete
re0:
commit complete
271

NOTE: The backup Roung Engine may be only parally commied due to invalid conguraon
during system reboot. In this case, the commit synchronize command with the force opon from the
primary Roung Engine does not work.
The commit synchronize command does not work if the responding Roung Engine has uncommied
conguraon changes. However, you can force commit synchronizaon on the Roung Engines by using
the force opon. When you issue the commit synchronize command with the force opon from one Roung
Engine, the conguraon sessions on the other Roung Engine are terminated. When those sessions are
terminated on the other Roung Engine, its conguraon is synchronized with the conguraon on the
Roung Engine from which you issued the command.
NOTE: We recommend that you use the force opon only if you are unable to resolve the issues
that caused the commit synchronize command to fail.
To force a commit synchronize on the Roung Engines, you log in to the Roung Engine from which you
want to synchronize. Then, you issue the command with the force opon.
Example:
[edit]
user@host# commit synchronize force
re0:
re1:
commit complete
re0:
commit complete
[edit]
user@host#
NOTE: If you have nonstop roung enabled on your device, you enter the commit synchronize
command from the primary Roung Engine aer you make any changes to the conguraon. If
you enter this command on the backup Roung Engine, the soware displays a warning and
commits the conguraon.
272

Include the fast-synchronize statement at the [edit system] hierarchy level to have the synchronizaon
occur simultaneously between the primary and the backup Roung Engines:
[edit system]
commit fast-synchronize;
NOTE:
• When the fast-synchronize statement is congured, the commits on the primary Roung Engine
and the backup Roung Engine run in parallel. In this process, the conguraon is validated
only on the Roung Engine where you execute the commit command. Therefore, we
recommend that you not include too many conguraon details in groups like re0 and re1,
because the conguraon specied in group re0 is applied only if the current Roung Engine
is in slot 0. Likewise, the conguraon specied in group re1 is applied only if the current
Roung Engine is in slot 1.
• If fast-synchronize is enabled and both Roung Engines (primary and backup) run dierent
soware versions, the backup Roung Engine conguraon may not be valid. This is true
even if the primary Roung Engine validates the conguraon. Therefore, ensure that the
same operang systemoperang system soware version is running on both the Roung
Engines.
You can use the commit synchronize scripts command to synchronize a Roung Engine's conguraon and
all commit, event, lib, op, and SNMP scripts with the other Roung Engine. If you congure the load-
scripts-from-flash statement for the requesng Roung Engine, the device synchronizes the scripts. The
device synchronizes the scripts from ash memory on the requesng Roung Engine to ash memory
on the responding Roung Engine. Otherwise, the device synchronizes the scripts from the hard disk on
the requesng Roung Engine to the hard disk on the responding Roung Engine. The device
synchronizes all scripts regardless of whether they are enabled in the conguraon or have been
updated since the last synchronizaon.
To synchronize a Roung Engine's conguraon le and all scripts with the other Roung Engine, log in
to the Roung Engine from which you want to synchronize, and issue the commit synchronize scripts
command.
Example:
[edit]
user@host# commit synchronize scripts
re0:
configuration check succeeds
273

re1:
commit complete
re0:
commit complete
NOTE: If the commit check operaon fails for the requesng Roung Engine, the process stops,
and the scripts are not copied to the responding Roung Engine. If the commit check or commit
operaon fails for the responding Roung Engine, the scripts are sll synchronized. The scripts
are sll synchronized because the synchronizaon occurs before the commit check operaon on
the responding Roung Engine.
Include the synchronize statement at the [edit system scripts] hierarchy level to synchronize scripts every
me you issue a commit synchronize command.
[edit system scripts]
synchronize;
Congure Mulple Roung Engines to Synchronize Commied
Conguraons Automacally
If your device has mulple Roung Engines, you can manually direct one Roung Engine to synchronize
its conguraon with the others by issuing the commit synchronize command.
To make the Roung Engines synchronize automacally whenever a conguraon is commied, include
the commit synchronize statement at the [edit system] hierarchy level:
[edit system]
commit synchronize;
The Roung Engine on which you execute the commit command (requesng Roung Engine) copies and
loads its candidate conguraon to the other (responding) Roung Engines. All Roung Engines then
perform a syntax check on the candidate conguraon le being commied. If no errors are found, the
conguraon is acvated and becomes the current operaonal conguraon on all Roung Engines.
For the commit synchronizaon process, the primary Roung Engine commits the conguraon and
sends a copy of the conguraon to the backup Roung Engine. Then the backup Roung Engine loads
and commits the conguraon. So, the commit synchronizaon between the primary and backup
274

Roung Engines takes place one Roung Engine at a me. If the conguraon has a large text size or
many apply-groups, commit mes can be longer than desired.
You can use the commit fast-synchronize statement to have the synchronizaon between the primary and
backup Roung Engines occur simultaneously instead of sequenally. This can reduce the me needed
for synchronizaon because the commits on the primary and backup Roung Engines occur in parallel.
Include the fast-synchronize statement at the [edit system] hierarchy level to have synchronize occur
simultaneously between the primary and the backup Roung Engines:
[edit system]
commit fast-synchronize
NOTE:
• If commit fails on either Roung Engine, the commit process is rolled back on the other
Roung Engine as well. This ensures that both Roung Engines have the same conguraon.
• When the fast-synchronize statement is congured, the commits on the primary Roung Engine
and the backup Roung Engine run in parallel. In this process, the conguraon is validated
only on the Roung Engine where you execute the commit command. Therefore, we
recommend liming the number of conguraon details in groups like re0 and re1, because
the conguraon specied in group re0 is applied only if the current Roung Engine is in slot
0. Likewise, the conguraon specied in group re1 is applied only if the current Roung
Engine is in slot 1.
• If fast-synchronize is enabled and if the primary Roung Engine and backup Roung Engines
run dierent soware versions, you cannot be sure that the backup Roung Engine
conguraon is valid. This is true even if the primary Roung Engine validates the
conguraon, Therefore, ensure that the operang system soware version running on both
the Roung Engines is the same.
Change History Table
Feature support is determined by the plaorm and release you are using. Use Feature Explorer to
determine if a feature is supported on your plaorm.
Release
Descripon
19.4R1-S1
Starng in Junos OS Evolved Release 19.4R1-S1, commit synchronize is enabled by default on
PTX10008. If you issue commit at the [edit system] hierarchy level from the primary roung engine,
you see that the backup roung engine is automacally synchronized.
275

19.4R1
Starng in Junos OS Evolved Release 19.4R1, commit synchronize is enabled by default on PTX10008.
If you issue commit at the [edit system] hierarchy level from the primary roung engine, you see that
the backup roung engine is automacally synchronized.
276

CLI Operaonal Mode Overview
IN THIS SECTION
CLI Operaonal Mode Command Overview | 278
Display Opons of the show Command—An Overview | 281
Interface Naming Convenons Used in Operaonal Commands | 282
About Group Interface Names Using Wildcard Characters | 284
In operaonal mode, you can use Junos OS CLI commands to monitor and troubleshoot a device. The
monitor, ping, show, test, and traceroute commands enable you to display informaon and test network
connecvity for the device.
CLI Operaonal Mode Command Overview
IN THIS SECTION
CLI Operaonal Mode Command Categories | 278
Commonly Used Operaonal Mode Commands | 279
You (the network administrator) can control all network operaons using the Junos OS CLI operaonal
mode commands described in this topic.
CLI Operaonal Mode Command Categories
CLI operaonal mode commands fall into the following broad categories:
• Operaonal mode commands for monitoring and troubleshoong—The following commands perform
funcons related to informaon and stascs about the soware and to test network connecvity.
• clear—Clear stascs and protocol database informaon.
278

• file—Perform le operaons.
• mtrace—Trace a mulcast path from source to receiver.
• monitor—Perform real-me debugging of various soware components, including the roung
protocols and interfaces.
• ping—Determine the reachability of a remote network host.
• show—Display the current conguraon and informaon about interfaces, roung protocols,
roung tables, roung policy lters, system alarms, and the chassis.
• test—Test the conguraon and applicaon of policy lters and autonomous system (AS) path
regular expressions.
• traceroute—Trace the route to a remote network host.
• Commands for restarng soware processes—The commands in the restart hierarchy restart the
various system processes, including the roung protocol, interface, and SNMP.
• A command—request—Perform system-level operaons, including stopping and reboong the router
or switch and loading operang system images.
• A command—start—Exit the CLI and start a UNIX shell.
• A command—configure—Enter conguraon mode, which provides a series of commands that
congure the system, including the roung protocols, interfaces, network management, and user
access.
For more informaon about the CLI operaonal mode commands, see the CLI Explorer. Alternavely,
you can enter ? at the operaonal mode command prompt to view a list of available commands.
Commonly Used Operaonal Mode Commands
The following table lists some operaonal commands you may nd useful for monitoring router or
switch operaon.
Table 12: Commonly Used
Operaonal Mode Commands
Items to Check Descripon Command
Soware version Versions of soware running on the router or switch
show version
Log les Contents of the log les
monitor
279

Table 12: Commonly Used Operaonal Mode Commands
(Connued)
Items to Check Descripon Command
Log les and their contents and recent user logins
show log
Remote systems Host reachability and network connecvity
ping
The route to a network system
traceroute
Conguraon Current system conguraon
show configuration
File manipulaon List of les and directories on the router or switch
file list
Contents of a le
file show
Interface informaon Detailed informaon about interfaces
show interfaces
Chassis Chassis alarm status
show chassis alarms
Informaon currently on cra display
show chassis craft-interface
Router or switch environment informaon
show chassis environment
Hardware inventory
show chassis hardware
Roung table
informaon
Informaon about entries in the roung tables
show route
Forwarding table
informaon
Informaon about data in the kernel’s forwarding table
show route forwarding-table
280

Display Opons of the show Command—An Overview
—
The show command can include brief, detail, extensive, or terse opons. You can use these and other
opons to control the amount and type of informaon to view.
1. At any point in the CLI, you can enter the ? character to view all the currently available opons. For
example:
user@host> show interfaces fe-1/1/1 ?
Possible completions:
<[Enter]> Execute this command
brief Display brief output
descriptions Display interface description strings
detail Display detailed output
extensive Display extensive output
media Display media information
snmp-index SNMP index of interface
statistics Display statistics and detailed output
terse Display terse output
| Pipe through a command
2. At any point in the CLI, you can use the show command with one of the following opons to display
the detail you need to view.
281

Figure 10: Command Output Opons
Interface Naming Convenons Used in Operaonal Commands
IN THIS SECTION
Physical Part of an Interface Name | 282
Logical Part of an Interface Name | 283
Channel Idener Part of an Interface Name | 283
This topic explains the interface naming convenons used in operaonal commands.
Physical Part of an Interface Name
The physical interface naming convenons for Juniper Networks device plaorms is as follows:
282

• On SRX Series Firewalls, the unique name of each network interface has the following format to
idenfy the physical device that corresponds to a single physical network connector:
type-slot
/
pim-or-ioc
/
port
• On other plaorms, when you display informaon about an interface, you specify the following
ideners: interface type, the slot in which the Flexible PIC Concentrator (FPC) is installed, the slot
on the FPC in which the PIC is located, and the congured port number.
In the physical part of the interface name, a hyphen (-) separates the media type from the FPC
number, and a slash (/) separates the FPC, PIC, and port numbers:
type-fpc
/
pic
/
port
NOTE: Excepons to the
type-fpc
/
pic
/
port
physical descripon include the aggregated Ethernet
and aggregated SONET/SDH interfaces, which use the syntax ae
number
and as
number
, respecvely.
Logical Part of an Interface Name
The logical unit part of the interface name corresponds to the logical unit number, which can be a
number from 0 through 16,384. You use logical unit numbers to uniquely idenfy physical storage
systems or virtual storage systems within a network. In the virtual part of the name, a period (.)
separates the port and logical unit numbers:
• SRX Series Firewalls:
type-slot/pim-or-ioc/port:channel.unit
• Other plaorms:
type-fpc
/
pic
/
port.logical
Channel Idener Part of an Interface Name
The channel idener part of an interface name is required only on channelized interfaces. For
channelized interfaces, channel 0 idenes the rst channelized interface. For channelized intelligent
queuing (IQ) interfaces, channel 1 idenes the rst channelized interface.
283

NOTE: Depending on the type of channelized interface, you can specify up to three levels of
channelizaon.
A colon (:) separates the physical and virtual parts of the interface name:
• SRX Series Firewalls:
type-slot
/
pim-or-ioc
/
port:channel
type-slot
/
pim-or-ioc
/
port:channel:channel
type-slot
/
pim-or-ioc
/
port:channel:channel:channel
• Other plaorms:
type-fpc
/
pic
/
port:channel
type-fpc/
/
pic
/
port:channel:channel
type-fpc
/
pic
/
port:channel:channel:channel
About Group Interface Names Using Wildcard Characters
You can use wildcard characters in operaonal commands to specify groups of interface names without
having to type each name individually. The following table lists the available wildcard characters. You
must enclose all wildcard characters except the asterisk (*) in quotaon marks (“ ”).
Table 13: Wildcard Characters for Specifying Interface Names
Wildcard Character Descripon
* (asterisk)
Match any string of characters in that posion in the interface name. For example,
so* matches all SONET/SDH interfaces.
"[
character
<
character
...>]"
Match one or more individual characters in that posion in the interface name.
For example, so-“[03]”* matches all SONET/SDH interfaces in slots 0 and 3.
284

Table 13: Wildcard Characters for Specifying Interface Names
(Connued)
Wildcard Character Descripon
"[!
character
<
character
...>]" Match all characters except those included in the brackets. For example, so-“[!
03]”* matches all SONET/SDH interfaces except those in slots 0 and 3.
"[
character1
-
character2
]" Match a range of characters. For example, so-“[0-3]” * matches all SONET/SDH
interfaces in slots 0, 1, 2, and 3.
"[!
character1
-
character2
]"
Match all characters that are not in the specied range of characters. For example,
so-”[!0-3]”* matches all SONET/SDH interfaces in slots 4, 5, 6, and 7.
Using Operaonal Commands to Monitor a Device
IN THIS SECTION
CLI Command Compleon Example | 286
Operaonal Mode Commands: Overview of Controlling the Scope | 287
Viewing Files and Directories on a Device | 289
Display Operang System Informaon | 295
Managing Programs and Processes Using Operaonal Mode Commands | 295
CLI Comment Character # for Operaonal Mode Commands | 300
Operaonal mode CLI commands enable you to monitor and control the operaon of a Juniper
Networks device. The operaonal mode commands exist in a hierarchical structure.
285

CLI Command Compleon Example
The command compleon feature can help make it easier both to enter commands or to learn what
possible compleon opons are available at any given me.
This example shows the result of issuing the show interfaces command. In this case, the spacebar is used
to autocomplete the command.
user@host> sh<Space>ow i<Space>
'i' is ambiguous.
Possible completions:
igmp Show information about IGMP
interface Show interface information
isis Show information about IS-IS
user@host> show in<Space>terfaces
Physical interface: at-0/1/0, Enabled, Physical link is Up
Interface index: 11, SNMP ifIndex: 65
Link-level type: ATM-PVC, MTU: 4482, Clocking: Internal, SONET mode
Speed: OC12, Loopback: None, Payload scrambler: Enabled
Device flags: Present Running
Link flags: 0x01
...
user@host>
This example shows how to display a list of all log les whose names start with the string “messages,”
and then display the contents of one of the les. Here, the Tab key is used to perform the
autocompleon.
user@myhost> show log mes?
Possible completions:
<filename>Log file to display
messagesSize: 1417052, Last changed: Mar 3 00:33
messages.0.gzSize: 145575, Last changed: Mar 3 00:00
messages.1.gzSize: 134253, Last changed: Mar 2 23:00
messages.10.gzSize: 137022, Last changed: Mar 2 14:00
messages.2.grSize: 137112, Last changed: Mar 2 22:00
messages.3.gzSize: 121633, Last changed: Mar 2 21:00
messages.4.gzSize: 135715, Last changed: Mar 2 20:00
messages.5.gzSize: 137504, Last changed: Mar 2 19:00
messages.6.gzSize: 134591, Last changed: Mar 2 18:00
286

messages.7.gzSize: 132670, Last changed: Mar 2 17:00
messages.8.gzSize: 136596, Last changed: Mar 2 16:00
messages.9.gzSize: 136210, Last changed: Mar 2 15:00
user@myhost> show log mes
<Tab>
sages.4
<Tab>
.gz
<Enter>
Jan 15 21:00:00 myhost newsyslog[1381]: logfile turned over
...
Operaonal Mode Commands: Overview of Controlling the Scope
IN THIS SECTION
Roung Matrix Command Opons | 288
The Junos OS CLI operaonal commands include opons that you can use to idenfy specic
components on a device. For example:
• You use the show interfaces command to display informaon about all interfaces on the router.
1. Type the show interfaces command to display informaon about all interfaces on the router.
user@host> show interfaces
Physical interface: so-0/0/0, Enabled, Physical link is Up
Interface index: 128, SNMP ifIndex: 23
Link-level type: PPP, MTU: 4474, Clocking: Internal, SONET mode, Speed: OC3,
Loopback: None, FCS: 16, Payload scrambler: Enabled
Device flags : Present Running
Interface flags: Point-To-Point SNMP-Traps Internal: 0x4000
Link flags : Keepalives
Keepalive settings: Interval 10 seconds, Up-count 1, Down-count 3
Keepalive: Input: 13861 (00:00:05 ago), Output: 13891 (00:00:01 ago)
LCP state: Opened
NCP state: inet: Opened, inet6: Not-configured, iso: Opened, mpls: Not-configured
CHAP state: Closed
PAP state: Closed
CoS queues : 4 supported, 4 maximum usable queues
Last flapped : 2008-06-02 17:16:14 PDT (1d 14:21 ago)
287

Input rate : 40 bps (0 pps)
Output rate : 48 bps (0 pps)
---(more)---
NOTE: This example output shows only one interface, for the sake of brevity, but in reality,
the interfaces informaon for all four would be shown aer the —(more)— prompts.
2. To display informaon about a specic interface, type that interface as a command opon:
user@host> show interfaces fe-0/1/3
Physical interface: fe-0/1/3, Enabled, Physical link is Up
Interface index: 135, SNMP ifIndex: 30
Link-level type: Ethernet, MTU: 1514, Speed: 100mbps, MAC-REWRITE Error: None,
Loopback: Disabled, Source filtering: Disabled, Flow control: Enabled
Device flags : Present Running
Interface flags: SNMP-Traps Internal: 0x4000
Link flags : None
CoS queues : 4 supported, 4 maximum usable queues
Current address: 00:05:85:8f:c8:22, Hardware address: 00:05:85:8f:c8:22
Last flapped : 2008-06-02 17:16:15 PDT (1d 14:28 ago)
Input rate : 0 bps (0 pps)
Output rate : 0 bps (0 pps)
Active alarms : None
Active defects : None
user@host>
Roung Matrix Command Opons
The show version command oers several opons for viewing informaon about the roung matrix.
user@host> show version ?
Possible completions:
<[Enter]> Execute this command
all-lcc Show software version on all LCC chassis
brief Display brief output
detail Display detailed output
288

lcc Show software version on specific LCC (0..3)
scc Show software version on the SCC
| Pipe through a command
Viewing Files and Directories on a Device
IN THIS SECTION
Directories on the Device | 289
List Files and Directories | 290
Filenames and URLs | 293
The operang system stores informaon in les on the device, including conguraon les, log les, and
device soware les. This topic shows some examples of operaonal commands that you can use to
view les and directories on a device.
Directories on the Device
The following table lists some standard directories on a Juniper Networks device.
Table 14: Directories on the Device
DIrectory Descripon
/config
This directory is located on the device’s internal ash drive. It contains the acve conguraon
(juniper.conf) and rollback les 1, 2, and 3.
/var/db/config
This directory is located on the device’s hard drive and contains rollback les 4 through 49.
/var/tmp
This directory is located on the device’s hard drive. It holds core les from the various processes
on the Roung Engines. Core les are generated when a parcular process crashes. Juniper
Networks engineers use these core les to diagnose the cause of the failure.
289

Table 14: Directories on the Device
(Connued)
DIrectory Descripon
/var/log
This directory is located on the device’s hard drive. It contains les generated by both the
device’s logging funcon and the traceoptions command.
/var/home
This directory is located on the device’s hard drive. It contains a subdirectory for each congured
user on the device. These individual user directories are the default le locaon for many
soware commands.
/altroot
This directory is located on the device’s hard drive and contains a copy of the root le structure
from the internal ash drive. This directory is used in certain disaster recovery modes where the
internal ash drive is not operaonal.
/altconfig This directory is located on the device’s hard drive and contains a copy of the /config le
structure from the internal ash drive. This directory is also used in certain disaster recovery
modes when the internal ash drive is not operaonal.
List Files and Directories
You can view the device’s directory structure as well as individual les by issuing the file command in
operaonal mode.
1. To get help about the file command, enter file ?:
user@host> file ?
Possible
completions:
<[Enter]> Execute this command
archive Archives files from the system
change-owner Change owner of file
change-permission Change permission of file
checksum Calculate file checksum
compress Compress file
copy Copy files (local or remote)
delete Delete files from the system
delete-directory Delete a directory
link Create link between files
290

list List file information
make-directory Create a new
make-directory Create a new
user@host> file
Help shows that the file command includes several opons for manipulang les.
2. Use the list opon to see the directory structure of the device. For example, to show the les
located in your home directory on the device:
user@host> file list
.ssh/
common
The default directory for the file list command is the home directory of the user logged in to the
device. In fact, the user’s home directory is the default directory for most of the commands requiring
a lename.
3. To view the contents of other le directories, specify the directory locaon. For example:
user@host> file list /config
juniper.conf
juniper.conf.1.gz
juniper.conf.2.gz
juniper.conf.3.gz
4. You can also use the device’s context-sensive help system to locate a directory. For example:
user@host> file list /?
Possible completions:
<[Enter]> Execute this command
<path> Path to list
/COPYRIGHT Size: 6355, Last changed: Feb 13 2017
/altconfig/ Last changed: Aug 07 2017
/altroot/ Last changed: Aug 07 2017
/bin/ Last changed: Apr 09 22:31:35
/boot/ Last changed: Apr 09 23:28:39
/config/ Last changed: Apr 16 22:35:35
/data/ Last changed: Aug 07 2017
/dev/ Last changed: Apr 09 22:36:21
/etc/ Last changed: Apr 11 03:14:22
291

/kernel Size: 27823246, Last changed: Aug 07 2017
/mfs/ Last changed: Apr 09 22:36:49
/mnt/ Last changed: Jan 11 2017
/modules/ Last changed: Apr 09 22:33:54
/opt/ Last changed: Apr 09 22:31:00
/packages/ Last changed: Apr 09 22:34:38
/proc/ Last changed: May 07 20:25:46
/rdm.taf Size: 498, Last changed: Apr 09 22:37:31
/root/ Last changed: Apr 10 02:19:45
/sbin/ Last changed: Apr 09 22:33:55
/staging/ Last changed: Apr 09 23:28:41
/tmp/ Last changed: Apr 11 03:14:49
/usr/ Last changed: Apr 09 22:31:34
/var/ Last changed: Apr 09 22:37:30
user@host> file list /var/?
<[Enter]> Execute this command
<path> Path to list
/var/account/ Last changed: Jul 09 2017
/var/at/ Last changed: Jul 09 2017
/var/backups/ Last changed: Jul 09 2017
/var/bin/ Last changed: Jul 09 2017
/var/crash/ Last changed: Apr 09 22:31:08
/var/cron/ Last changed: Jul 09 2017
/var/db/ Last changed: May 07 20:28:40
/var/empty/ Last changed: Jul 09 2017
/var/etc/ Last changed: Apr 16 22:35:36
/var/heimdal/ Last changed: Jul 10 2017
/var/home/ Last changed: Apr 09 22:59:18
/var/jail/ Last changed: Oct 31 2017
/var/log/ Last changed: Apr 17 02:00:10
/var/mail/ Last changed: Jul 09 2017
/var/msgs/ Last changed: Jul 09 2017
/var/named/ Last changed: Jul 10 2017
/var/packages/ Last changed: Jan 18 02:38:59
/var/pdb/ Last changed: Oct 31 2017
/var/preserve/ Last changed: Jul 09 2017
/var/run/ Last changed: Apr 17 02:00:01
/var/rundb/ Last changed: Apr 17 00:46:00
/var/rwho/ Last changed: Jul 09 2017
/var/sdb/ Last changed: Apr 09 22:37:31
/var/spool/ Last changed: Jul 09 2017
/var/sw/ Last changed: Jul 09 2017
/var/tmp/ Last changed: Apr 09 23:28:41
292

/var/transfer/ Last changed: Jul 09 2017
/var/yp/ Last changed: Jul 09 2017
user@host> file list /var/
5. You can also display the contents of a le. For example:
user@host>file show /var/log/inventory
Jul 9 23:17:46 CHASSISD release 8.4I0 built by builder on 2017-06-12 07:58:27 UTC
Jul 9 23:18:05 CHASSISD release 8.4I0 built by builder on 2017-06-12 07:58:27 UTC
Jul 9 23:18:06 Routing Engine 0 - part number 740-003239, serial number 9000016755
Jul 9 23:18:15 Routing Engine 1 - part number 740-003239, serial number 9001018324
Jul 9 23:19:03 SSB 0 - part number 710-001951, serial number AZ8025
Jul 9 23:19:03 SSRAM bank 0 - part number 710-001385, serial number 243071
Jul 9 23:19:03 SSRAM bank 1 - part number 710-001385, serial number 410608
...
Filenames and URLs
You can include a lename in CLI commands and conguraon statements such as these:
• file copy
• file archive,
• load,
• save
• set system login user
•
username
• authentication
•
load-key-file
• request system software add
On a roung matrix, you can include chassis informaon as part of the lename (for example, lcc0, lcc0-
re0, or lcc0-re1).
You can specify a lename or URL in one of the following ways:
•
filename
—File in the user’s current directory on the local ash drive. You can use wildcards to specify
mulple source les or a single desnaon le. Neither HTTP nor FTP supports wildcards.
293

NOTE: Only the file (compare | copy | delete | list | rename | show) commands support
wildcards. When you issue the file show command with a wildcard, the command must
resolve to one lename.
•
path
/
filename
—File on the local ash disk.
• /var/
filename
or /var/
path
/
filename
—File on the local hard disk.
You can also specify a le on a local Roung Engine for a specic T640 router on a roung matrix:
user@host> file delete lcc0-re0:/var/tmp/junk
• a:
filename
or a:
path
/
filename
—File on the local drive. The default path is / (the root-level directory). The
removable media can be in MS-DOS or UNIX (UFS) format.
•
hostname:
/
path
/
filename, hostname:filename, hostname:path
/
filename,
or scp://
hostname
/
path
/
filename
—File on
an scp/ssh client. This form is not available in the worldwide version of the operang system. The
default path is the user’s home directory on the remote system. You can also specify
hostname
as
username
@
hostname
.
• ftp://
hostname
/
path
/
filename
—File on an FTP server. You can also specify
hostname
as
username
@
hostname
or
username
:
password
@
hostname
. The default path is the user’s home directory.
To specify an absolute path, the path must start with %2F; for example, ftp://
hostname
/%2F
path
/
filename
.
To have the system prompt you for the password, specify prompt in place of the password. If a
password is required, and you do not specify the password or prompt, an error message is displayed:
user@host> file copy ftp://[email protected]//filename
file copy ftp.hostname.net: Not logged in.
user@host> file copy ftp://username:[email protected]//filename
Password for [email protected]:
• http://
hostname
/
path
/
filename
—File on an HTTP server. You can also specify
hostname
as
username
@
hostname
or
username
:
password
@
hostname
. If a password is required and you omit it, you are prompted for it.
• re0:/
path
/
filename
or re1:/
path
/
filename
—File on a local Roung Engine.
294
You can also specify a le on a local Roung Engine for a specic T640 router on a roung matrix:
user@host> show log lcc0-re1:chassisd
Display Operang System Informaon
You can display Junos OS version informaon and other status to determine if the version of the
soware that you are running supports specic features or hardware.
To display this informaon:
1. Make sure you are in operaonal mode.
2. To display brief informaon and status for the kernel and Packet Forwarding Engine, enter the show
version brief command. This command shows version informaon for soware packages installed on
the router.
If the Junos Crypto Soware Suite is listed, the router has Canada and USA encrypted soware. If
the Junos Crypto Soware Suite is not listed, the router is running worldwide nonencrypted
soware.
3. To display detailed version informaon, enter the show version detail command. This command
displays the hostname and version informaon for soware packages installed on your router. It also
includes the version informaon for each soware process.
Managing Programs and Processes Using Operaonal Mode Commands
IN THIS SECTION
Show Soware Processes | 296
Restart the Soware Process | 297
Stop the Soware | 298
Reboot the Soware | 299
This topic shows some examples of Junos OS operaonal commands that you can use to manage
programs and processes on a Juniper Networks device.
295

Show Soware Processes
To verify system operaon or to begin diagnosing an error condion, you may need to display
informaon about soware processes running on the device.
To show soware processes:
1. Make sure you are in operaonal mode.
2. Enter the show system processes extensive command. This command shows the CPU ulizaon on the
device and lists the processes in order of CPU ulizaon.
The following table lists and describes the output elds included in this example. The elds are listed in
alphabecal order.
Table 15: The show system process extensive Command Output Fields
Field Descripon
COMMAND
Command that is running.
last pid
Last process idener assigned to the process.
load averages
Three load averages, followed by the current me.
Mem
Informaon about physical and virtual memory allocaon.
NICE
UNIX “nice” value. The nice value allows a process to change its nal scheduling priority.
PID
Process idener.
PRI
Current kernel scheduling priority of the process. A lower number indicates a higher priority.
processes Number of exisng processes and the number of processes in each state (sleeping, running,
starting, zombies, and stopped).
RES
Current amount of resident memory, in KB.
296
Table 15: The show system process extensive Command Output Fields
(Connued)
Field Descripon
SIZE Total size of the process (text, data, and stack), in KB.
STATE Current state of the process (sleep, wait, run, idle, zombi, or stop).
Swap
Informaon about physical and virtual memory allocaon.
USERNAME
Owner of the process.
WCPU
Weighted CPU usage.
Restart the Soware Process
To correct an error condion, you might need to restart a soware process running on the device. You
can use the restart command to force a restart of a soware process.
CAUTION: Do not restart a soware process unless specically asked to do so by your
Juniper Networks customer support representave. Restarng a soware process
during normal operaon of a device can interrupt packet forwarding and cause data
loss.
To restart a soware process:
1. Make sure you are in operaonal mode.
2. Enter the following command:
user@host> restart
process-name
< (immediately | gracefully | soft) >
•
process-name
is the name of the process that you want to restart. For example, routing or class-of-
service. You can use the command compleon feature of the system to see a list of soware
processes that you can restart using this command.
• The opon gracefully restarts the soware process aer performing clean-up tasks.
•
The opon immediately restarts the soware process without performing any clean-up tasks.
297

• The opon soft rereads and reacvates the conguraon without completely restarng the
soware processes. For example, BGP peers stay up and the roung table stays constant.
NOTE: The gracefully, immediately, and soft opons for the restart command are oponal and not
required for execung the command.
The following example shows how to restart the roung process:
user@host> restart routing
Routing protocol daemon started, pid 751
When a process restarts, the process idener (PID) is updated.
Figure 11: Restarng a Process
Stop the Soware
CAUTION: To avoid possible damage to the le system and to prevent data loss, you
must always shut down the soware gracefully before powering o the device.
You must stop the soware on a device through a direct console connecon, not through the network.
As the soware shuts down, the network will go down, and if you were connected that way, you will not
see the results output.
To stop the soware:
298

1. Make sure you are in operaonal mode.
2. Enter the request system halt command. This command stops all system processes and halts the
operang system. For example:
user@host> request system halt
Halt the system? [yes,no] (no) yes
shutdown: [pid 3110]
Shutdown NOW!
*** FINAL System shutdown message from root@host ***
System going down IMMEDIATELY
user@host> Dec 17 17:28:40 init: syslogd (PID 2514) exited with status=0 Normal Exit
Waiting (max 60 seconds) for system process `bufdaemon' to stop...stopped
Waiting (max 60 seconds) for system process `syncer' to stop...stopped
syncing disks... 4
done
Uptime: 3h31m41s
ata0: resetting devices.. done
The operating system has halted.
Please press any key to reboot.
Reboot the Soware
Aer a soware upgrade or to recover (occasionally) from an error condion, you must reboot the
soware. As with the shutdown command, you must reboot through a direct console connecon otherwise
you will not see the command output when the network goes down during the reboot process.
To reboot the soware:
1. Make sure you are in operaonal mode.
2. Enter the request system reboot command. This command displays the nal stages of the system
shutdown and executes the reboot. Reboot requests are recorded to the system log les, which you
can view with the show log messages command. For example:
user@host>request system rebootReboot the system? [yes,no] (no)yes
shutdown: [pid 845]
Shutdown NOW!
*** FINAL System shutdown message from root@host ***
System going down IMMEDIATELY
299

user@host> Dec 17 17:34:20 init: syslogd (PID 409) exited with status=0 Normal Exit
Waiting (max 60 seconds) for system process `bufdaemon' to stop...stopped
Waiting (max 60 seconds) for system process `syncer' to stop...stopped
syncing disks... 10 6
done
Uptime: 2m45s
ata0: resetting devices.. done
Rebooting...
CLI Comment Character # for Operaonal Mode Commands
The comment character enables you to copy operaonal mode commands that include comments from
a le and paste them into the CLI. A pound or hash symbol (#) at the beginning of the command line
indicates a comment line. This command is useful for describing frequently used operaonal mode
commands, such as a user’s work instrucons on how to monitor the network. To add a comment to a
command le, you must place # as the rst character of the line. When you start a command with #, the
operang system disregards the rest of the line.
NOTE: The device conguraon does not save the comments you enter in the CLI, whether
individually or by pasng in the contents of a conguraon le. Comments entered at the CLI are
ignored.
To add comments in operaonal mode, you start with a # and end with a new line (carriage return):
user@host> #
comment-string
comment-string
is the text of the comment. The comment text can be any length, but each comment line
must begin with a #.
300

Filtering Operaonal Command Output
IN THIS SECTION
About Using the Pipe ( | ) Symbol to Filter Command Output | 301
Example: Use Regular Expressions with the Pipe ( | ) Symbol to Filter Command Output | 303
Example: Pipe ( | ) Filter Funcons in the Command-Line Interface | 304
Filter Operaonal Mode Command Output in a QFabric System | 318
Use Suppress-Zero Filter with the Pipe ( | ) Symbol to Filter Zero Values in Command Output | 319
The pipe | symbol lets you (the network administrator) lter the command output in both operaonal
and conguraon modes.
About Using the Pipe ( | ) Symbol to Filter Command Output
You can lter command output by adding the pipe ( | ) symbol when you enter the command.
Example:
user@host> show rip neighbor ?
Possible completions:
<[Enter]> Execute this command
<name> Name of RIP neighbor
instance Name of RIP instance
logical-system Name of logical system, or 'all'
| Pipe through a command
The following example lists the lters that you can use with the pipe symbol ( | ):
user@host> show interfaces | ?
user@host> show interfaces | ?
Possible completions:
append Append output text to file
301

count Count occurrences
display Show additional kinds of information
except Show only text that does not match a pattern
find Search for first occurrence of pattern
hold Hold text without exiting the --More-- prompt
last Display end of output only
match Show only text that matches a pattern
no-more Don't paginate output
refresh Refresh a continuous display of the command
request Make system-level requests
resolve Resolve IP addresses
save Save output text to file
tee Write to standard output and file
trim Trim specified number of columns from start of line
For the show configuration command only, you can combine the pipe symbol and queson mark to display
an addional compare lter:
user@host> show configuration | ?
Possible completions:
compare Compare configuration changes with prior version
...
You can enter any of the pipe lters in combinaon. For example:
user@host>
command
| match
regular-expression
| save
filename
NOTE: This topic describes
only
the lters that you can use for
operaonal mode command
output.
302

Example: Use Regular Expressions with the Pipe ( | ) Symbol to Filter
Command Output
You use the except, find, and match lters with the pipe symbol to employ regular expressions to lter
output. Juniper Networks uses the regular expressions as dened in POSIX 1003.2. If a regular
expression contains spaces, operators, or wildcard characters, enclose the expression in quotaon
marks.
Table 16: Common Regular Expression Operators in Operaonal Mode Commands
Operator Funcon
|
Indicates that a match can be one of the two terms on either side of the pipe.
^
Used at the beginning of an expression to denote where a match should begin.
$
Used at the end of an expression to denote that a term must be matched exactly up to the point of
the $ character.
[ ]
Species a range of leers or digits to match. To separate the start and end of a range, use a hyphen
( - ).
( )
Species a group of terms to match.
For example, if a command produces the following output:
user@host> show chassis hardware
Hardware inventory:
Item Version Part number Serial number Description
Chassis F0632 MX80
Midplane REV 09 711-031594 ZW0568 MX80
PEM 0 Rev 04 740-028288 VK09886 AC Power Entry Module
Routing Engine BUILTIN BUILTIN Routing Engine
TFEB 0 BUILTIN BUILTIN Forwarding Engine Processor
QXM 0 REV 06 711-028408 ZW4288 MPC QXM
FPC 0 BUILTIN BUILTIN MPC BUILTIN
MIC 0 BUILTIN BUILTIN 4x 10GE XFP
PIC 0 BUILTIN BUILTIN 4x 10GE XFP
Xcvr 0 REV 02 740-014289 C825XU010 XFP-10G-SR
303

Xcvr 1 REV 03 740-014289 CB25BQ0WD XFP-10G-SR
Xcvr 2 REV 01 740-011571 C739XJ039 XFP-10G-SR
FPC 1 BUILTIN BUILTIN MPC BUILTIN
MIC 1 *** Hardware Not Supported ***
Fan Tray Fan Tray
A pipe lter of | match "FPC-1" displays the following output:
FPC 1 BUILTIN BUILTIN MPC BUILTIN
A pipe lter of | except "FPC 1" displays the following output:
Hardware inventory:
Item Version Part number Serial number Description
Chassis F0632 MX80
PEM 0 Rev 04 740-028288 VK09886 AC Power Entry Module
Routing Engine BUILTIN BUILTIN Routing Engine
TFEB 0 BUILTIN BUILTIN Forwarding Engine Processor
FPC 0 BUILTIN BUILTIN MPC BUILTIN
Fan Tray Fan Tray
Example: Pipe ( | ) Filter Funcons in the Command-Line Interface
IN THIS SECTION
Examples of Conguraons and Their Dierences in Text | 305
Examples of Conguraons and Their Dierences in XML | 307
Example of Counng the Number of Lines of Output | 308
Example of Output Displayed in XML Tag Format | 308
Example of Displaying Stac Conguraon Data | 308
Example of Displaying Ephemeral Conguraon Data | 309
Example of Displaying Output in JSON Format | 309
Example of Displaying the Conguraon with YANG Translaon Scripts Applied | 310
Example of Displaying the RPC Tags for a Command | 311
304

Example of Ignoring Output That Does Not Match a Regular Expression | 312
Example of Displaying Output from the First Match of a Regular Expression | 312
Example of Retaining Output Aer the Last Screen | 313
Example of Displaying Output Beginning with the Last Entries | 313
Example of Displaying Output That Matches a Regular Expression | 314
Example of Prevenng Output from Being Paginated | 314
Example of Sending Command Output to Other Users | 314
Example of Resolving IP Addresses | 315
Example of Saving Output to a File | 315
Example of Appending Output to a File | 316
Example of Displaying Output on Screen and Wring to a File | 316
Example of Trimming Output by Specifying the Starng Column | 317
Example of Refreshing the Output of a Command | 317
This topic describes and provides examples of the pipe ( | ) lter funcons that the Junos OS CLI
supports.
Examples of Conguraons and Their Dierences in Text
The compare lter compares the candidate conguraon with either the current commied conguraon
or a conguraon le. It also displays the dierences between the two conguraons with text
characters.
To compare conguraon les, you enter compare aer the pipe ( | ) symbol, as follows:
show | compare [rollback
n
|
filename
]
The rollback
n
variable is the index into the list of previously commied conguraons. The most
recently saved conguraon is 0. If you do not specify arguments, the candidate conguraon is
compared against the acve conguraon le (/cong/juniper.conf), which is the same as comparing to
rollback index 0.
The full path (or URL) to a conguraon le is
lename
.
The comparison output uses the following convenons:
305

• Statements that are in the candidate conguraon only are prexed with a plus sign (+).
• Statements that are in the comparison le only are prexed with a minus sign (–).
• Statements that are unchanged are prexed with a single blank space ( ).
Example:
user@host> show configuration system | compare rollback 9
[edit system]
+ host-name device;
+ backup-router 192.168.71.254;
- ports {
- console log-out-on-disconnect;
- }
[edit system name-server]
+ 172.17.28.11;
172.17.28.101 { ... }
[edit system name-server]
172.17.28.101 { ... }
+ 172.17.28.100;
+ 172.17.28.10;
[edit system]
- scripts {
- commit {
- allow-transients;
- }
- }
+ services {
+ ftp;
+ rlogin;
+ rsh;
+ telnet;
+ }
We have enhanced output from the show | compare command to more accurately reect conguraon
changes. This enhancement includes more intelligent handling of order changes in lists. For example,
consider group names that are reordered as follows:
groups {
groups {
group_xmp; group_xmp;
306

group_cmp; group_grp:
group_grp; group_cmp;
}
}
In early releases, output from the show | compare command looked like the following:
[edit groups]
- group_xmp;
- group_cmp;
- group_grp;
+ group_xmp;
+ group_grp;
+ group_cmp;
Now, output from the show | compare command looks like the following:
[edit groups]
group_xmp {...}
! group_grp {...}
Examples of Conguraons and Their Dierences in XML
The compare | display xml lter compares the candidate conguraon with the current commied
conguraon and displays the dierences between the two conguraons in XML. To compare
conguraons, you enter compare | display xml aer the pipe ( | ) symbol in either operaonal or
conguraon mode.
Example in operaonal mode:
user@host> show configuration | compare | display xml
Example in conguraon mode:
[edit]
user@host# show | compare | display xml
You can enter a specic conguraon hierarchy before using the | compare command. In conguraon
mode, you can navigate to a hierarchy where the command is applied.
307

Example of Counng the Number of Lines of Output
To count the number of lines in command output, enter count aer the pipe symbol ( | ). For example:
user@host> show configuration | count
Count: 269 lines
Example of Output Displayed in XML Tag Format
To display command output in XML tag format, you enter display xml aer the pipe symbol ( | ).
The following example displays the show cli directory command output as XML tags:
user@host> show cli directory | display xml
<rpc-reply xmlns:junos="http://xml.juniper.net/junos/7.5I0/junos">
<cli>
<working-directory>/var/home/user</working-directory>
</cli>
<cli>
<banner></banner>
</cli>
</rpc-reply>
If the conguraon data or command output contains characters that are outside of the 7-bit ASCII
character set, the CLI displays the equivalent UTF-8 decimal character reference for those characters in
the XML output.
Example of Displaying Stac Conguraon Data
You can view the inherited conguraon data and informaon about the source group from which the
conguraon has been inherited with respect to the stac conguraon database. To view this data, you
issue the show configuration | display inheritance command.
user@host> show configuration | display inheritance
## Last commit: 2018-03-29 15:54:17 PDT
version 16.2R2;
system {
...
}
308

Example of Displaying Ephemeral Conguraon Data
Juniper Extension Toolkit (JET) applicaons, Network Conguraon Protocol (NETCONF), and Junos
XML protocol client applicaons can congure the ephemeral conguraon database. The ephemeral
database is an alternate conguraon database that provides a fast programmac interface for
performing conguraon updates.
To view the complete post-inheritance conguraon merged with the conguraon data in all instances
of the ephemeral database, use the show ephemeral-configuration merge command.
user@host> show ephemeral-configuration merge
## Last changed: 2019-02-01 09:47:20 PST
version 18.2R1;
system {
...
}
Example of Displaying Output in JSON Format
You can display the conguraon or command output in JavaScript Object Notaon (JSON) format by
entering display json aer the pipe symbol ( | ).
The following example displays the show cli directory command output in JSON format:
user@host> show cli directory | display json
{
"cli" : [
{
"working-directory" : [
{
"data" : "/var/home/username"
}
]
}
]
}
If the operaonal command output contains characters that are outside of the 7-bit ASCII character set,
the CLI displays the equivalent UTF-8 decimal character reference for those characters in the JSON
output.
309

Example of Displaying the Conguraon with YANG Translaon Scripts Applied
You can load YANG modules onto devices running Junos OS to augment the conguraon hierarchy
with data models that Junos OS does not support navely. Junos OS does support translaon of these
models.. The acve conguraons and candidate conguraons contain the conguraon data for non-
nave YANG data models in the syntax dened by that model. These conguraons do not explicitly
display the corresponding translated Junos OS syntax, which is commied as a transient change.
The | display translation-scripts lter displays the complete post-inheritance conguraon, with the
translated conguraon data from all enabled translaon scripts explicitly included in the output. To
display the conguraon with all enabled YANG translaon scripts applied, append the | display
translation-scripts lter to the show configuration command in operaonal mode or the show command in
conguraon mode. For example:
user@host> show configuration | display translation-scripts
To view just the non-nave conguraon data aer translaon, you use the | display translation-
scripts translated-config lter in either operaonal mode or conguraon mode.
user@host> show configuration | display translation-scripts translated-config
In conguraon mode, you can display just the conguraon dierences in the hierarchies
corresponding to non-nave YANG data models before or aer translaon scripts are applied. To display
those dierences, you append the configured-delta or translated-delta keyword, respecvely, to the show |
display translation-scripts command. In both cases, the XML output displays the deleted conguraon
data, followed by the new conguraon data.
user@host# show | display-translation-scripts (configured-delta | translated-delta)
The following example displays a sample conguraon with and without translaon scripts applied. The
show command displays the conguraon, which includes the non-nave conguraon data in the syntax
that the YANG data model denes. The | display translation-scripts lter displays the non-nave
conguraon data in both the syntax dened by the YANG data model and the translated Junos OS
syntax. Both commands display the enre conguraon, which has been truncated for brevity in this
example. However, the show command returns the pre-inhertance conguraon, whereas the show |
display translation-scripts command returns the post-inheritance conguraon.
user@host# show
...
myint:intconfig {
310

interfaces {
interface ge-0/0/0 {
config {
description test;
}
}
}
}
...
user@host# show | display translation-scripts
...
interfaces {
ge-0/0/0 {
description test;
gigether-options {
no-flow-control;
}
}
}
...
myint:intconfig {
interfaces {
interface ge-0/0/0 {
config {
description test;
}
}
}
}
...
Example of Displaying the RPC Tags for a Command
To display the remote procedure call (RPC) XML tags for an
operaonal mode command
, you enter
display xml rpc aer the pipe symbol ( | ).
311

The following example displays the RPC tags for the show route command:
user@host> show route | display xml rpc
<rpc-reply xmlns:junos="http://xml.juniper.net/junos/10.1I0/junos">
<rpc>
<get-route-information>
</get-route-information>
</rpc>
<cli>
<banner></banner>
</cli>
</rpc-reply>
Example of Ignoring Output That Does Not Match a Regular Expression
To ignore text that matches a regular expression, specify the except command aer the pipe symbol ( | ).
If the regular expression contains any spaces, operators, or wildcard characters, enclose it in quotaon
marks.
The following example displays all users who are logged in to the router, except for the user root:
user@host> show system users | except root
8:28PM up 1 day, 13:59, 2 users, load averages: 0.01, 0.01, 0.00
USER TTY FROM LOGIN@ IDLE WHAT
user p0 device1.example.com 7:25PM - cli
Example of Displaying Output from the First Match of a Regular Expression
To display output starng with the rst occurrence of text matching a regular expression, you enter find
aer the pipe symbol ( | ). If the regular expression contains any spaces, operators, or wildcard
characters, enclose it in quotaon marks.
The following example displays the routes in the roung table starng at IP address 208.197.169.0:
user@host> show route | find 208.197.169.0
208.197.169.0/24 *[Static/5] 1d 13:22:11
> to 192.168.4.254 via so-3/0/0.0
224.0.0.5/32 *[OSPF/10] 1d 13:22:12, metric 1
iso.0: 1 destinations, 1 routes (1 active, 0 holddown, 0 hidden)
+ = Active Route, - = Last Active, * = Both
312

47.0005.80ff.f800.0000.0108.0001.1921.6800.4015.00/160
*[Direct/0] 1d 13:22:12
> via lo0.0
The following example displays the rst CCC entry in the forwarding table:
user@host> show route forwarding-table | find ccc
Routing table: ccc
MPLS:
Interface.Label Type RtRef Nexthop Type Index NhRef Netif
default perm 0 rjct 3 1
0 user 0 recv 5 2
1 user 0 recv 5 2
32769 user 0 ucst 45 1 fe-0/0/0.534
fe-0/0/0. (CCC) user 0 indr 44 2
10.0.16.2 Push 32768, Push
Example of Retaining Output Aer the Last Screen
You can retain output and scroll or search through it by holding rather than returning immediately to the
CLI prompt aer viewing the last screen of output. To retain output, you enter hold aer the pipe symbol
( | ). The following example prevents returning to the CLI prompt aer you have viewed the last screen
of output from the show log log-file-1 command:
user@host> show log log-file-1 | hold
Example of Displaying Output Beginning with the Last Entries
You can view log les in which the end of the le contains the most recent entries. To display text
starng from the end of the output, you enter last <
lines
> aer the pipe symbol ( | ).
The following example displays the last entries in log-le-1 le:
user@host> show log log-file-1 | last
NOTE: When the number of lines requested is less than the number of lines that the screen
length seng permits you to display, the system returns a subset. The system returns as many
313

lines as permied by the screen length seng. That is, if your screen length is set to 20 lines and
you have requested only the last 10 lines, the system returns the last 19 lines instead of the last
10 lines.
Example of Displaying Output That Matches a Regular Expression
To display output that matches a regular expression, you enter match
regular-expression
aer the pipe
symbol ( | ). If the regular expression contains any spaces, operators, or wildcard characters, enclose it in
quotaon marks.
The following example matches all the Asynchronous Transfer Mode (ATM) interfaces in the
conguraon:
user@host> show configuration | match at-
at-2/1/0 {
at-2/1/1 {
at-2/2/0 {
at-5/2/0 {
at-5/3/0 {
Example of Prevenng Output from Being Paginated
By default, if output is longer than the length of the terminal screen, you receive a ---(more)--- message
to display the remaining output. To display the remaining output, you press Space.
To prevent the output from being paginated, you enter no-more aer the pipe symbol ( | ).
The following example displays output from the show configuration command all at once:
user@host> show configuration | no-more
This feature is useful if you want to copy the enre output and paste it into an email message.
Example of Sending Command Output to Other Users
To display command output on the terminal of a specic user logged in to your router, or on the
terminals of all users logged in to your router, you enter request message (all | user
account
@
terminal
) aer
the pipe symbol ( | ).
314

If you are troubleshoong your router and talking with a customer service representave on the phone,
you can share the command output. You use the request message command to send your representave
the command output you are currently viewing on your terminal.
The following example sends the output from the show interfaces command that you enter on your
terminal to the terminal of the user root@ttyp1:
user@host> show interfaces | request message user root@ttyp1
The user root@ttyp1 sees the following output appear on the terminal screen:
Message from user@host on /dev/ttyp0 at 10:32 PST...
Physical interface: dsc, Enabled, Physical link is Up
Interface index: 5, SNMP ifIndex: 5
Type: Software-Pseudo, MTU: Unlimited...
Example of Resolving IP Addresses
In operaonal mode only, if the output of a command displays an unresolved IP address, you can enter |
resolve aer the command to display the name associated with the IP address. The resolve lter enables
the system to perform a reverse DNS lookup of the IP address. If DNS is not enabled, the lookup fails
and no substuon is performed.
To perform a reverse DNS lookup of an unresolved IP address, you enter resolve <full-names> aer the
pipe symbol ( | ). If you do not specify the full-names opon, the name is truncated to t whatever eld
width limitaons apply to the IP address.
The following example performs a DNS lookup on any unresolved IP addresses in the output from the
show ospf neighbors command:
user@host> show ospf neighbors | resolve
Example of Saving Output to a File
When command output is lengthy, when you need to store or analyze the output, or when you need to
send the output in an e-mail message or by FTP, you can save the output to a le. By default, the le is
placed in your home directory on the router.
To save command output to a le, you enter save
filename
aer the pipe symbol ( | ).
315

The following example saves the output from the request support information command to a le named
my-support-info.txt:
user@host> request support information | save my-support-info.txt
Wrote 1143 lines of output to ‘my-support-info.txt’
Example of Appending Output to a File
When command output is displayed, you can either save the output to a le, which overwrites the
exisng contents of that le, or you can append the output text to a specic le.
To append the command output to the le, you enter append
filename
aer the pipe symbol ( | ).
The following example appends the output from the request support information command to a le named
my-support-info.txt:
user@host> request support information | append my-support-info.txt
Wrote 2247 lines of output to 'my-support-info.txt'
Example of Displaying Output on Screen and Wring to a File
When command output is displayed, you can also write the output to a le. To both display the output
and write it to a le, you enter tee
filename
aer the pipe symbol (|).
The following example displays the output from the show interfaces ge-* terse command (displaying
informaon about the status of the Gigabit Ethernet interfaces on the device) and diverts the output to
a le called ge-interfaces.txt:
user@host> show interfaces ge-* terse | tee ge-interfaces.txt
Interface Admin Link Proto Local Remote
ge-0/1/0 up down
ge-0/1/1 up up
ge-0/1/2 up down
ge-0/1/3 up up
316

Unlike the UNIX tee command, only an error message is displayed if the le cannot be opened (instead
of displaying the output and then the error message).
user@host> show interfaces ge-* terse | tee /home/user/test.txt
error: tee failed: file /home/user/test.txt could not be opened
user@host>
Example of Trimming Output by Specifying the Starng Column
Output appears on the terminal screen in terms of rows and columns. The rst alphanumeric character
starng at the le of the screen is in column 1, the second character is in column 2, and so on. To display
output starng from a specic column (thus trimming the lemost poron of the output), you enter trim
columns aer the pipe symbol ( | ). The trim lter is useful for trimming the date and me from the
beginning of system log messages.
The following example displays output from the show system storage command, ltering out the rst 10
columns:
user@host> show system storage | trim 11
NOTE: The trim command does not accept negave values.
Example of Refreshing the Output of a Command
You can run an operaonal mode command with the | refresh pipe opon to refresh the output
displayed on the screen periodically. The default refresh occurs every second. However, you can also
explicitly specify a refresh interval from 1 through 604,800 seconds. For example, to refresh the output
of the show interfaces command every 5 seconds, you run the following command:
user@host> show interfaces | refresh 5
317

Filter Operaonal Mode Command Output in a QFabric System
When you issue an operaonal mode command in a QFabric system, the output generated can be fairly
extensive because of the number of components contained within the system. To make the output more
accessible, you can lter the output by appending the | filter opon to the end of most commands.
1. To lter operaonal mode command output and limit it to a Node group, include the | filter node-
group
node-group-name
opon at the end of your operaonal mode command. For example:
root@qfabric> show interfaces terse | filter node-group NW-NG-0
Interface Admin Link Proto Local Remote
NW-NG-0:dsc up up
NW-NG-0:em0 up up
NW-NG-0:em1 up up
NW-NG-0:gre up up
NW-NG-0:ipip up up
NW-NG-0:lo0 up up
NW-NG-0:lo0.16384 up up inet 127.0.0.1 --> 0/0
NW-NG-0:lo0.16385 up up inet
NW-NG-0:lsi up up
NW-NG-0:mtun up up
NW-NG-0:pimd up up
NW-NG-0:pime up up
NW-NG-0:tap up up
Node01:ge-0/0/10 up up
Node01:ge-0/0/40 up up
Node01:ge-0/0/41 up up
vlan up up
2. To lter operaonal mode command output and limit it to a set of Node groups, include the | filter
node-group opon at the end of your operaonal mode command and specify the list of Node group
names in brackets. For example:
root@qfabric> show ethernet-switching interfaces | filter node-group [NW-NG-0 RSNG-1]
Interface State VLAN members Tag Tagging Blocking
NW-NG-0:ae0.0 up v200 200 tagged unblocked
v50 50 tagged unblocked
v51 51 tagged unblocked
v52 52 tagged unblocked
v53 53 tagged unblocked
318

RSNG-1:ae0.0 up v200 200 untagged unblocked
RSNG-1:ae47.0 up v50 50 tagged unblocked
v51 51 tagged unblocked
v52 52 tagged unblocked
v53 53 tagged unblocked
Use Suppress-Zero Filter with the Pipe ( | ) Symbol to Filter Zero Values in
Command Output
Junos OS supports suppress-zero lter to exclude lines with ‘0' values for any of the elds in given line.
This feature is available for all the operaonal show commands. For show commands CLI output, lines
with ‘0’ values output can be masked. The output lines with non-zero values are displayed. You can use
this to mask zero counters’ values. If a line has non-zero values along with ‘0’ values in a line, it is not
masked. If ‘0’ appears in descripon or string eld, it is not masked and is emied in the CLI output.
NOTE: This feature is applicable for CLI operaonal commands only. The suppress-zeros lter is
not applicable for commands that don't use rendering. For example, show configuration, traceroute,
ping and other monitor commands.
Here are a few examples for the show commands with suppress-zeroes lter:
• For example, if a command produces the following output:
user@host> show interfaces vtep
Physical interface: vtep, Enabled, Physical link is Up
Interface index: 133, SNMP ifIndex: 517
Type: Software-Pseudo, Link-level type: VxLAN-Tunnel-Endpoint, MTU: Unlimited, Speed:
Unlimited
Device flags : Present Running
Interface flags: SNMP-Traps
Link type : Full-Duplex
Link flags : None
Last flapped : Never
Input packets : 0
Output packets: 0
319

A pipe lter of | suppress-zeros displays the following output:
user@host> show interfaces vtep | suppress-zeros
Physical interface: vtep, Enabled, Physical link is Up
Interface index: 133, SNMP ifIndex: 517
Type: Software-Pseudo, Link-level type: VxLAN-Tunnel-Endpoint, MTU: Unlimited, Speed:
Unlimited
Device flags : Present Running
Interface flags: SNMP-Traps
Link type : Full-Duplex
Link flags : None
Last flapped : Never
In this example, the Input packets and Output packets elds are masked as these elds contain ‘0’
integer values.
• If a command produces the following output:
user@host> show interfaces fxp0
Physical interface: fxp0, Enabled, Physical link is Up
Interface index: 8, SNMP ifIndex: 1
Description: 0
Type: Ethernet, Link-level type: Ethernet, MTU: 1514, Speed: 1000mbps
Device flags : Present Running
Interface Specific flags: Internal: 0x100000
Interface flags: SNMP-Traps
Link type : Full-Duplex
Link flags : 0x4
Current address: 54:04:0a:dd:85:8d, Hardware address: 54:04:0a:dd:85:8d
Last flapped : 2023-11-15 19:02:00 IST (21:40:35 ago)
Input packets : 1530766
Output packets: 13469
Logical interface fxp0.0 (Index 5) (SNMP ifIndex 13)
Flags: Up SNMP-Traps 0x4000000 Encapsulation: ENET2
Input packets : 1528251
Output packets: 13481
Protocol inet, MTU: 1500
Max nh cache: 75000, New hold nh limit: 75000, Curr nh cnt: 186, Curr new hold cnt: 0, NH
drop cnt: 0
Flags: Sendbcast-pkt-to-re, Is-Primary
320

Addresses, Flags: Is-Preferred Is-Primary
Destination: 10.221.128/18, Local: 10.221.133.141, Broadcast: 10.221.191.255
A pipe lter of | suppress-zeros displays the following output:
user@host> show interfaces fxp0 | suppress-zeros
Physical interface: fxp0, Enabled, Physical link is Up
Interface index: 8, SNMP ifIndex: 1
Description: 0
Type: Ethernet, Link-level type: Ethernet, MTU: 1514, Speed: 1000mbps
Device flags : Present Running
Interface Specific flags: Internal: 0x100000
Interface flags: SNMP-Traps
Link type : Full-Duplex
Link flags : 0x4
Current address: 54:04:0a:dd:85:8d, Hardware address: 54:04:0a:dd:85:8d
Last flapped : 2023-11-15 19:02:00 IST (21:40:35 ago)
Input packets : 1530766
Output packets: 13469
Logical interface fxp0.0 (Index 5) (SNMP ifIndex 13)
Flags: Up SNMP-Traps 0x4000000 Encapsulation: ENET2
Input packets : 1528251
Output packets: 13481
Protocol inet, MTU: 1500
Max nh cache: 75000, New hold nh limit: 75000, Curr nh cnt: 186, Curr new hold cnt: 0, NH
drop cnt: 0
Flags: Sendbcast-pkt-to-re, Is-Primary
Addresses, Flags: Is-Preferred Is-Primary
Destination: 10.221.128/18, Local: 10.221.133.141, Broadcast: 10.221.191.255
In this example, the Description eld is not masked in the output as it is a string type and is a non-
integer. The Max nh cache: 75000, New hold nh limit: 75000, Curr nh cnt: 186, Curr new hold cnt: 0, NH drop
cnt: 0 line is not masked as it contains non-zero integer counter values in it.
Change History Table
321

Feature support is determined by the plaorm and release you are using. Use Feature Explorer to
determine if a feature is supported on your plaorm.
Release Descripon
18.2R1 In Junos OS Release 18.1 and earlier, to view the complete post-inheritance conguraon merged with
the conguraon data in all instances of the ephemeral conguraon database, use the show ephemeral-
configuration | display merge command. Starng in Junos OS Release 18.2R1, the display merge opon
is deprecated.
17.3R1 Starng in Junos OS Release 17.3R1, OpenCong supports the operaonal state emied by daemons
directly in JSON format in addion to XML format. To congure JSON compact format, use the
command set system export-format state-data json compact. This command converts XML format to
compact JSON format. Else, it emits the JSON in non-compact format.
16.2R2
Starng in Junos OS Release 16.2R2, the show | compare | display xml command omits the
<configuration> tag in the XML output if the comparison returns no dierences or if the comparison
returns only dierences for non-nave conguraon data, for example, conguraon data associated
with an OpenCong data model.
16.2R2
Starng in Junos OS Release 16.2R2, the show | compare | display xml command omits the
<configuration> tag in the XML output if the comparison returns no dierences or if the comparison
returns only dierences for non-nave conguraon data, for example, conguraon data associated
with an OpenCong data model.
16.1 Starng in Junos OS Release 16.1, devices running Junos OS emit JSON-formaed conguraon data
using a new default implementaon for serializaon.
16.1 Starng in Junos OS Release 16.1, you can load YANG modules onto devices running Junos OS to
augment the conguraon hierarchy with data models that are not navely supported by Junos OS but
can be supported by translaon. The acve and candidate conguraons contain the conguraon data
for non-nave YANG data models in the syntax dened by that model, but they do not explicitly display
the corresponding translated Junos OS syntax, which is commied as a transient change.
14.2 Starng in Junos OS Release 14.2, you can display the conguraon or command output in JavaScript
Object Notaon (JSON) format by entering display json aer the pipe symbol ( | ).
8.3
Starng with Junos OS Release 8.3, output from the show | compare command has been enhanced to
more accurately reect conguraon changes. This includes more intelligent handling of order changes
in lists.
322
Junos CLI Reference Overview
We've consolidated all Junos CLI commands and conguraon statements in one place. Learn about the
syntax and opons that make up the statements and commands and understand the contexts in which
you’ll use these CLI elements in your network conguraons and operaons.
• Junos CLI Reference
Click the links to access Junos OS and Junos OS Evolved conguraon statement and command
summary topics.
• Conguraon Statements
• Operaonal Commands
324





